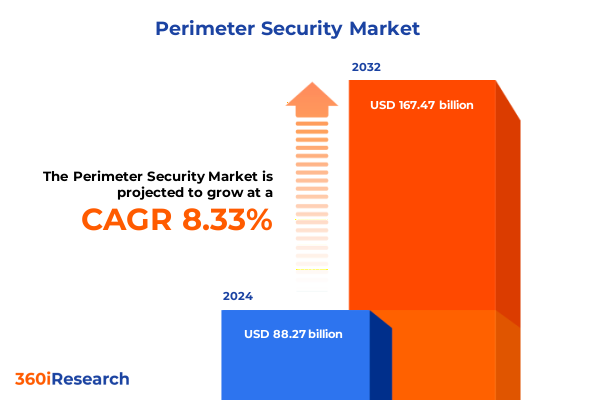
The Perimeter Security Market size was estimated at USD 95.50 billion in 2025 and expected to reach USD 103.33 billion in 2026, at a CAGR of 8.35% to reach USD 167.47 billion by 2032.
An authoritative introduction that positions perimeter security leaders to integrate regulatory, supply chain and technological shifts into procurement and deployment decisions
The perimeter security sector sits at the intersection of technology, infrastructure and public policy, and this executive summary synthesizes the forces reshaping procurement, deployment and supplier strategy across that intersection. This introduction frames why perimeter security decision-makers must reorient priorities from product selection alone to an integrated view that includes regulatory risk, component sourcing, distribution resilience and the lifecycle economics of systems that increasingly combine optical, electronic and software-driven technologies. As organizations contend with heightened geopolitical friction, shifting trade regimes and rapid adoption of AI-enabled analytics, the traditional separation between physical and logical security is dissolving in practice, forcing security architects and procurement leaders to coordinate more closely than ever with legal, supply chain and IT stakeholders.
Moving from context to purpose, this section clarifies the intent of the broader study: to deliver a concise, operationally focused compass for executives who must prioritize capital, procurement and partner selection under deepening policy uncertainty. The following pages translate segmentation-driven insights-spanning product types such as access control, fencing, intrusion detection, security lighting and video surveillance; diverse end users from commercial to government and industrial buyers; components ranging from hardware and software to services; varied deployment models including cloud and on-premises; and distribution routes through both direct and indirect channels-into clear signals for immediate action. In short, this introduction grounds readers in the practical implications of the market dynamics explored in the full report and sets expectations for how to use the insights to inform near-term decisions and medium-term strategic planning.
Transformative shifts in perimeter security driven by sensor fusion, regulatory tightening, and service-centric commercial models that change competitive advantage
The landscape for perimeter security is undergoing transformative shifts driven by three converging dynamics: accelerated technology adoption, intensified regulatory scrutiny, and strategic supply-chain reconfiguration. First, the proliferation of sensor fusion-where video surveillance, intrusion detection sensors, and access control platforms share telemetry-has elevated the value of systems that can ingest heterogeneous data and deliver reliable operational alerts. Adoption of biometric modalities such as facial recognition, fingerprint and iris scanning is increasing in controlled environments, which in turn raises expectations for interoperability between access control hardware and advanced analytics. Second, regulators and standards bodies are tightening the compliance perimeter. Governments and public agencies are establishing stricter procurement rules, export and import controls, and prohibitions tied to national security considerations, which affects equipment provenance and the vendors eligible for public contracts. Third, commercial and industrial buyers are pressing vendors for robust lifecycle services-consulting, installation and maintenance support-that reduce integration risk and ensure long-term resilience.
These changes compel manufacturers and integrators to rethink product roadmaps and commercial models. Vendors that historically competed on hardware features must now demonstrate secure software lifecycles, transparent supply chains and scalable service offerings. Meanwhile, channel partners-distributors, system integrators and value-added resellers-are shifting from transactional resale into consultative roles that bridge procurement and technical implementation. As a result, leaders should expect competitive advantage to accrue to organizations that can combine secure, modular hardware platforms with cloud or hybrid deployment options and sophisticated video management and analytics software. In short, the market is favoring ecosystem players able to deliver integrated solutions that reduce operational friction for end users while navigating a more constrained and politically sensitive sourcing environment.
Cumulative operational consequences of 2025 U.S. tariff and trade actions on perimeter security sourcing, materials costs, and supplier eligibility across public and private procurement
United States tariff actions in 2025 have created a cumulative operational effect on perimeter security supply chains, procurement strategies and total cost of ownership calculations for hardware-intensive solutions. During the last statutory review cycle, Section 301 actions culminated in tariff adjustments affecting key upstream materials and components, including increases on items such as polysilicon and related semiconductor inputs that are critical for imaging sensors and other electronic modules; those changes came into effect at the start of 2025 and altered sourcing calculus for many manufacturers. This action, taken to blunt certain foreign industrial practices, has directly pressured suppliers that rely on specialized wafers and component-level imports, creating an incentive to accelerate alternative sourcing or reconfigure product BOMs (bills of materials) to reduce exposure to tariffed inputs. The result is a near-term scramble to prioritize longer lead-time sourcing contracts, adjust inventory policy, and examine qualification processes for new suppliers to preserve delivery SLAs and contractual commitments.
Concurrently, tariff policy addressing steel and aluminum has introduced material-cost volatility for metal-intensive components such as camera housings, mounting hardware, fencing systems and lamp enclosures. Executive determinations that raised tariff rates on these categories during 2025 have increased the marginal cost of physical components and raised the premium on domestically sourced or “melt-and-pour” certified materials, prompting integrators and manufacturers to reassess manufacturing footprints and vendor contracts. These changes have spurred near-term decisions to seek qualified domestic mill sources, negotiate pass-through clauses in supply agreements, and consider design substitutions where feasible to mitigate price pressure while maintaining structural integrity and compliance.
Finally, the regulatory environment surrounding covered communications equipment and certain foreign-made surveillance devices has constrained the universe of acceptable suppliers for many public-sector and government tenders. Bans and restricted-authority designations have had the combined effect of reducing access to several low-cost vendors that previously competed heavily on price, thereby increasing demand for qualified alternative suppliers and certified test laboratories. This supply narrowing, together with tariff-driven cost pressure and the geopolitical impetus to diversify away from single-country dependence, has increased the strategic importance of nearshoring and re-shoring conversations. Companies are therefore investing in dual-sourcing strategies and diversifying manufacturing between Southeast Asia, Mexico and domestic sites to maintain supply continuity and satisfy procurement rules for critical installations. Evidence of diversified manufacturing footprints among major contract manufacturers underscores this shift toward “China plus” approaches to mitigate tariff and regulatory risk.
Segmentation-driven insights that translate product types, end-user priorities, component roles, deployment choices and distribution routes into strategic procurement and product decisions
Segmentation analysis reveals how exposure and opportunity vary across product types, end users, components, deployment models and distribution channels, informing tailored strategies for each market slice. When evaluated by product type-access control, fencing, intrusion detection, security lighting and video surveillance-differentiated exposure becomes apparent: access control systems that embed biometric modalities such as facial recognition, fingerprint and iris scanners rely on both specialized sensors and analytics software; video surveillance lines depend on imaging sensors that tie back to wafer and semiconductor availability; fencing and heavy-duty physical barriers are more sensitive to steel and aluminum costs; intrusion detection modalities such as infrared, microwave, radar and vibration sensors require bespoke sensor components and can be impacted by both metal and semiconductor price movements; security lighting alternatives show contrasts between legacy halogen architectures and increasingly favored LED solutions; and within video surveillance, analog cameras continue to serve cost-constrained use cases while IP camera platforms-both wired and wireless-drive security system modernization. This product-focused differentiation helps procurement teams prioritize mitigation levers relevant to the dominant cost drivers in each category.
End-user segmentation further refines strategy. Commercial buyers, including banking, retail and telecommunications, often prioritize integration with corporate IT and analytics services and are prepared to invest in managed services to reduce operational complexity, while government buyers across defense, education and transportation emphasize provenance, compliance and long-term maintenance contracts. Industrial and residential customers each present unique purchasing dynamics: industrial buyers require ruggedized, standards-compliant hardware and predictable lifecycle services, whereas residential purchasing is often price sensitive and influenced by indirect distribution channels. Component segmentation-hardware, services and software-reveals where margin and control accrue, with hardware comprising cameras, controllers and sensors; services extending from consulting through installation to maintenance support; and software spanning access control platforms, analytics and video management systems. The software and services layers offer durable differentiation and recurring revenue opportunities, while hardware remains the locus of immediate tariff and material exposure. Finally, deployment and distribution lenses underscore the strategic choice between cloud, hybrid and on-premises models, and between direct sales and channel-driven indirect routes through distributors, system integrators and value-added resellers, each of which requires distinct contractual and certification approaches to satisfy buyer risk profiles.
This comprehensive research report categorizes the Perimeter Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Product Type
- Component
- End User
- Deployment
- Distribution Channel
Key regional dynamics across the Americas, Europe Middle East & Africa, and Asia-Pacific that determine procurement, sourcing and compliance strategies for perimeter security programs
Regional dynamics materially shape strategy and risk for perimeter security programs, and leaders must align sourcing, partner selection and deployment models to regional policy and supply-chain realities. In the Americas, procurement teams contend with renewed emphasis on domestic sourcing for metal-intensive components, heightened scrutiny of supplier provenance for public tenders, and a robust private market where managed services are maturing. The United States federal and state procurement ecosystems increasingly require compliance with covered-equipment rules, which affects vendor eligibility and amplifies demand for certified local integrators and service partners. Moving eastward, Europe, the Middle East and Africa present a patchwork of regulatory postures: several European jurisdictions have adopted restrictive procurement positions regarding specific foreign surveillance vendors and enforce strict data-protection regimes that shape analytics adoption, while Middle Eastern markets are accelerating investment in advanced perimeter systems for strategic infrastructure and transportation projects. Africa’s market is heterogeneous, with pockets of rapid urbanization driving demand for cost-effective surveillance and access control but with supply-chain constraints that favor regional distribution partners.
Asia-Pacific remains a dual narrative of robust manufacturing capacity and evolving regulatory friction. The region hosts substantial electronics and sensor manufacturing ecosystems that serve global demand, yet geopolitical pressures and export control policies have encouraged manufacturers to diversify production across Southeast Asia and into Mexico or nearshore facilities to reduce tariff exposure and satisfy purchasing rules. Within each region, channel structures-ranging from direct OEM relationships in some large infrastructure projects to deeply entrenched indirect channels in commercial and residential segments-determine how quickly new compliance demands and material-cost changes propagate to end users. Taken together, regional insights compel executives to adopt localization or nearshoring strategies where feasible, partner with qualified local integrators for compliance-sensitive contracts, and adjust procurement terms to reflect variant regulatory and cost environments across the Americas, Europe, Middle East & Africa, and Asia-Pacific.
This comprehensive research report examines key regions that drive the evolution of the Perimeter Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Key company-level insights showing how hardware-software-service integration, certified channel partnerships, and supply resilience drive competitive advantage
Competitive and supplier landscapes in perimeter security are shaped by product specialization, vertical focus and the capacity to support certified services and lifecycle commitments. Leading vendors that combine robust hardware portfolios with mature software stacks and repeatable service models enjoy preferential procurement status among large commercial and government buyers who prize integration and continuity. At the same time, regional manufacturers and system integrators provide competitive on-the-ground execution capabilities-especially important when procurement rules favor domestic sourcing or certified local participation. The expanding bar on covered communications equipment and related national security designations has pruned the pool of eligible manufacturers for certain public tenders, thereby creating openings for certified alternative vendors and local champions.
Channel partners-distributors, system integrators and value-added resellers-play an increasingly determinative role in customer selection because they absorb integration risk, provide warranties and deliver maintenance support that end users require. For many vendors, establishing long-term service agreements and training certification programs for channel partners is a pragmatic route to sustain market access. Meanwhile, software and analytics providers that can demonstrate secure development practices, transparent data governance and interoperability with a wide array of access control and video management systems capture recurring revenue opportunities and reduce customer churn. For procurement teams, understanding which suppliers offer full-lifecycle support and certified compliance documentation is now as important as assessing feature lists, and for investors, the companies that successfully stitch hardware, software and services into a trusted ecosystem are likely to command premium valuations over time.
This comprehensive research report delivers an in-depth overview of the principal market players in the Perimeter Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- ABB Ltd.
- Advanced Perimeter Systems Limited
- AJAX SYSTEMS CH
- ASSA ABLOY AB
- Axis AB
- Bandweaver
- Canon Inc.
- Cias Elettronica Srl
- DEA Security S.r.l.
- Gallagher Group Limited
- Genetec Inc.
- Hangzhou Hikvision Digital Technology Co., Ltd.
- Honeywell International Inc.
- Johnson Controls International plc
- Magos Systems
- Motorola Solutions, Inc.
- Perimeter Protection Group
- Ring LLC by Amazon.com, Inc.
- Robert Bosch GmbH
- Schneider Electric SE
- SensoGuard Ltd.
- Siemens AG
- Tenable, Inc.
- Vicon Industries, Inc
- Zhejiang Dahua Technology Co., Ltd.
Actionable recommendations for industry leaders to mitigate tariff and regulatory risk while building modular product and service-led competitive positions
Given the convergence of tariff pressure, regulatory tightening and rapid technological change, industry leaders should adopt a set of immediate and medium-term actions to preserve project continuity and competitive positioning. In the immediate term, organizations should implement supplier risk audits that assess tariff exposure, materials provenance and eligibility under national procurement rules. These audits must extend beyond high-level vendor names to include tier-two suppliers for components such as imaging sensors, controllers and metal subcomponents. Next, negotiate flexible contracting language that allows for cost pass-throughs on unavoidable tariff increases, clear lead-time windows and rights to qualify alternate suppliers without onerous penalties. Transition plans should prioritize dual sourcing for critical items, and where practical, engage contract manufacturers or regional partners to create buffer capacity while new supplier qualifications are completed.
For the medium term, invest in modular product architectures that reduce dependency on single-source chips or materials, and pursue software-driven differentiation-analytics, video management and access control platforms-that deliver recurring revenue and soften hardware margin pressure. Strengthen certification and compliance capabilities through third-party testing and documented secure development lifecycles to maintain eligibility for public contracts and to reassure risk-averse commercial buyers. Finally, cultivate closer collaboration with channel partners by offering training, financial incentives for stocking certified components, and service-level agreements that align incentives across the value chain. By combining near-term tactical measures with medium-term strategic investments, industry leaders can transform tariff and regulatory headwinds into an opportunity to consolidate trust, increase margin resilience, and capture premium positions in compliance-sensitive segments.
Methodology describing the triangulation of primary interviews, supply-chain trace analysis, and regulatory review used to derive practical segmentation and regional insights
The research methodology underpinning these insights blends primary stakeholder interviews, supply-chain trace analysis, and a structured review of public policy actions and regulatory announcements. Primary input was collected through confidential interviews with procurement leaders, systems integrators and hardware manufacturers to surface practical procurement friction points, vendor qualification hurdles and contract language that currently governs critical projects. To validate supplier and component risk, the study cross-referenced public tariff announcements, executive proclamations and agency determinations with observable shifts in manufacturing footprints and investment patterns sourced from reputable news and government releases. This triangulation provides a robust view of how policy changes translate into operational outcomes across tiers of the supply chain.
Analytically, segmentation logic was applied across product types, end-user categories, component roles, deployment models and distribution channels to ensure insights map to actionable decision levers. Each segment was assessed for exposure to regulatory constraints, materials intensity, software dependency and lifecycle service needs. Finally, regional sensitivity analysis considered procurement rules, local manufacturing capacity and partner ecosystems to produce practical recommendations that align with procurement cycles and contract durations. Where primary data was limited due to commercial sensitivity, the methodology defaults to conservative assumptions and recommends targeted follow-up due diligence for organizations considering large capital programs.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Perimeter Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Perimeter Security Market, by Product Type
- Perimeter Security Market, by Component
- Perimeter Security Market, by End User
- Perimeter Security Market, by Deployment
- Perimeter Security Market, by Distribution Channel
- Perimeter Security Market, by Region
- Perimeter Security Market, by Group
- Perimeter Security Market, by Country
- United States Perimeter Security Market
- China Perimeter Security Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 3180 ]
A concise conclusion emphasizing strategic prioritization of compliance, supply resilience, modular design and service-led differentiation to navigate 2025 complexities
In conclusion, perimeter security leaders face a landscape in which technology advancement, trade policy and procurement standards are tightly interwoven. The practical effect of 2025 trade actions and regulatory clarifications is not merely transient price pressure; rather, they accelerate structural decisions about where and how systems are manufactured, who qualifies to supply critical projects, and which architectures will remain supportable over multiyear lifecycles. Organizations that proactively audit supplier exposure, adopt modular product designs, and redirect investment toward software and service capabilities will be better positioned to preserve continuity of service and capture value as procurement criteria evolve.
Looking ahead, the winners will be those who treat compliance and supply-chain resilience as strategic assets rather than cost centers, and who cultivate trusted channel ecosystems with documented certification and lifecycle support. By applying the segmentation and regional lenses described here, security and procurement leaders can move from reactive mitigation to proactive positioning-reducing operational risk while unlocking new revenue models grounded in managed services and analytics. The remainder of the full report expands each of these themes with implementation playbooks, supplier risk matrices, and sample contractual language to accelerate decision-making and reduce execution risk in complex procurement environments.
Contact Ketan Rohom, Associate Director of Sales & Marketing, to secure your tailored executive briefing and purchase the comprehensive perimeter security research package
To purchase the full perimeter security market research report and receive tailored briefings, contact Ketan Rohom, Associate Director, Sales & Marketing. Ketan can arrange a complimentary executive briefing that aligns the report's strategic findings with your organization’s priorities, including a walkthrough of segmentation insights, regional implications, and actionable scenarios for procurement, sourcing and partnership strategies. For procurement teams, the briefing can map vendor risk profiles against current tariff and regulatory developments; for product and R&D leaders, it can identify practical levers to preserve innovation velocity while mitigating component and materials supply risk. The report package includes a detailed appendix of regulatory sources, supplier due-diligence templates, and a prioritized implementation checklist to accelerate decision-making. Schedule a consultation with Ketan to explore bespoke research add-ons, enterprise licensing, or custom horizon-scanning workshops designed to convert insights into measurable actions and procurement outcomes.

- How big is the Perimeter Security Market?
- What is the Perimeter Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




