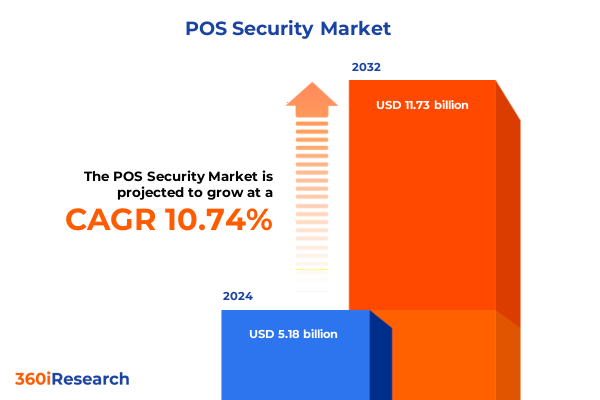
The POS Security Market size was estimated at USD 5.73 billion in 2025 and expected to reach USD 6.28 billion in 2026, at a CAGR of 10.75% to reach USD 11.73 billion by 2032.
Establishing the Imperative for Enhanced Point-of-Sale Security in a Rapidly Evolving Threat Environment with Proliferation of Connected Devices
Point-of-sale security sits at the intersection of technological innovation, regulatory compliance, and evolving threat vectors. In recent years, the proliferation of mobile payment terminals, cloud-connected devices, and integrated authentication modules has heightened both opportunities and vulnerabilities within retail, hospitality, and financial services environments. As the digital wallet paradigm expands, organizations must reevaluate legacy systems, align security postures with emerging standards, and anticipate adversarial tactics that leverage AI-driven reconnaissance.
This introduction establishes the imperative for a holistic analysis of point-of-sale security that transcends hardware and software silos. It underscores the fact that security is no longer an afterthought but a strategic enabler of customer trust, operational continuity, and revenue protection. By framing the discussion around real-world breach case studies, regulatory catalysts such as updated PCI DSS requirements, and the growing complexity of omnichannel transactions, this section sets the stage for a comprehensive exploration of market transformations, geopolitical impacts, segmentation dynamics, and actionable frameworks that follow.
In doing so, decision-makers gain a clear understanding that effective POS security strategies combine resilient hardware, adaptive software modules, and robust service partnerships. This foundational perspective guides stakeholders toward informed investments and collaborative vendor engagements that mitigate risk while fostering innovation.
Unveiling Pivotal Transformations Reshaping Point-of-Sale Security Architecture Across Hardware, Software, and Services in 2025
The point-of-sale security landscape has undergone swift and foundational shifts as organizations integrate biometric scanners, network-based intrusion detection, and AI-driven fraud detection into cohesive security architectures. What was once a collection of discrete devices and protocols now converges into unified ecosystems that must adapt in real time to novel phishing techniques, ransomware strains targeting transaction logs, and supply-chain compromises of embedded firmware.
Consequently, vendors and end users alike are rearchitecting platform designs, moving toward decentralized authentication schemes where two-factor biometrics interface with tokenized payment rails. This trend dovetails with a broader migration to cloud-native deployments that facilitate continuous monitoring and dynamic policy enforcement across distributed endpoints. Moreover, the increased reliance on host-based intrusion detection agents underscores a shift from perimeter defense to active endpoint resilience.
Simultaneously, the convergence of fraud and intrusion detection capabilities signals a transformative move toward unified threat management within POS environments. Organizations are deploying rule-based engines alongside adaptive AI models to detect anomalous payment patterns, automate incident response, and streamline compliance reporting. These transformative shifts reflect an industry consensus: securing point-of-sale operations demands an integrated blend of hardware, software, and service innovation.
Assessing the Far-Reaching Ramifications of the 2025 United States Tariff Regime on Point-of-Sale Hardware Supply Chains and Costs
In 2025, the United States imposed an array of tariffs targeting imported point-of-sale hardware components, from biometric scanners to payment security tokens, altering cost structures and procurement strategies across North American supply chains. The cascading impact of these trade measures has compelled vendors to reconsider manufacturing footprints, with several leading manufacturers initiating near-shore production partnerships in Mexico and Canada to mitigate tariff exposure.
This reactive reconfiguration of supply chains has not only influenced lead times for card readers and PIN pads but has also spurred opportunities for domestic assemblers to capture niche segments. Furthermore, price pressures have elevated the strategic value of software-centric and cloud-based security offerings, as organizations seek to balance hardware cost escalations with investments in AI-powered fraud detection and tokenization services.
From a strategic standpoint, the cumulative effects of these tariffs extend beyond immediate cost pass-throughs. They have accelerated vendor roadmaps that prioritize modular architectures, allowing clients to upgrade software features without undergoing full hardware replacements. Moreover, service providers are augmenting maintenance contracts and managed service agreements to offer longer-term value propositions that offset initial hardware investment spikes. Ultimately, these tariff-driven responses underscore a resilient market trend: adaptability and innovation in hardware deployment strategies are essential for maintaining competitive advantage.
Distilling Actionable Insights from Component, Application, Industry, and Deployment Segmentation to Illuminate Core Dynamics of POS Security Market
Insight into market dynamics emerges most vividly when examining how component frameworks, application use cases, industry verticals, and deployment modalities interplay to shape strategic priorities. By analyzing the hardware landscape, it becomes apparent that biometric scanners, card readers, PIN pads, and security tokens each address different risk profiles: biometric scanners prioritize identity proofing, whereas tokenization modules are central to payment security. Meanwhile, installation services, maintenance support, and managed offerings form the services backbone, ensuring continuous protection and regulatory alignment. On the software front, access control systems balance badge-based and PIN-based conveniences, authentication services marry biometrics with two-factor protocols, and fraud detection solutions blend AI-based algorithms with rule-based logic to identify suspicious transactions at the edge.
Shifting to application segmentation, the cross-functional deployment of these technologies highlights the industry’s move toward converged platforms that can simultaneously manage badge-based access, biometric verification, and tokenized payments. In terms of end users, financial services organizations such as banks, ATMs, and insurance entities demand high-assurance authentication and intrusion detection, while retail, hospitality, and healthcare providers often prioritize seamless consumer experiences alongside robust fraud prevention. Finally, examining deployment modes clarifies that cloud-hosted solutions-whether in hybrid, private, or public environments-offer scalability and centralized threat intelligence, whereas on-premises installations cater to organizations requiring customized, off-the-shelf controls.
Altogether, these multi-dimensional segmentation insights afford stakeholders a granular perspective on which components, applications, industries, and deployment strategies will drive value in the evolving POS security ecosystem.
This comprehensive research report categorizes the POS Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Application
- End User Industry
- Deployment Mode
Mapping Regional Divergence and Convergence in Point-of-Sale Security Adoption Trends Across the Americas, EMEA, and Asia-Pacific in 2025
Regional analysis reveals distinct adoption patterns and growth drivers across the Americas, Europe-Middle East-Africa, and Asia-Pacific markets. In the Americas, rapid retail digitalization and a strong vendor network have accelerated uptake of tokenization and AI-based fraud analytics, with leading retailers integrating network-based intrusion detection directly into point-of-sale terminals to safeguard omnichannel operations. Transitional dynamics in North America also reflect tighter regulatory scrutiny, prompting organizations to adopt two-factor authentication and encryption at scale to maintain PCI compliance.
Conversely, the EMEA region exhibits diverse maturity levels: Western Europe’s mature retail and hospitality sectors focus on badge-based access controls combined with advanced host-based intrusion sensors, whereas emerging markets in the Middle East and Africa are leapfrogging legacy systems, often opting for cloud-native managed services that simplify deployment and maintenance. This bifurcation of strategies illustrates the interplay between regulatory drivers and infrastructure readiness across the region.
Meanwhile, Asia-Pacific stands out for its rapid consumer adoption of mobile wallets and proximity-based payments, elevating the importance of seamless biometric authentication and rule-based fraud monitoring. Markets such as China and India are pioneering AI-driven intrusion detection integrations, while Australia and Japan emphasize public cloud deployments to facilitate real-time threat intelligence sharing. These regional insights underscore the necessity of tailoring security roadmaps to local regulatory frameworks, infrastructural capabilities, and consumer behaviors.
This comprehensive research report examines key regions that drive the evolution of the POS Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Strategic Moves and Portfolio Advancements of Leading Point-of-Sale Security Vendors Driving Innovation and Competitive Differentiation
Leading vendors are executing strategic product expansions and collaborative alliances to cement their positions in the POS security landscape. Legacy terminal manufacturers have diversified into biometric and tokenization services by acquiring specialized software firms, while cybersecurity incumbents are embedding host-based intrusion detection agents within payment terminals through OEM partnerships. These strategic maneuvers underscore a broader shift toward vertically integrated solutions that bridge hardware reliability with adaptive software capabilities.
Furthermore, several industry stalwarts have launched developer ecosystems and open APIs to foster third-party innovation in AI-based fraud detection and network-based intrusion management. By cultivating these platforms, vendors not only accelerate feature development but also enhance interoperability with enterprise access control and payment processing systems. Additionally, some organizations have invested in comprehensive managed service frameworks, offering round-the-clock monitoring and rapid incident response as differentiators in competitive procurement processes.
For decision-makers, monitoring these competitive dynamics provides insight into which vendor ecosystems prioritize modular integration, which focus on end-to-end managed services, and which excel in specialized software advancements. This competitive intelligence equips buyers to align procurement strategies with partners whose roadmaps and operational models best match their own security, compliance, and growth objectives.
This comprehensive research report delivers an in-depth overview of the principal market players in the POS Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Block, Inc.
- Bluefin Payment Systems LLC
- Braintree
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Clover Network, Inc.
- Elavon Inc.
- Fortinet, Inc.
- Heartland Payment Systems, Inc.
- Ingenico
- McAfee Corp.
- Palo Alto Networks, Inc.
- PAX Technology Limited
- Thales Group
- Toast, Inc.
- Verifone Systems, Inc.
- Visa Inc.
Formulating Pragmatic Strategies and Best Practices to Strengthen Organizational Posture Against Escalating Point-of-Sale Security Threats and Compliance Demands
Organizations seeking to fortify their point-of-sale security posture should embark on a phased approach that begins with rigorous risk assessments, encompassing both physical endpoints and digital payment channels. By conducting comprehensive vulnerability scans of card readers, biometric scanners, and payment tokens, stakeholders can prioritize remediation actions that address the most critical threats. Subsequently, integrating AI-based fraud detection engines alongside rule-based workflows ensures adaptive, real-time monitoring that evolves with transaction patterns.
Simultaneously, investing in end-user training on secure authentication practices and incident response protocols cultivates a security-first culture that complements technical controls. For maximum resilience, enterprises should architect hybrid cloud deployments for centralized policy orchestration while retaining on-premises custom modules to satisfy stringent data sovereignty requirements. Furthermore, embedding tokenization, encryption, and point-to-point security mechanisms at the transaction level isolates sensitive data and reduces the attack surface.
Ultimately, orchestrating these technical and organizational measures within long-term managed service agreements can align vendor SLAs with internal compliance deadlines and budget cycles. Through iterative reviews and continuous threat intelligence integration, industry leaders can pivot swiftly to emerging risks, ensuring that their POS security strategy remains robust and forward leaning.
Elucidating a Rigorous, Multi-Layered Research Methodology Integrating Qualitative Interviews, Secondary Data, and Triangulation for Unbiased Market Insights
This research employs a robust, multi-layered methodology to ensure the insights reflect current market realities and practical challenges. The process began with extensive secondary research, drawing from regulatory publications, open-source technical standards, and public filings to map the technology landscape and identify emerging threat patterns. Building upon this foundation, a series of in-depth interviews with industry practitioners, including CISOs, payment system integrators, and managed service providers, provided qualitative insights into procurement drivers and deployment barriers.
Data triangulation further enhanced the accuracy of findings by comparing interview inputs with vendor product literature and independent cybersecurity assessments. This was complemented by a review of breach case studies and compliance audit reports to validate the efficacy of different security controls in real-world scenarios. Throughout the research cycle, iterative peer reviews and expert panels helped refine key themes, ensuring that the framework remains devoid of bias and grounded in empirical evidence.
By integrating these quantitative and qualitative approaches, the methodology offers a transparent, reproducible blueprint that underpins each strategic insight. This precision enables stakeholders to trust the report’s conclusions and apply them to their unique operational contexts with confidence.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our POS Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- POS Security Market, by Component
- POS Security Market, by Application
- POS Security Market, by End User Industry
- POS Security Market, by Deployment Mode
- POS Security Market, by Region
- POS Security Market, by Group
- POS Security Market, by Country
- United States POS Security Market
- China POS Security Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 3975 ]
Synthesizing Key Learnings and Strategic Imperatives from the Latest Point-of-Sale Security Landscape to Inform Executive Decision-Making
The evolving point-of-sale security domain is shaped by converging trends in cloud migration, AI-driven threat detection, and biometric authentication, all against a backdrop of tighter regulatory frameworks and shifting trade policies. As hardware tariffs reshape supply chains, organizations must pivot to modular architectures and software-centric defenses. Meanwhile, the proliferation of mobile wallets and omnichannel commerce compels the integration of tokenization, encryption, and intrusion detection within unified platforms.
Collectively, these developments underscore several strategic imperatives: first, embrace adaptive security models that blend rule-based controls with machine-learning analytics; second, diversify deployment modes to balance scalability and sovereignty; and third, forge collaborative vendor partnerships that prioritize interoperability and managed services. By internalizing these lessons and aligning security roadmaps with organizational risk appetites, decision-makers can transform POS environments from potential vulnerabilities into competitive differentiators.
In summary, robust POS security is not a one-time project but an ongoing journey requiring continual investment in technology, training, and partnerships. Stakeholders who rigorously assess, plan, and iterate their strategies will be best positioned to navigate future disruptions while safeguarding transaction integrity and customer trust.
Empowering Stakeholder Engagement and Investment Decisions with Expert Guidance from Ketan Rohom to Secure a Comprehensive Point-of-Sale Security Market Report Purchase
Engaging directly with Ketan Rohom provides immediate access to tailored insights and a streamlined report acquisition process. By partnering with an expert who comprehends both the technical nuances and the commercial imperatives, stakeholders can accelerate their ability to make proactive investments in advanced point-of-sale security solutions. This direct line of communication ensures that specific organizational challenges-whether around encryption strategies, biometric integrations, or managed service deployments-are addressed comprehensively within the report.
Moreover, Ketan Rohom’s extensive experience in bridging research and sales contexts means that organizations benefit from actionable summaries, dedicated post-purchase support, and customized executive briefings. These value-added services transform a standard market study into a strategic roadmap that aligns with enterprise timelines and compliance imperatives. Readers are encouraged to reach out promptly to secure priority on report delivery, guarantee inclusion of bespoke market analyses, and unlock early-stage advisory sessions designed to refine implementation plans.
Connect now with Ketan Rohom, Associate Director of Sales & Marketing, to elevate your organization’s point-of-sale security strategy through authoritative, data-driven, and context-rich insights. Ensure that your next investment is informed by the latest trends, regulatory landscapes, and competitor dynamics outlined in a comprehensive market research report.

- How big is the POS Security Market?
- What is the POS Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




