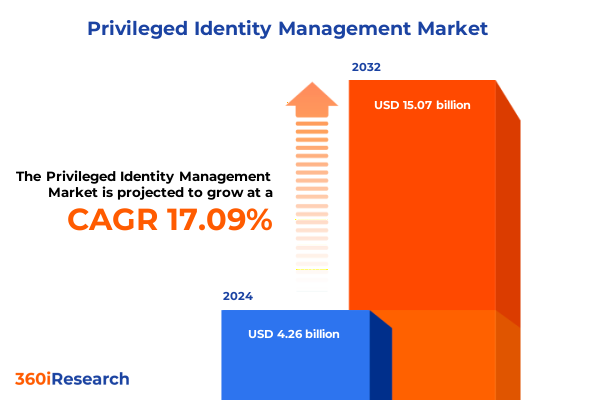
The Privileged Identity Management Market size was estimated at USD 4.93 billion in 2025 and expected to reach USD 5.70 billion in 2026, at a CAGR of 17.31% to reach USD 15.07 billion by 2032.
Unveiling the Strategic Imperative of Privileged Identity Management as the Foundation for Resilient and Secure Enterprise Operations
Enterprises today face a complex threat landscape where privileged accounts can both enable seamless operations and introduce critical vulnerabilities if not managed with precision. Privileged Identity Management (PIM) has emerged as a foundational discipline for safeguarding highly sensitive credentials, orchestrating privileged sessions, and enforcing least privilege principles. As digital transformation accelerates, organizations must strengthen PIM programs not only to fend off external attacks but also to mitigate insider risk and comply with an expanding array of regulations. In this context, an effective PIM framework evolves from being a mere component of identity and access management into a strategic enabler for resilient, zero-trust architectures.
Building on decades of cybersecurity best practices and propelled by advancements in automation, analytics, and cloud-native design patterns, modern PIM solutions deliver unprecedented visibility into privileged activities, context-aware controls, and streamlined workflows for credential lifecycle management. Organizations that proactively integrate PIM into their core security programs are better positioned to respond to dynamic threats while capitalizing on emerging technologies. This introduction sets the stage for a deep-dive analysis of how the PIM landscape is shifting, the impact of United States tariff measures, nuanced segmentation considerations, and regional dynamics shaping the market’s trajectory.
Revolutionary Technological Integrations and Heightened Regulatory Requirements Dramatically Reshape the Privileged Identity Management Environment
In just a few years, the privileged identity management ecosystem has been transformed by a confluence of technological breakthroughs and evolving regulatory mandates. The infusion of artificial intelligence and machine learning into PIM platforms now enables predictive risk scoring, behavior-based anomaly detection, and adaptive session controls. These capabilities shift the paradigm from reactive remediation to proactive prevention, equipping security teams with real-time insights and risk prioritization. Moreover, the maturation of infrastructure-as-code and DevSecOps practices has spurred integrations between PIM tools and orchestration pipelines, facilitating secure credential injection and just-in-time access for ephemeral workloads.
Meanwhile, regulatory frameworks such as the updated National Institute of Standards and Technology (NIST) guidelines, the California Consumer Privacy Act (CCPA), and sector-specific mandates are elevating the bar for privileged access governance. Compliance demands for robust audit trails, four-eye controls, and zero-trust enforcement have accelerated PIM adoption across highly regulated industries, including finance, healthcare, and government. As organizations navigate these transformative shifts, they must reassess legacy practices, optimize deployment models, and embed PIM into enterprise-wide risk management strategies to maintain agility and resilience.
Assessing the Strategic Consequences of United States Tariffs in 2025 on Privileged Identity Management Supply Chains and Cost Structures
The introduction of targeted tariffs on technology imports by the United States in early 2025 has reverberated throughout the privileged identity management value chain. Hardware appliances sourced from key manufacturing regions faced increased duties, prompting many solution providers to revisit their supply networks and production footprints. Concurrently, software platforms with embedded hardware components experienced elevated delivery costs, leading to adjustments in pricing models for on-premises and hybrid offerings. These added expenses have subsequently been passed down to end customers, tightening budget allocations for security initiatives.
In response, leading PIM vendors have accelerated investments in cloud-native architectures and containerized deployments, which inherently reduce reliance on physical hardware. These strategic moves have mitigated some of the tariff-induced cost pressures while enabling customers to pivot toward more scalable, pay-as-you-go consumption models. Nonetheless, for sectors where stringent latency and data residency requirements persist-such as federal government and critical infrastructure-on-premises appliances remain indispensable. Navigating the cumulative impact of these tariff measures requires a delicate balance between cost optimization and compliance adherence, underscoring the importance of flexible PIM frameworks capable of evolving with global trade dynamics.
Illuminating Critical Market Segmentation by Solution Type Deployment Model Organization Size and Industry Vertical to Guide Targeted Investments
A deeper look at solution types reveals that access orchestration tools have grown in prominence as organizations seek to harmonize disparate credential management processes, while least privilege management engines enforce granular access policies to reduce lateral movement risks. Password vaulting continues to be a cornerstone of PIM strategies, encompassing both privileged password management for individual accounts and shared account management for collaborative environments. Session management capabilities, integrating real-time monitoring and forensic recording, complete the spectrum of functionalities that cater to enterprises’ evolving security imperatives.
Turning to deployment models, cloud-based solutions-spanning private and public cloud infrastructures-are driving rapid adoption due to their inherent scalability and reduced total cost of ownership. Hybrid deployments, blending cloud agility with on-premises control, offer a pragmatic transitional path for organizations migrating from legacy estates. On-premises implementations, while still prevalent in highly regulated sectors, face pressure to adopt more containerized and virtualized form factors to optimize performance and manageability.
When examining organization size, large enterprises leverage extensive PIM integrations across complex IT estates and benefit from dedicated security teams to orchestrate privileged access at scale. In contrast, small and medium enterprises, encompassing both small enterprises and medium enterprises, demand simplified interfaces and preconfigured policy templates to accelerate time to value. Vendors targeting this segment have thus expanded capabilities for self-service provisioning and automated compliance reporting to address resource constraints.
Within industry verticals, banking institutions-including commercial banking and retail banking-prioritize stringent access controls and auditability to uphold financial regulations. Government entities at both federal and state and local levels require robust segmentation to safeguard critical systems and citizen data. Healthcare and insurance providers focus on HIPAA and data privacy mandates, while manufacturing, retail, and ecommerce organizations emphasize seamless integration with operational technology and customer-facing platforms. These vertical-specific drivers shape solution road maps and inform prioritization of feature development.
This comprehensive research report categorizes the Privileged Identity Management market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Solution Type
- Industry Vertical
- Deployment Model
Unraveling Regional Growth Patterns and Regulatory Drivers Influencing Privileged Identity Management Adoption in Americas EMEA and Asia-Pacific
Across the Americas, privileged identity management has reached a mature stage, marked by widespread adoption among Fortune 500 enterprises and large public sector agencies. Organizations in the United States and Canada are championing zero-trust initiatives, accelerating their shift to cloud-first PIM implementations while leveraging deep partnerships with leading technology providers. Mexico and Brazil are witnessing growing interest among multinational corporations, which are harmonizing their global PIM policies to streamline cross-border operations and compliance.
In Europe, the Middle East, and Africa region, stringent data protection regulations such as the General Data Protection Regulation and emerging localized privacy laws have spurred significant demand for enhanced privileged access controls. The EMEA landscape is characterized by a diverse mix of early adopters in finance and government, and rising traction among mid-market enterprises seeking to bolster their cybersecurity posture. Meanwhile, complex geopolitical considerations and cross-border data flow restrictions are prompting organizations to prioritize regional data sovereignty and on-premises PIM deployments.
The Asia-Pacific region is emerging as the fastest-growing market for privileged identity management, driven by digital transformation agendas in sectors such as telecommunications, manufacturing, and public utilities. Countries including Australia, Japan, and Singapore have established rigorous cybersecurity standards that mandate privileged access governance, while India and Southeast Asian markets are scaling up investments to protect critical infrastructure. Cloud-native PIM offerings are particularly popular across APAC, where organizations value agility and localized data center availability to support global expansion strategies.
This comprehensive research report examines key regions that drive the evolution of the Privileged Identity Management market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Established Leaders and Innovative Disruptors Driving Privileged Identity Management Through Strategic Alliances and Feature Differentiation
In the competitive PIM landscape, a handful of global leaders distinguish themselves through comprehensive platforms, extensive partner ecosystems, and relentless innovation. These established vendors continuously refine their solutions through strategic acquisitions, such as the integration of advanced session intelligence or identity analytics capabilities. Simultaneously, a wave of challenger companies is disrupting the market with specialized offerings focused on emerging use cases like developer-centric privilege management and cloud-native secret vaulting.
Collaboration between PIM vendors and leading cloud service providers has created co-engineered solutions optimized for hybrid environments, while partnerships with managed security service providers extend coverage for organizations lacking in-house expertise. On the product front, the rise of embedded PIM modules within broader identity governance suites is blurring the lines between standalone and platform-based approaches. As competition intensifies, pricing flexibility, user experience, and outcome-based service models are becoming key differentiators for PIM vendors aiming to capture both large enterprise and mid-market segments.
This comprehensive research report delivers an in-depth overview of the principal market players in the Privileged Identity Management market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- ARCON by NEC Corporation
- BeyondTrust Software, Inc.
- Broadcom, Inc.
- CyberArk Software Ltd.
- Delinea Inc.
- Ekran System
- Fortra, LLC
- Foxpass, Inc.
- Hitachi Solutions, Ltd.
- IBM Corporation
- Iraje Inc.
- Kron Teknoloji A.Ş.
- Microsoft Corporation
- One Identity by Quest Software Inc.
- Open Text Corporation
- Optrics Inc.
- Oracle Corporation
- Osirium Ltd.
- Quest Software Inc.
- Saviynt Inc.
- Sennovate Inc.
- Silverlake Mastersam Pte Ltd
- Simeio Solutions, LLC
- WALLIX Group SA
- Zoho Corporation Pvt. Ltd.
Strategic Actions for Industry Leaders to Embed Zero Trust Automation and Drive Continuous Evolution of Privileged Identity Management Initiatives
To stay ahead in the evolving PIM market, industry leaders should prioritize the adoption of zero-trust frameworks that assert least privilege by default and enforce real-time access policies. Integrating artificial intelligence capabilities will enhance threat detection and drive automated remediation workflows, reducing the burden on security operations teams. Additionally, aligning PIM initiatives with broader DevSecOps practices ensures that privileged access controls are embedded throughout the development and deployment lifecycle.
Organizations must also cultivate strong vendor relationships to leverage roadmap visibility and early access to new features, while demanding transparent pricing models that align costs with consumption patterns. Structuring PIM rollouts in phased waves-beginning with high-risk systems and progressively expanding to cover emerging workloads-will balance risk reduction with resource constraints. Finally, establishing a continuous improvement cycle based on operational metrics and stakeholder feedback will ensure that PIM programs remain adaptive, measurable, and tightly aligned with evolving business objectives.
Comprehensive Research Framework Integrating Primary Stakeholder Interviews Surveys and Secondary Source Analysis to Ensure Rigorous Market Insights
This analysis was developed through a robust, multi-faceted research approach combining qualitative and quantitative methodologies. Primary data was gathered via structured interviews with security executives, identity and access management architects, and CISOs across diverse industries to capture firsthand perspectives on PIM challenges and success factors. These insights were complemented by detailed surveys targeting both large enterprises and mid-market organizations, ensuring a balanced representation of organizational maturity levels.
Secondary research involved a systematic review of regulatory documentation, industry whitepapers, vendor technical briefs, and publicly available case studies. This was augmented by an examination of capital expenditure filings and technology partnership announcements to validate market dynamics. Data triangulation techniques were employed to reconcile discrepancies between sources, while continuous feedback loops with subject matter experts ensured accuracy and relevancy. The combined methodology delivers a comprehensive and balanced view of the privileged identity management market, free from proprietary biases and grounded in empirical evidence.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Privileged Identity Management market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Privileged Identity Management Market, by Solution Type
- Privileged Identity Management Market, by Industry Vertical
- Privileged Identity Management Market, by Deployment Model
- Privileged Identity Management Market, by Region
- Privileged Identity Management Market, by Group
- Privileged Identity Management Market, by Country
- United States Privileged Identity Management Market
- China Privileged Identity Management Market
- Competitive Landscape
- List of Figures [Total: 15]
- List of Tables [Total: 1272 ]
Synthesizing Emerging Trends Technology Advances and Regional Dynamics to Chart a Clear Path Forward in Privileged Identity Management
The intersection of advanced technology, evolving regulatory landscapes, and global trade dynamics is elevating privileged identity management from a tactical control to a strategic business enabler. Organizations that invest in modern PIM frameworks, underpinned by zero-trust principles and AI-driven automation, will achieve stronger security postures and enhanced operational efficiency. Regional nuances-from mature adoption in the Americas to rapid growth in Asia-Pacific-present tailored opportunities for vendors and end users alike.
As the tariff environment evolves and digital transformation accelerates, flexibility in deployment models and targeted segmentation strategies will be paramount. By synthesizing insights across solution types, deployment preferences, organization size, and industry verticals, decision-makers can craft nuanced approaches that mitigate risk and optimize resource allocation. Ultimately, a well-executed PIM program will serve as the linchpin for safeguarding critical assets, ensuring compliance, and enabling secure innovation in an increasingly complex digital economy.
Partner with Ketan Rohom to Access the Full Privileged Identity Management Market Intelligence Report and Empower Your Security Strategy
To gain unparalleled access to the comprehensive insights presented in this Privileged Identity Management market research report, we invite you to connect directly with Ketan Rohom, Associate Director, Sales & Marketing at 360iResearch. By engaging with Ketan, you will secure the strategic intelligence needed to optimize your security investments, align your privileged access strategy with emergent industry trends, and accelerate time-to-value for your organization’s cybersecurity initiatives. Ketan’s expertise will guide you through package options tailored to your business goals and ensure seamless integration of actionable findings into your enterprise roadmap. Contact Ketan Rohom today to unlock the full depth of analysis, secure your competitive edge, and empower your decision-making with data-driven clarity.

- How big is the Privileged Identity Management Market?
- What is the Privileged Identity Management Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




