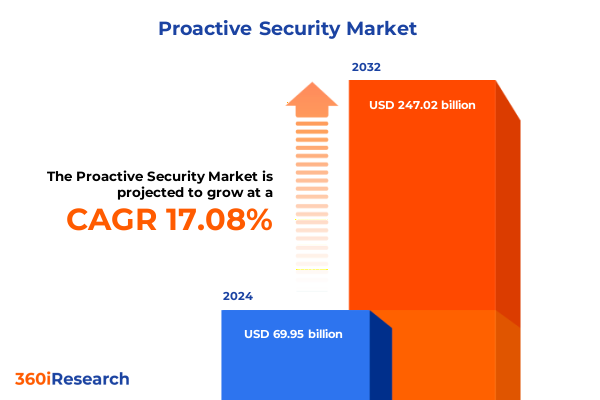
The Proactive Security Market size was estimated at USD 81.70 billion in 2025 and expected to reach USD 95.42 billion in 2026, at a CAGR of 17.12% to reach USD 247.02 billion by 2032.
Setting the Stage for Proactive Security Strategies in an Era Defined by Rapid Technological Evolution and Emerging Cyber Threats
In an age marked by unparalleled digital transformation and an ever-expanding cyber threat landscape, organizations can no longer rely solely on reactive security measures. Proactive security emphasizes the anticipation, identification, and mitigation of risks before they materialize into breaches or disruptions. This strategic shift demands a fundamental recalibration of conventional approaches, requiring enterprises to integrate predictive analytics, continuous monitoring, and threat hunting into their core defense architectures. The goal is to minimize the window of exposure by detecting anomalies, vulnerabilities, and emerging threats in real time.
By embedding proactive security practices into every stage of the development lifecycle and operational framework, enterprises can foster a culture of resilience. Security teams gain visibility into potential attack vectors, enabling them to prioritize resources and orchestrate rapid responses. Proactive security also catalyzes collaboration among IT, DevOps, and business units, ensuring that security considerations are integral to innovation rather than an afterthought. As organizations embrace digital initiatives-from cloud migrations to Internet of Things deployments-this introduction underscores the importance of shifting from a reactive to a proactive posture to safeguard assets, reputation, and trust.
Exploring How AI, Zero Trust, and Automation Are Revolutionizing Modern Proactive Security Practices to Counter Advanced Threats
The proactive security landscape has been reshaped by transformative shifts that challenge traditional boundaries and accelerate innovation. Artificial intelligence and machine learning now power advanced threat detection systems that adapt to evolving attack patterns, replacing static signatures with dynamic behavioral analysis. Security solutions have transcended perimeter-based models, adopting zero trust architectures that validate every user and device before granting access. Such models significantly reduce the risk of lateral movement within networks and complement proactive threat hunting practices.
Concurrently, the convergence of IT and operational technology has blurred the lines between digital and physical security, elevating the importance of cross-domain threat intelligence. Security orchestration and automated response platforms have emerged to streamline incident investigation, accelerating remediation workflows and freeing analysts to focus on complex threats. Moreover, the rise of cloud-native applications has spurred the adoption of infrastructure-as-code scanning and runtime protection, embedding security controls within development pipelines. These shifts reflect a broader trend toward integration, automation, and anticipatory defense, equipping organizations to navigate an increasingly sophisticated threat environment with agility and precision.
Analyzing the Far-Reaching Consequences of Recent Tariff Changes on Hardware, Software, and Cloud-Driven Security Deployments
United States trade policies in 2025 have introduced new layers of complexity for technology sourcing and deployment within security architectures. Tariffs on foreign hardware components, particularly those sourced from key semiconductor producing nations, have led to increased costs and supply chain realignments. Hardware-dependent security appliances now face longer lead times, prompting enterprises to diversify procurement channels or pivot toward software-centric, cloud-delivered security services that mitigate exposure to tariff volatility.
Furthermore, increased duties on network infrastructure components have catalyzed a shift toward virtualized network security functions, as organizations seek to decouple their security layers from expensive physical devices. This trend dovetails with the broader move to edge computing and distributed environments, where agility and cost-efficiency are paramount. Proactive security teams must now factor in tariff-induced cost fluctuations when architecting resilient solutions, balancing on-premise requirements with cloud-native services to optimize total cost of ownership. The cumulative impact of these tariffs underscores the need for flexible, software-driven security strategies that can adapt to evolving trade landscapes without compromising efficacy.
Uncovering How Distinct Security Types, Components, Deployment Modes, and Organizational Profiles Define Tailored Proactive Security Approaches
When examining proactive security through the lens of security type segmentation, organizations can discern distinct priorities and investment patterns. Application security efforts are increasingly focused on interactive testing techniques that provide contextual insight into code behavior, while static analysis remains a foundational control for early vulnerability detection. Cloud security spans multiple service models, pushing teams to secure everything from infrastructure to end-user applications against configuration drift and unauthorized access. Endpoint security has evolved beyond traditional antivirus solutions, with endpoint detection and response platforms offering advanced visibility and automated remediation across desktops, mobile devices, and IoT endpoints. Network security continues to anchor perimeter defenses, though microsegmentation and software-defined controls are gaining prominence to isolate workloads.
Component segmentation reveals a growing appetite for managed services as organizations seek to augment internal expertise and streamline operations, while professional services deliver customized assessments and integration support. Deployment mode preferences vary by maturity level, with cloud-first organizations leveraging rapid scalability and on-premise environments persisting in highly regulated industries. Industry verticals such as financial services and healthcare prioritize stringent compliance and data privacy, whereas technology sectors emphasize rapid innovation cycles and secure development practices. Lastly, enterprise size shapes security strategy, as large organizations deploy multi-layered, integrated platforms, while small and medium enterprises often favor modular solutions to align with leaner budgets and staffing models.
This comprehensive research report categorizes the Proactive Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Security Type
- Enterprise Size
- Deployment Mode
- End User
Examining How Diverse Regulatory Landscapes and Digital Maturity Levels Shape Proactive Security Investments Across Key Global Regions
Regional dynamics exert a significant influence on proactive security priorities and resource allocation. In the Americas, a robust regulatory environment and widespread digital transformation initiatives drive investments in cloud-native security services and automation, with organizations leveraging local expertise to address evolving compliance frameworks. Meanwhile, Europe, the Middle East, and Africa present a diverse regulatory tapestry characterized by stringent data privacy laws and geopolitical considerations that shape cross-border threat intelligence sharing. Enterprises in this region often balance local data residency requirements with global collaboration efforts to maintain cohesive security postures.
Across the Asia-Pacific region, rapid cloud adoption and mobile-first strategies create a fertile ground for innovative security solutions. Organizations grapple with balancing cost pressures with the need for advanced threat prevention in markets where digital ecosystems evolve at breakneck speed. Furthermore, regional partnerships between technology vendors and governments have accelerated the deployment of secure infrastructure projects, underscoring proactive security’s role in supporting national digital agendas. These regional insights illuminate how variations in regulatory regimes, digital maturity, and partnership ecosystems drive differentiated security investments and strategic priorities.
This comprehensive research report examines key regions that drive the evolution of the Proactive Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting How Collaborative Technology and Service Providers Are Driving Innovation in Proactive Cybersecurity Solutions
Leading vendors in proactive security have honed their offerings to address the multifaceted needs of modern enterprises. Innovative cybersecurity providers deliver integrated platforms that converge endpoint, network, and cloud security under a unified dashboard, enabling centralized policy enforcement and analytics-driven threat hunting. Certain specialists differentiate themselves through proprietary artificial intelligence models that refine threat classification and automate low-level response actions, reducing dwell time and relieving analyst workloads.
Meanwhile, service-centric players continue to expand their managed detection and response portfolios, offering 24/7 monitoring and incident response support through global security operations centers. These firms emphasize threat intelligence sharing and scenario-based simulations to elevate preparedness and validate controls under real-world conditions. Partnerships between technology vendors and managed service providers have grown increasingly common, facilitating seamless integration of advanced security tools with tailored service-level agreements. This collaborative dynamic enhances scalability and adaptability, empowering organizations to navigate complex threat landscapes with confidence.
This comprehensive research report delivers an in-depth overview of the principal market players in the Proactive Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- AT&T Cybersecurity, Inc.
- Broadcom Inc.
- Centrify Corporation
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Corvil Ltd.
- CrowdStrike Holdings, Inc.
- CyberSponse, Inc.
- FireMon, LLC
- Fortinet, Inc.
- IBM Corporation
- LogRhythm, Inc.
- McAfee Corp.
- Oracle Corporation
- Palo Alto Networks, Inc.
- Qualys, Inc.
- Rapid7, Inc.
- RSA Security LLC
- Securonix, Inc.
- Siemplify Ltd.
- Skybox Security, Inc.
- Sophos Ltd.
- Splunk Inc.
- ThreatConnect, Inc.
- Trellix, Inc.
- Trend Micro Incorporated
Implementing Unified Analytics, Collaborative Exercises, and Modular Architectures to Enhance Proactive Security Posture and Agility
Industry leaders can fortify their proactive security strategies by prioritizing the integration of predictive analytics and threat intelligence into existing workflows. By aligning security operations and development teams around shared telemetry and automated testing frameworks, organizations can identify and remediate vulnerabilities earlier in the lifecycle. Investing in dynamic risk scoring that adapts to changes in the threat environment enables security teams to allocate resources effectively and prioritize response efforts based on real-time risk assessments.
Additionally, cultivating strategic partnerships with managed service providers can bridge skill gaps and augment in-house capabilities. Engaging in regular tabletop exercises and red team assessments sharpens incident response readiness while validating the efficacy of security controls under stress. Organizations should also develop modular architectures that support both cloud-native and on-premise deployments, ensuring flexibility in the face of shifting regulatory and supply chain constraints. Finally, establishing a continuous improvement cycle-driven by post-incident reviews and threat landscape analyses-ensures that proactive security measures evolve alongside emerging risks, reinforcing organizational resilience.
Detailing a Comprehensive, Multi-Source Research Framework That Ensures Validity Through Data Triangulation and Expert Validation
The research underpinning these insights was conducted using a rigorous methodology that combines primary interviews with cybersecurity practitioners, industry experts, and decision-makers across various sectors. Secondary research comprised an exhaustive review of regulatory guidelines, vendor whitepapers, peer-reviewed journals, and threat intelligence reports. Data triangulation was employed to validate findings by cross-referencing vendor capabilities with end-user feedback and independent test results.
Quantitative analysis of deployment preferences and technology adoption patterns was supported by anonymized survey responses from enterprise security leaders, providing statistical rigor and trend validation. Qualitative analyses, including scenario-based case studies, illustrated implementation challenges and best practices in diverse environments. Finally, iterative expert reviews ensured the accuracy, relevance, and applicability of the study’s conclusions, culminating in actionable insights tailored to real-world proactive security needs.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Proactive Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Proactive Security Market, by Component
- Proactive Security Market, by Security Type
- Proactive Security Market, by Enterprise Size
- Proactive Security Market, by Deployment Mode
- Proactive Security Market, by End User
- Proactive Security Market, by Region
- Proactive Security Market, by Group
- Proactive Security Market, by Country
- United States Proactive Security Market
- China Proactive Security Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1590 ]
Synthesizing the Imperative of Anticipatory Defense as a Strategic Lever for Innovation, Trust, and Organizational Resilience
Proactive security has emerged as a critical enabler for organizations seeking to stay ahead of increasingly sophisticated threats and regulatory complexities. By integrating advanced detection techniques, zero trust principles, and automated response mechanisms, enterprises can transition from reactive postures to adaptive defense frameworks that anticipate and neutralize risks. The influence of trade policies, regional regulations, and segmentation dynamics underscores the importance of flexible, software-led architectures capable of evolving alongside the threat landscape.
As security teams refine their strategies, the convergence of technology and services fosters deeper collaboration, unlocking efficiencies and elevating resilience. Leaders who embrace predictive analytics, cross-functional coordination, and continuous improvement cycles will be best positioned to navigate the multifaceted challenges of today’s environment. Ultimately, proactive security is not merely a defensive imperative but a strategic asset that drives innovation, protects stakeholder trust, and sustains competitive advantage.
Empower Your Organization with Expert Insights by Engaging Directly with Our Associate Director for a Tailored Market Research Experience
To take advantage of deep insights drawn from rigorous analysis, reach out to Ketan Rohom, Associate Director, Sales & Marketing at 360iResearch, and secure your copy of the comprehensive market research report today. Bridge the gap between uncertainty and informed decision making by leveraging data-driven strategies and customized guidance that align with your organization’s unique security objectives. Contact Ketan to explore tailored solutions and stay ahead in the proactive security arena with confidence; ensure your enterprise is equipped to navigate evolving threats and regulatory landscapes effectively.

- How big is the Proactive Security Market?
- What is the Proactive Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




