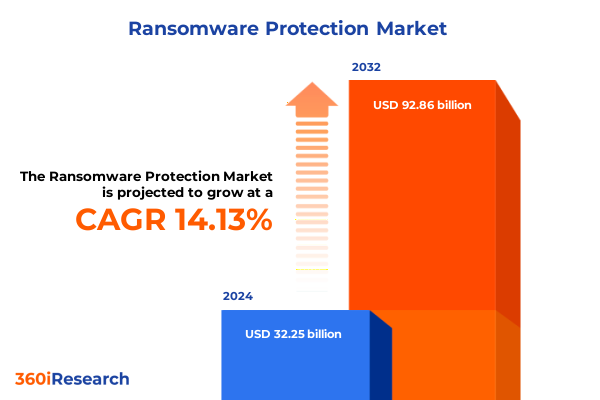
The Ransomware Protection Market size was estimated at USD 36.86 billion in 2025 and expected to reach USD 41.35 billion in 2026, at a CAGR of 14.10% to reach USD 92.86 billion by 2032.
Establishing the Critical Context for Ransomware Protection Strategies Amid Intensifying Cyber Threats and Regulatory Pressures
Organizations worldwide are contending with an escalating wave of ransomware attacks that exploit vulnerabilities across complex IT environments. Malicious actors have refined their intrusion methods, shifting from opportunistic breaches to highly targeted campaigns that can demand multi-million-dollar ransoms. Simultaneously, regulatory bodies have intensified compliance requirements, mandating stricter reporting standards and higher fines for breach-related negligence. This convergence of heightened threat sophistication and regulatory scrutiny underscores the critical necessity for an in-depth understanding of ransomware protection strategies.
As the digital landscape evolves, security leaders must navigate an intricate mix of legacy infrastructure, cloud-native applications, and increasingly distributed workforces. In this context, a proactive and layered defense approach is paramount. By interpreting the interplay between emerging technologies, shifting attacker techniques, and changing policy frameworks, stakeholders can craft resilient architectures that deter, detect, and respond to ransomware events. This executive summary sets the stage for exploring transformative shifts, tariff impacts, segmentation insights, regional dynamics, competitive positioning, and strategic recommendations to empower organizations in fortifying their ransomware defenses.
Navigating the Emerging Technological and Threat Landscape That Is Redefining Ransomware Protection Priorities and Architectural Approaches
The ransomware protection landscape has undergone significant transformations, driven by advancements in artificial intelligence, zero trust principles, and automation orchestrations. AI-powered threat detection algorithms now analyze vast telemetry streams in real time, correlating anomalous behaviors to preemptively identify potential intrusions. Meanwhile, the adoption of zero trust architectures has redefined perimeter-centric models, compelling organizations to authenticate and authorize every access request regardless of network location.
Automation plays a pivotal role in accelerating incident response, enabling security teams to deploy predefined playbooks that isolate affected endpoints, trigger backups, and initiate forensic investigations within seconds of detection. Furthermore, threat actors have begun leveraging automation themselves, employing ransomware-as-a-service platforms to scale campaigns with minimal technical expertise. Consequently, defenders must continuously innovate, integrating machine learning models with human expertise to sustain a robust deterrence posture.
In addition to technological shifts, the industry is witnessing a surge in collaborative initiatives such as cyber threat intelligence sharing among peer organizations and public–private partnerships. These cooperative frameworks enhance situational awareness and fast-track the refinement of defensive tactics. As ransomware tactics evolve, the ability to adapt through integrated threat intelligence, dynamic policy enforcement, and seamless orchestration across security tools emerges as a defining characteristic of resilient organizations.
Assessing the Broad Spectrum Consequences of 2025 United States Tariff Adjustments on Ransomware Protection Supply Chains and Technology Adoption
In 2025, new United States tariffs on imported cybersecurity hardware and software components have introduced additional complexity into supply chain planning and procurement decisions. Organizations reliant on international vendors have encountered extended lead times and increased costs, prompting a reevaluation of sourcing strategies. Some enterprises have shifted toward domestic manufacturers or diversified their supplier pools to mitigate tariff-driven price inflation and potential shipment delays.
These procurement adjustments have influenced the adoption of critical ransomware protection technologies, particularly in areas such as secure web gateways, intrusion prevention systems, and advanced endpoint detection and response platforms. As businesses weigh the tradeoffs between cost, performance, and compliance, many have opted for cloud-based deployment models that offer pay-as-you-go flexibility and reduced capital expenditures. The tariff environment has thus accelerated cloud migration trends for organizations seeking to decouple security investments from hardware procurement cycles.
Moreover, professional and managed security service providers have adapted by absorbing some tariff impacts through strategic partnerships and volume-based purchasing agreements. This collaborative approach has enabled clients to maintain access to cutting-edge ransomware defenses without bearing the full brunt of heightened import costs. Consequently, the 2025 tariff landscape has acted as a catalyst for innovative sourcing, deployment, and service delivery models in the ransomware protection domain.
Uncovering Actionable Insights from Multidimensional Segmentation of Ransomware Protection Solutions Across Service Types Deployment Modes and Industry Verticals
A multifaceted segmentation approach to ransomware protection reveals distinct dynamics across solution types, components, deployment modes, organization sizes, and industry verticals. Within solution types, backup and recovery tools integrate backup software and recovery services to ensure rapid data restoration, while endpoint security solutions combine antivirus engines, application control mechanisms, and endpoint detection and response capabilities to thwart malicious payloads before execution. Managed services encompass consulting engagements, incident response teams, and continuous monitoring services that extend internal expertise, whereas network security offerings comprise next-generation firewalls, intrusion prevention systems, and secure web gateways designed to filter traffic at perimeter and internal network segments.
When examining components, software suites deliver the core detection, analysis, and orchestration functionalities, while services-both managed and professional-provide essential customization, integration, and operational support. Deployment mode further influences strategic decisions, as cloud-based solutions offer elastic scalability and simplified maintenance, on-premises platforms enable granular control over data residency, and hybrid configurations balance agility with security requirements. The dichotomy between large enterprises and small and medium enterprises highlights varying resource allocations; larger organizations often invest in comprehensive, multi-layered defenses, whereas smaller businesses prioritize straightforward, cost-effective solutions that deliver rapid time to value.
Industry vertical segmentation uncovers specialized requirements across banking, financial services and insurance organizations focused on regulatory compliance, government agencies prioritizing data sovereignty, healthcare providers safeguarding patient records across hospital systems, medical device networks, and pharmaceutical research environments, IT and telecom firms confronting large-scale distributed attacks, manufacturing plants protecting operational technology networks, and retail chains defending point-of-sale systems and e-commerce platforms. Each vertical demands a tailored blend of technologies, processes, and services to address its unique threat profile and business imperatives.
This comprehensive research report categorizes the Ransomware Protection market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Solution Type
- Component
- Deployment Mode
- Organization Size
- Industry Vertical
Evaluating Critical Regional Dynamics Shaping the Evolution of Ransomware Protection Strategies Across Americas EMEA and Asia Pacific Markets
Regional dynamics play a pivotal role in shaping ransomware protection strategies, reflecting distinct regulatory regimes, threat actor ecosystems, and technology adoption curves. In the Americas, stringent data breach notification laws and a thriving cybersecurity vendor landscape have fostered rapid deployment of advanced endpoint detection and response platforms and integrated backup solutions. North American organizations frequently pilot AI-driven anomaly detection and share intelligence through industry consortiums, driving a culture of innovation and resilience against state-sponsored and financially motivated ransomware groups.
Across Europe, the Middle East, and Africa, regulatory frameworks such as the GDPR and national cybersecurity directives have driven demand for solutions emphasizing data privacy, cross-border compliance, and incident reporting protocols. Enterprises in this region often adopt hybrid architectures to satisfy both EU data residency requirements and the agility demands of global operations. Collaborations between public sector agencies and private cybersecurity firms have enhanced threat intelligence sharing, while managed services remain popular among organizations seeking specialized expertise to navigate complex regulatory landscapes.
In the Asia-Pacific region, rapid digitization initiatives and expanding cloud ecosystems have accelerated the integration of ransomware protection capabilities into core IT infrastructures. Government-led programs to bolster critical infrastructure security have encouraged public and private entities to invest in zero trust frameworks and secure web gateways. The increasing prevalence of regional ransomware variants has underscored the need for localized threat intelligence feeds and industry-specific incident response playbooks, propelling demand for both on-premises and cloud-native solutions across commercial and government verticals.
This comprehensive research report examines key regions that drive the evolution of the Ransomware Protection market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Competitive Positioning and Innovation Trajectories of Leading Providers in the Ransomware Protection Ecosystem
Leading providers in the ransomware protection ecosystem have differentiated themselves through a combination of technological innovation, strategic partnerships, and service integrations. Cloud-native vendors have capitalized on platform-as-a-service models to streamline deployment and updates, embedding machine learning-driven detection engines directly into their SaaS offerings. Meanwhile, traditional endpoint security firms have expanded their portfolios with backup and recovery modules, enabling a unified approach to prevention and data restoration.
Service-oriented organizations have established managed detection and response offerings that deliver 24/7 monitoring, threat hunting, and incident containment capabilities. These providers emphasize deep domain expertise in compliance-heavy industries, offering tailored playbooks for sectors such as healthcare and finance. Partnerships with global system integrators and cloud hyperscalers have further extended their market reach, facilitating seamless integration of ransomware protection technologies into broader digital transformation initiatives.
Consolidation trends are also evident, with several key players acquiring specialized startups focused on orchestration, threat intelligence, and deception technologies. Such acquisitions have enriched vendor portfolios by adding automated response workflows, real-time attack mapping, and decoy environments that divert adversaries. As the market matures, the competitive landscape is defined by the ability to deliver end-to-end resilience-from proactive threat detection through post-incident recovery-within a cohesive, managed framework.
This comprehensive research report delivers an in-depth overview of the principal market players in the Ransomware Protection market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Acronis International GmbH
- BlackBerry Limited
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems Inc.
- CrowdStrike Holdings Inc.
- CyberArk Software Ltd.
- Datto Holding Corp.
- Dell Technologies Inc.
- Fortinet Inc.
- IBM Corporation
- Kaspersky Lab
- Malwarebytes Corporation
- McAfee Corp.
- Microsoft Corporation
- Palo Alto Networks Inc.
- SentinelOne Inc.
- Sophos Ltd.
- Trend Micro Incorporated
- Zscaler Inc.
Delivering Targeted Strategic and Operational Recommendations to Enhance Organizational Resilience Against Ransomware Threats and Regulatory Complexities
Industry leaders should adopt a blend of strategic and operational measures to fortify their ransomware defenses. First, embedding continuous threat intelligence sharing into governance structures ensures that emerging attack vectors are promptly incorporated into detection rules and incident response playbooks. Next, aligning zero trust principles-such as least-privilege access and microsegmentation-with existing network architectures reduces lateral movement opportunities for malicious actors.
Organizations must also prioritize the orchestration of backup and recovery workflows, verifying that restore procedures are regularly tested under realistic failover scenarios. Integrating backup validation checks into automated scripts can guarantee data integrity and accelerate recovery timelines. Furthermore, allocating resources to develop internal incident response capabilities-complemented by managed services engagements-provides a force multiplier effect, balancing on-demand expertise with in-house situational awareness.
Lastly, to sustain a resilient posture, executives should champion a culture of cybersecurity awareness that extends beyond the IT department. Regular cross-functional drills, tabletop exercises, and executive briefings cultivate organizational readiness and expedite decision-making during high-pressure ransomware events. By implementing these recommendations, enterprises can elevate their defense-in-depth strategies and maintain adaptive resilience in the face of continually evolving ransomware threats and regulatory demands.
Outlining a Robust Research Framework Combining Qualitative and Quantitative Approaches to Illuminate Ransomware Protection Market Dynamics
The research methodology underpinning this report integrates qualitative expert interviews, primary survey data, and secondary research from reputable industry publications and open-source intelligence. Interviews with CISOs, security architects, and managed security service provider executives provided firsthand perspectives on operational challenges and solution effectiveness. These insights were complemented by survey responses from IT decision makers across multiple sectors, capturing priorities in budget allocation, technology adoption, and risk management practices.
Secondary research involved analysis of regulatory guidelines, cybersecurity incident reports, and vendor white papers to identify common failure modes and benchmark best practices. Data from public threat intelligence repositories and malware analysis platforms offered quantitative metrics on attack frequency, ransom demands, and detection latency. This triangulation of data sources enabled a robust validation of market trends and technology capabilities.
To ensure comprehensive coverage, the study applied a rigorous framework that weights both technological efficacy and business impact. Each solution category was evaluated against criteria such as deployment flexibility, integration potential, and operational scalability. Service offerings were assessed for scope of coverage, response times, and cost efficiency. The combined qualitative and quantitative approach delivers reliable, actionable insights tailored to the evolving needs of security leaders navigating the complex ransomware landscape.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Ransomware Protection market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Ransomware Protection Market, by Solution Type
- Ransomware Protection Market, by Component
- Ransomware Protection Market, by Deployment Mode
- Ransomware Protection Market, by Organization Size
- Ransomware Protection Market, by Industry Vertical
- Ransomware Protection Market, by Region
- Ransomware Protection Market, by Group
- Ransomware Protection Market, by Country
- United States Ransomware Protection Market
- China Ransomware Protection Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1908 ]
Distilling Core Takeaways and Future Imperatives to Guide Stakeholders Through an Evolving Ransomware Protection Landscape
In summary, protecting against ransomware requires a holistic strategy that integrates cutting-edge technologies, adaptive operational processes, and cross-organizational collaboration. The convergence of AI-driven detection, zero trust mandates, and automated orchestration forms the technological foundation for resilient defenses. Meanwhile, the 2025 tariff environment, regional regulatory nuances, and segmentation-specific demands underscore the need for agile procurement and deployment models.
Key takeaways emphasize the importance of continuous threat intelligence sharing, rigorous validation of backup procedures, and the cultivation of incident response capabilities informed by realistic drills. Segmentation insights highlight that no single solution fits all; organizations must tailor their protection stack according to solution type, deployment season, organization size, and industry vertical requirements. Regional analysis reveals that success hinges on aligning security investments with local compliance mandates and threat actor profiles.
As ransomware tactics evolve, so too must defense strategies. Stakeholders are encouraged to leverage this report’s comprehensive analysis to drive informed decisions, optimize technology portfolios, and foster a culture of resilience. By adhering to the recommendations and insights presented, enterprises can navigate the complexities of the ransomware threat landscape and safeguard their critical assets against both current and emerging risks.
Inspiring Decision Makers to Secure the Complete Ransomware Protection Report Today by Connecting Directly with Associate Director Sales & Marketing Ketan Rohom
Every moment organizations delay in securing their defenses against ransomware increases the potential for operational disruptions, reputational damage, and financial loss. The comprehensive research report on ransomware protection offers indispensable insights into evolving threats, technological innovations, and strategic frameworks proven to safeguard critical assets. By engaging directly with Ketan Rohom, Associate Director, Sales & Marketing at 360iResearch, decision makers can access tailored guidance on leveraging the report’s detailed analysis to implement robust protection measures. Act now to fortify your enterprise against the next generation of ransomware attacks and ensure a resilient, future-ready security posture

- How big is the Ransomware Protection Market?
- What is the Ransomware Protection Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




