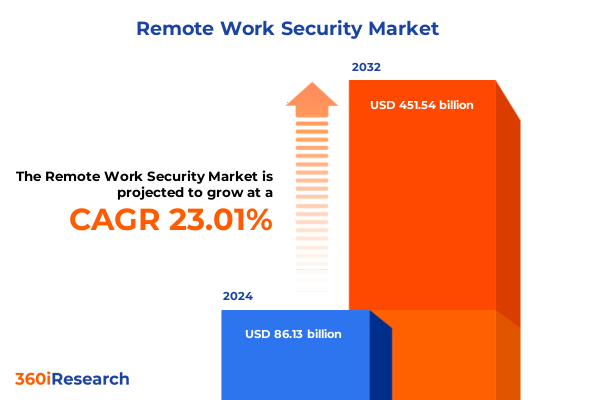
The Remote Work Security Market size was estimated at USD 105.61 billion in 2025 and expected to reach USD 129.50 billion in 2026, at a CAGR of 23.06% to reach USD 451.54 billion by 2032.
Framing the New Era of Remote Work Security Demands That Define Organizational Resilience and Technological Adaptation Imperatives
As organizations worldwide continue to adopt hybrid and fully remote work models, the traditional boundaries of corporate networks have dissolved, exposing enterprises to a broader array of security threats and vulnerabilities. In this new paradigm, employees access sensitive data from diverse locations and devices, often leveraging personal networks and bringing previously unseen risks to the enterprise perimeter. Cloud collaboration platforms, virtual desktop environments, and endpoint-driven workflows have become dominant modes of productivity, yet they also introduce complex challenges that require rethinking legacy security controls. This introduction sets the stage for understanding how security strategies must evolve beyond on-premises firewalls and static defenses to encompass a distributed ecosystem of cloud services, endpoints, and user identities. Moreover, organizations must balance user experience with robust protection to foster employee engagement and maintain business continuity.
The rapid acceleration of remote work initiatives demands that security stakeholders reevaluate legacy approaches and adopt adaptive, intelligent solutions that scale with evolving threats. Regulatory compliance regimes are tightening around data privacy and cross-border data flows, driving the need for more granular visibility and policy enforcement. Simultaneously, threat actors have honed sophisticated capabilities that exploit misconfigured cloud instances and unsecured endpoints. Against this backdrop, the imperative to integrate zero trust principles, leverage artificial intelligence for threat detection, and orchestrate multi-layered defense tactics becomes mission critical. As we move forward in the analysis, these foundational concepts will guide the exploration of market dynamics, technological innovation, and strategic actions essential for safeguarding modern work environments.
Unveiling Pivotal Transformations in Security Frameworks Fueled by Remote Work Evolution and Emerging Threat Vectors Strategic Adjustments
Remote work has catalyzed pivotal transformations in security frameworks, shifting the focus from perimeter-based defenses to identity-centric and data-centric strategies. The once well-defined corporate network boundary has fragmented into countless edge points, driven by the proliferation of endpoint devices and cloud workloads. Organizations are increasingly embracing secure access service edge architectures, integrating networking and security functions in a unified cloud-delivered model to address latency and scalability challenges. At the same time, identity and access management solutions have matured to prioritize continuous verification and adaptive authentication, reducing reliance on static credentials and fortifying the human element of the security stack.
Another transformative shift has emerged through the integration of artificial intelligence and machine learning in threat detection, enabling faster recognition of anomalous patterns and automated response orchestration. Threat intelligence feeds now inform dynamic policy adjustments that preemptively block emerging attack vectors. Additionally, the adoption of microsegmentation and zero trust network access strategies isolates workloads and applications, minimizing lateral movement in the event of a breach. Together, these evolutions represent a fundamental redefinition of security posture, with a proactive, risk-adaptive mindset supplanting the reactive, signature-based models of the past.
Assessing the Broad Ramifications of 2025 United States Tariffs on Remote Work Security Supply Chains and Cost Structures
The culmination of United States tariffs enacted in 2025 has exerted significant pressure on the remote work security supply chain, influencing both upstream hardware costs and downstream service delivery economics. Tariffs on semiconductor components, networking equipment, and security appliances have incrementally increased the capital expenditure associated with deploying advanced endpoint protection devices and next-generation firewalls. Cloud service providers have also grappled with import levies on servers and storage arrays, leading to selective price adjustments in subscription rates and service-level commitments. These cost pressures have compelled security teams to reexamine hardware refresh cycles and explore software-defined alternatives that can mitigate tariff-induced capital burdens.
In response to these fiscal headwinds, many organizations have shifted toward strategic sourcing from regions exempt from specific levies, while others have accelerated deployment of virtualized and containerized security functions to reduce reliance on physical appliances. The evolving tariff environment has also spurred innovation in consumption-based licensing models, enabling enterprises to align security spending more closely with actual usage and budgetary constraints. Concurrently, service integrators and managed security providers have adapted packaging and bundling approaches, embedding hardware-agnostic solutions to circumvent tariff pass-through and maintain pricing stability for their remote workforce customers. These cumulative impacts underscore the need for agile procurement and deployment strategies in the face of geopolitical trade shifts.
Dissecting Deep Segmentation Insights Across Solutions Deployment Modes Industry Verticals and Enterprise Sizes Nuanced Perspectives
The remote work security ecosystem can be dissected through multiple lenses to uncover nuanced growth opportunities and adoption barriers. A solution type segmentation reveals that organizations are increasingly investing in cloud security offerings, including both cloud access security brokers that govern data flows and cloud workload protection platforms that secure containerized environments. Data loss prevention mechanisms are evolving to address both endpoint and network contexts, ensuring sensitive information is protected whether it resides on user devices or traverses corporate networks. Endpoint protection has advanced beyond traditional antivirus to encompass sophisticated detection and response capabilities, while identity and access management solutions leverage multi-factor authentication and single sign-on frameworks to streamline user experiences without sacrificing control. Simultaneously, network security approaches blend virtual private networking technologies with zero trust network access models, and security information and event management systems now integrate log management with real-time analytics to accelerate incident investigation.
Deployment mode further differentiates segmentation outcomes, as pure cloud-native solutions compete with hybrid architectures that balance on-premises infrastructures and fully managed services. In parallel, industry vertical segmentation highlights unique requirements across sectors such as banking, capital markets and insurance within the financial services domain; civilian and defense agencies in government; hospitals, medical devices, and pharmaceutical companies in healthcare; IT service providers and telecom carriers; automotive and electronics manufacturers; and both brick-and-mortar and ecommerce retail operators. Finally, organizational size segmentation distinguishes between the security practices of large enterprises with dedicated security operations centers and small and medium enterprises that often rely on managed services partners for 24/7 monitoring. These combined perspectives offer a comprehensive view of where demand is strongest and where specialized approaches are needed to address varied risk profiles.
This comprehensive research report categorizes the Remote Work Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Solution Type
- Deployment Mode
- Organization Size
- Industry Vertical
Illuminating Critical Regional Variations and Security Adaptation Trends Across Americas Europe Middle East Africa and Asia Pacific
Regional dynamics play a pivotal role in shaping remote work security priorities and solution preferences. The Americas exhibit a robust appetite for cloud-centric security services, driven by progressive data privacy regulations and mature technology infrastructures. North American enterprises are at the forefront of adopting advanced endpoint detection and response platforms, while Latin American markets are rapidly scaling managed security services to offset talent shortages. Regulatory bodies across the region emphasize data sovereignty and incident reporting requirements, prompting organizations to implement granular controls and robust auditing capabilities.
Across Europe, the Middle East, and Africa, compliance with stringent frameworks such as the General Data Protection Regulation and the emerging NIS2 directives is driving investment in identity governance and unified security orchestration. Enterprises in this region navigate a complex web of cross-border data transfer rules and localization mandates, leading to a preference for hybrid deployment models that combine local data processing with centralized threat intelligence. In contrast, Asia-Pacific markets are characterized by rapid digital transformation initiatives and government-backed cybersecurity programs. From mature economies implementing zero trust strategies to emerging markets adopting foundational endpoint protection, the region as a whole demonstrates accelerating demand for scalable, cost-effective solutions that can adapt to diverse infrastructure environments.
This comprehensive research report examines key regions that drive the evolution of the Remote Work Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Revealing Competitive Dynamics and Strategic Initiatives Driving Leading Security Vendors and Innovative Market Entrants
Leading cybersecurity vendors have embarked on strategic initiatives to solidify their positions in the remote work security domain. Established players are extending platform-based capabilities, integrating endpoint detection and response with cloud workload security, and offering unified policy management across hybrid environments. Strategic acquisitions and partnerships are fueling this consolidation, enabling vendors to embed artificial intelligence analytics into their portfolios and provide threat hunting services that leverage global telemetry. New entrants and specialized providers are challenging traditional models by delivering nimble, API-driven solutions that interoperate with existing stacks and emphasize modularity and rapid deployment.
Startups focusing on zero trust network access and cloud-native security are gaining traction by addressing niche requirements and offering consumption-based pricing models. Meanwhile, incumbent technology providers are investing heavily in research and development to introduce automated threat remediation, proactive vulnerability management, and community-driven security intelligence sharing. This dual dynamic of consolidation among feature-rich platforms and disruption by lean innovators is reshaping vendor landscapes and creating a highly competitive environment in which differentiation hinges on interoperability, ease of deployment, and the ability to deliver measurable risk reduction for remote workforces.
This comprehensive research report delivers an in-depth overview of the principal market players in the Remote Work Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Alphabet Inc.
- Broadcom Inc
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Holdings, Inc.
- CyberArk Software Ltd.
- Fortinet, Inc.
- IBM Corporation
- Ivanti, Inc.
- McAfee, LLC
- Microsoft Corporation
- Okta, Inc.
- Palo Alto Networks, Inc.
- Proofpoint, Inc.
- RSA Security LLC
- Sophos Group plc
- Splunk Inc.
- Tenable Holdings, Inc.
- Trend Micro Incorporated
- VMware, Inc.
- Zscaler, Inc.
Actionable Strategic Directives for Security Leaders to Enhance Remote Workforce Protection Posture and Foster Organizational Cyber Resilience
Industry leaders seeking to fortify their remote workforce protection posture should prioritize the implementation of a zero trust security framework that continuously verifies user and device trust levels. By decomposing monolithic security perimeters into micro-segmented environments and enforcing least-privilege access policies, organizations can significantly reduce the attack surface and limit lateral movement in the event of a breach. Complementing this approach with adaptive authentication mechanisms that assess risk scores in real time helps maintain a seamless user experience while elevating security posture. Furthermore, integrating endpoint detection and response tools with centralized security analytics allows for accelerated threat detection and automated incident response orchestrations.
In addition to technology investments, governance and culture are paramount. Establishing a security-first mindset through regular simulated phishing exercises, targeted awareness training, and clear incident reporting procedures cultivates employee vigilance. Operational resilience is further enhanced by adopting cloud-native encryption services, leveraging managed security service providers for continuous monitoring, and developing playbooks for remote incident handling. By aligning budgetary allocations with risk priorities and fostering cross-functional collaboration between IT, security, and business units, organizations can create a cohesive defense ecosystem that adapts dynamically to evolving remote work demands.
Outlining Robust Research Methodologies and Analytical Frameworks Underpinning the Comprehensive Remote Work Security Study
This research employs a multi-tiered methodology to ensure the robustness and reliability of findings. Primary data collection included in-depth interviews and structured surveys with security decision-makers across a diverse set of industries, providing qualitative insights into challenges, adoption drivers, and investment priorities. Secondary research integrated analysis of public financial disclosures, vendor white papers, regulatory guidelines, and industry consortium reports to validate emerging trends and benchmark technological capabilities. Data triangulation techniques were applied to cross-verify information from distinct sources, mitigating biases and enhancing the overall credibility of conclusions.
Quantitative analysis incorporated statistical modeling of deployment patterns, vendor performance metrics, and technology adoption curves reported by research participants. Expert panels comprising cybersecurity practitioners and thought leaders were convened to review draft findings and refine recommendations. Finally, iterative validation workshops ensured that the analytical frameworks and segmentation matrices accurately reflect real-world use cases and evolving threat landscapes. This rigorous approach underpins the comprehensive mapping of remote work security requirements and the actionable insights presented throughout this executive summary.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Remote Work Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Remote Work Security Market, by Solution Type
- Remote Work Security Market, by Deployment Mode
- Remote Work Security Market, by Organization Size
- Remote Work Security Market, by Industry Vertical
- Remote Work Security Market, by Region
- Remote Work Security Market, by Group
- Remote Work Security Market, by Country
- United States Remote Work Security Market
- China Remote Work Security Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 2703 ]
Synthesizing Key Takeaways and Forward Looking Perspectives to Guide Strategic Decisions in Remote Work Security Management
In synthesizing the key takeaways from this comprehensive study, it becomes evident that remote work security is no longer an auxiliary governance consideration but a strategic imperative. Organizations that embrace identity-centric frameworks, deploy advanced endpoint and cloud security capabilities, and adopt zero trust principles will be best positioned to navigate the complexities of a distributed workforce environment. Moreover, the evolving landscape of tariffs and supply chain constraints underscores the importance of flexible procurement strategies and software-defined solutions that can absorb market volatility.
Looking ahead, the convergence of artificial intelligence-driven threat prevention, unified security orchestration, and continuous learning loops will define the next frontier in securing remote operations. Decision-makers are encouraged to leverage the segmentation insights and regional analyses outlined in this summary to craft tailored roadmaps that align with their unique risk profiles, regulatory contexts, and organizational maturity. By fostering a culture of continuous improvement and strategic foresight, enterprises can transform their remote work security posture from a defensive necessity into a competitive advantage.
Engage With Ketan Rohom Today to Secure Exclusive Insights and Empower Your Organization With Tailored Remote Work Security Intelligence
To gain deeper visibility into the transformative dynamics shaping remote work security and to unlock targeted strategies tailored to your organization’s specific needs, we invite you to engage with Ketan Rohom, Associate Director of Sales & Marketing. Ketan brings extensive expertise in cybersecurity research and can guide you through the comprehensive market analysis, detailed segmentation matrices, and forward-looking recommendations contained in the full report. This personalized consultation will help you identify actionable levers, anticipate emerging risks, and optimize your security investments for sustained resilience.
Contact Ketan today to secure exclusive access to the detailed findings and frameworks that have been meticulously developed for security leaders operating in hybrid and fully remote environments. Embark on a strategic partnership that empowers your team to stay ahead of evolving threats and to build a future-proof security posture. Reach out now to explore tailored engagement options, obtain sample chapters, and discuss how this in-depth research can accelerate your remote work security roadmap.

- How big is the Remote Work Security Market?
- What is the Remote Work Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




