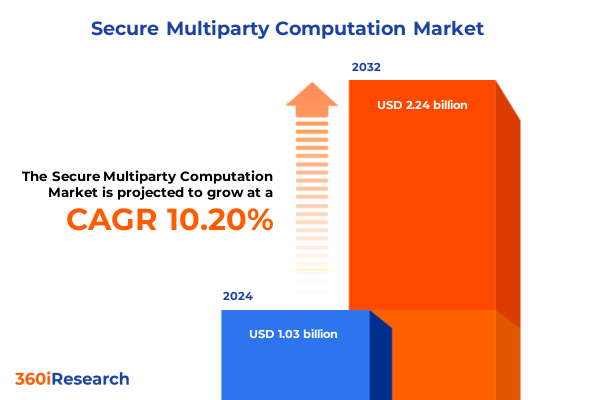
The Secure Multiparty Computation Market size was estimated at USD 1.67 billion in 2025 and expected to reach USD 1.87 billion in 2026, at a CAGR of 12.07% to reach USD 3.72 billion by 2032.
Unveiling the Strategic Imperative of Secure Multiparty Computation in Today’s Data Privacy Frameworks That Enable Confidential Collaborative Analytics Across Distributed Systems
Secure Multiparty Computation (SMPC) has evolved from an academic curiosity into a foundational element of enterprise data privacy strategies. As organizations grapple with increasingly stringent data protection regulations and rising concerns over data breaches, SMPC offers a paradigm in which multiple parties can collaboratively compute functions over their private inputs without revealing the underlying data to one another. This capability not only mitigates regulatory and reputational risk but also unlocks new avenues for cross-organizational analytics, enabling joint ML model training and private data sharing at unprecedented levels.
In today’s interconnected digital environment, businesses across banking, healthcare, telecommunications, and government are recognizing the transformative power of SMPC to facilitate secure multiparty workflows. From federated learning initiatives that enhance model accuracy without exposing proprietary datasets, to encrypted auctions that preserve confidentiality in competitive bidding, SMPC underpins a broad spectrum of applications. Moreover, advancements in homomorphic encryption schemes and optimized garbled circuit protocols have significantly reduced computational overhead, making SMPC viable for real-time and large-scale deployments.
As data ecosystems grow more complex, the imperative for robust privacy preserving technologies intensifies. In this context, SMPC stands out as a forward-looking solution that not only addresses current privacy and security challenges but also anticipates the evolving demands of digital collaboration. This report provides an in-depth executive overview of SMPC’s market dynamics, strategic implications, and key success factors, equipping decision-makers with the insights necessary to champion secure, data-driven innovation.
Mapping the Technological and Regulatory Evolution That’s Propelling Secure Multiparty Computation into Enterprise-Scale Deployments
Over the past several years, the Secure Multiparty Computation landscape has undergone dramatic shifts driven by both technological breakthroughs and evolving regulatory landscapes. Early SMPC implementations were largely confined to academic research and pilot projects, constrained by significant computational and network latency barriers. However, recent progress in algorithmic optimizations-such as improved garbled circuit constructions, more efficient secret sharing techniques, and schemes for approximate homomorphic encryption-has markedly enhanced performance, pushing the envelope for practical enterprise adoption.
Concurrently, global data governance regulations, including GDPR in Europe and CCPA in the United States, have incentivized enterprises to explore privacy enhancing technologies that can demonstrate compliance without impeding data utility. This regulatory impetus, coupled with growing awareness of competitive data collaborations, has fueled investments in SMPC protocols that integrate seamlessly with existing data architectures. Notably, the emergence of hybrid deployment models, which combine on premises secure enclaves with cloud-based orchestration, exemplifies the transformative shift toward scalable, flexible SMPC solutions.
Moreover, partnerships between cryptographic research labs and technology vendors have accelerated the transition from proof-of-concept to production-grade platforms. Open source frameworks and interoperable standards are now fostering a vibrant ecosystem, enabling rapid innovation while reducing vendor lock-in. As SMPC moves progressively from the fringes into the mainstream of enterprise security architectures, organizations that align early with these transformative shifts will be best positioned to harness the full potential of collaborative privacy preserving computing.
Analyzing the Dual Impact of 2025 US Tariffs on Cryptographic Hardware and the Adaptive Strategies Shaping SMPC Implementations
In 2025, United States tariffs on hardware components and specialized cryptographic accelerators have introduced new considerations for organizations implementing SMPC solutions. These duties, aimed at protecting domestic semiconductor production, have increased the cost of acquiring advanced secure hardware modules and high-performance GPUs essential for accelerating homomorphic operations and large-scale garbled circuit evaluations.
Consequently, solution providers and enterprises have recalibrated investment strategies, exploring alternative hardware sourcing and optimizing protocol designs to reduce dependency on expensive accelerators. Some vendors have responded by developing hardware-agnostic SMPC libraries that leverage general-purpose CPUs with vectorized instructions, mitigating tariff-induced cost pressures. Additionally, the adoption of cloud-based SMPC offerings hosted in domestic data centers has surged, as it allows businesses to sidestep import tariffs while maintaining performance SLAs.
Despite these headwinds, the tariff landscape has also prompted strategic collaborations between US-based cryptography companies and domestic hardware manufacturers to co-develop custom secure compute modules. Such partnerships aim to deliver tariff-exempt solutions that conform to federal procurement standards, particularly in government defense and critical infrastructure sectors. As a result, the net impact of 2025 tariffs has been dual: while raising near-term implementation costs, they have catalyzed innovation in hardware flexibility and supply chain resilience within the SMPC ecosystem.
Unraveling Key Segmentation Insights Revealing How Components, Protocol Types, Deployment Patterns, Organizational Scale, Applications, and Sectors Shape SMPC Adoption
Insights into SMPC adoption reveal that enterprises are strategically prioritizing end-to-end solutions that encompass both services and technology platforms. Organizations investing in consulting services to architect secure workflows often complement these engagements with implementation services that integrate hardware solutions and software solutions suited to their unique environments. The technology landscape itself bifurcates into hardware accelerators, purpose-built for encryption workloads, and software solutions that deliver protocol stacks run on flexible compute infrastructures.
From a cryptographic standpoint, market uptake is concentrated around three core protocol families: garbled circuits, homomorphic encryption, and secret sharing. Garbled circuits have gained traction for two-party computations requiring low communication overhead, while homomorphic encryption’s ability to perform arithmetic on encrypted data appeals to analytics-driven use cases. Secret sharing remains a foundational approach for multi-party collaboration, prized for its simplicity and resilience against direct data leakage.
Deployment preferences further segment into cloud, hybrid, and on premises models. Within cloud deployments, private cloud environments maintain proprietary control over data, whereas public cloud offerings attract organizations seeking cost efficiency and elasticity. Hybrid architectures, balancing on premises secure enclaves with cloud orchestration, have emerged as a versatile middle ground. Meanwhile, organizational size influences adoption curves: large enterprises often lead with sizeable proof-of-concept investments, whereas small and medium enterprises favor turnkey solutions with managed service components.
Finally, the spectrum of applications-from federated learning to privacy preserving data sharing, private set intersection, and secure auction mechanisms-underscores SMPC’s versatility across diverse business challenges. Industry verticals drive unique requirements: banking and financial services leverage secure auctions and federated credit scoring, energy and utilities focus on joint grid analytics, government and defense prioritize secure workflows, healthcare and life sciences converge on patient data sharing, IT and telecommunications optimize network insights, and retail and e-commerce enhance personalized recommendations without compromising consumer privacy.
This comprehensive research report categorizes the Secure Multiparty Computation market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Offering
- Type
- Technique
- Security Model Type
- Data Modality
- Commercial Model
- Use Case
- Industry Vertical
- Deployment Mode
- Organization Size
Exploring How Regional Regulatory Regimes, Investment Ecosystems, and Infrastructure Maturity Drive Distinct SMPC Adoption Patterns Across Major Global Markets
Regional dynamics play a pivotal role in SMPC adoption, with distinct factors influencing activity across the Americas, Europe, Middle East & Africa, and Asia-Pacific. In the Americas, robust venture funding and a growing culture of privacy-centric innovation have fueled rapid deployment of SMPC solutions, particularly within financial services and healthcare sectors. The ease of integration with leading cloud service providers headquartered in the region further accelerates uptake among early adopters.
Across Europe, Middle East & Africa, stringent data sovereignty regulations and the General Data Protection Regulation (GDPR) have created fertile ground for SMPC, as organizations seek to collaborate across borders without risking compliance breaches. Public sector initiatives and cross-national research consortia have pioneered federated analytics projects, highlighting the region’s leadership in privacy-preserving data collaborations.
Asia-Pacific exhibits a blend of state-sponsored digital transformation programs and expanding commercial interest, particularly in markets such as China, Japan, and Australia. Governments are exploring SMPC for secure citizen data aggregation, while private enterprises in telecommunications and retail are capitalizing on the region’s advanced telecom infrastructure to deploy cutting-edge SMPC use cases. Hybrid cloud models are especially prevalent, balancing global cloud service access with local data residency requirements.
Collectively, these regional insights underscore the importance of tailored go-to-market strategies that account for regulatory landscapes, cloud adoption maturity, and industry-specific use cases. As a result, solution providers are forging localized partnerships and compliance frameworks to effectively navigate the unique market drivers in each geography.
This comprehensive research report examines key regions that drive the evolution of the Secure Multiparty Computation market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Distilling the Competitive Landscape Where Technical Differentiation, Service Excellence, and Regulatory Compliance Define SMPC Market Leadership
The SMPC vendor ecosystem is characterized by a dynamic mix of established cryptographic specialists, cloud service providers, and emerging startups. Leading cryptography firms have expanded portfolios to include turnkey SMPC platforms, integrating accelerators and managed services to address enterprise demands for end-to-end solutions. Cloud providers have augmented their security suites with native SMPC offerings, leveraging global data centers to deliver scalable and compliant environments.
In parallel, a new wave of startups is disrupting the market with niche innovations-ranging from optimized secret sharing libraries for real-time financial computations to AI-focused homomorphic encryption toolkits that streamline federated learning deployments. Strategic partnerships and private equity investments have consolidated capabilities, as traditional security vendors acquire or ally with SMPC pioneers to bolster their privacy enhancing technology roadmaps.
Competitive differentiation increasingly revolves around performance benchmarking, interoperability standards, and professional service capabilities. Vendors demonstrating measurable efficiency gains in protocol execution or offering turnkey integration with enterprise data platforms have gained a competitive edge. Additionally, certifications such as Common Criteria and FIPS validation are becoming critical decision factors for regulated industries seeking assurance of robust cryptographic implementations.
These dynamics underscore a maturing market in which vendor viability hinges on a balanced combination of technical excellence, service delivery proficiency, and regulatory compliance expertise. As enterprises expand their SMPC use cases, the ability to navigate complex procurement processes and deliver demonstrable return on privacy will define market leadership.
This comprehensive research report delivers an in-depth overview of the principal market players in the Secure Multiparty Computation market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Microsoft Corporation
- International Business Machines Corporation
- Google LLC by Alphabet Inc.
- Amazon Web Services, Inc.
- Alibaba Group Holding Limited
- Intel Corporation
- Meta Platforms, Inc.
- Fireblocks Inc.
- Blockdaemon Inc.
- NTT, Inc.
- Circle Internet Financial, LLC
- NEC Corporation
- Oracle Corporation
- Penta Security Inc.
- Sharemind by Cybernetica AS
- Qredo Services Ltd.
- PayPal Holdings, Inc.
- Inpher
- Wipro Limited
- Zengo Ltd.
- Duality Technologies Inc.
- Roseman Labs B.V.
- Binance Group
- Coinbase Global, Inc.
- DuoKey SA
- Enveil, Inc.
- Fortanix Inc.
- Linksight B.V.
- Partisia Blockchain Foundation
- SAP SE
- Stealth Software Technologies, Inc.
- Taurus SA
Implementing Structured Pilots, Centers of Excellence, and Regulatory Engagement to Propel Enterprise-Wide Adoption of Privacy Enhancing Computation
To navigate the complexities of SMPC implementation and derive maximum value, industry leaders should adopt a multipronged strategy. First, investing in pilot programs with clearly defined performance and security benchmarks will enable rapid validation of protocol suitability for enterprise use cases. Collaborations with cryptography research centers can accelerate customization of SMPC workflows, ensuring alignment with organizational data governance frameworks.
Second, building a center of excellence for privacy enhancing technologies fosters cross-functional expertise and drives consistent best practices. By establishing governance mechanisms that encompass legal, IT, and business stakeholders, organizations can streamline decision-making and ensure that SMPC initiatives are integrated with broader digital transformation agendas. This holistic approach reduces implementation risks and promotes reusable architectural patterns.
Third, proactive engagement with regulatory bodies and standards organizations will help shape favorable compliance pathways and interoperability frameworks. Participating in industry consortia and open source communities accelerates knowledge sharing and positions enterprises at the forefront of emerging protocols. Finally, leaders should explore diversified deployment models-including hybrid cloud and domestic-hosted solutions-to optimize cost structures, regulatory alignment, and performance outcomes.
By executing these actionable recommendations, organizations can transcend proof-of-concept inertia, drive enterprise-wide adoption, and secure a sustainable competitive advantage through advanced privacy preserving computing.
Leveraging Mixed-Method Primary Interviews, Quantitative Surveys, and Technical Benchmarking to Deliver a Comprehensive SMPC Market Research Report
The research methodology underpinning this report combines a rigorous primary and secondary research approach to ensure accuracy and depth. Extensive secondary research included analysis of industry publications, white papers, patent filings, and regulatory frameworks to map the current state of SMPC technologies and best practices. Proprietary databases and technical benchmarks were consulted to identify leading protocols, vendor capabilities, and hardware acceleration trends.
Primary research involved in-depth interviews with key stakeholders, including chief privacy officers, cryptography researchers, solution architects, and CTOs across financial services, healthcare, government, telecommunications, and retail sectors. These qualitative insights provided real-world perspectives on deployment challenges, performance expectations, and strategic priorities. Quantitative surveys supplemented these interviews, capturing data on protocol adoption rates, preferred deployment models, and investment drivers.
A comprehensive segmentation analysis was conducted across components, protocol types, deployment modes, organizational sizes, applications, and industry verticals to reveal nuanced adoption patterns. Regional market assessments leveraged geopolitical and regulatory intelligence to contextualize growth dynamics. Competitive profiling combined vendor self-reported performance metrics with independent technical evaluations to ensure an unbiased view of the SMPC vendor landscape.
This mixed-method approach ensures that the report not only reflects the latest market trends and technological advancements but also provides actionable insights grounded in the realities of enterprise deployment and vendor capabilities.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Secure Multiparty Computation market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Secure Multiparty Computation Market, by Offering
- Secure Multiparty Computation Market, by Type
- Secure Multiparty Computation Market, by Technique
- Secure Multiparty Computation Market, by Security Model Type
- Secure Multiparty Computation Market, by Data Modality
- Secure Multiparty Computation Market, by Commercial Model
- Secure Multiparty Computation Market, by Use Case
- Secure Multiparty Computation Market, by Industry Vertical
- Secure Multiparty Computation Market, by Deployment Mode
- Secure Multiparty Computation Market, by Organization Size
- Secure Multiparty Computation Market, by Region
- Secure Multiparty Computation Market, by Group
- Secure Multiparty Computation Market, by Country
- United States Secure Multiparty Computation Market
- China Secure Multiparty Computation Market
- Competitive Landscape
- List of Figures [Total: 22]
- List of Tables [Total: 2226 ]
Summarizing the Convergence of Technological Maturity, Regulatory Imperatives, and Strategic Actions Driving SMPC’s Mainstream Adoption
The SMPC market stands at a pivotal juncture where technological maturity intersects with escalating privacy and compliance demands. As performance enhancements and innovative deployment models reduce barriers to entry, organizations across industries have unprecedented opportunities to collaborate on sensitive data without sacrificing confidentiality. From federated learning in healthcare to encrypted data sharing in finance, the versatility of SMPC continues to expand the frontier of privacy preserving applications.
US tariffs on specialized cryptographic hardware have introduced new supply chain considerations, but they have also spurred adaptive strategies that enhance resilience and foster domestic innovation in secure computing modules. The segmentation insights underscore the importance of tailored solutions-from consulting and implementation services to hardware and software platforms-aligned with enterprise size, preferred protocols, and industry-specific requirements. Regional dynamics further highlight the need for localized compliance and go-to-market strategies in the Americas, Europe, Middle East & Africa, and Asia-Pacific.
Vendor competition is sharpening around protocol performance, interoperability, and comprehensive service offerings, underscoring the value of certifications and strategic partnerships in regulated environments. To capitalize on the transformative potential of SMPC, industry leaders must implement structured pilot programs, establish dedicated centers of excellence, and proactively engage with regulators and standards bodies. This holistic approach will enable organizations to transcend initial proof-of-concepts and scale privacy preserving computing throughout their operations.
In conclusion, SMPC is poised to become an integral component of tomorrow’s data privacy architectures, empowering enterprises to unlock collaborative analytics, drive innovation, and maintain rigorous confidentiality standards in a data-driven world.
Seize Competitive Advantage with a Customized Multiparty Computation Market Intelligence Report by Connecting with Our Sales Leadership
Embrace the future of data security and innovation by securing your comprehensive Secure Multiparty Computation market research report today. Engage directly with Ketan Rohom, Associate Director of Sales & Marketing, to unlock tailored insights that will empower your strategic decisions and accelerate your competitive advantage. Reach out now to schedule a personalized consultation and discover how implementing advanced collaborative encryption techniques can revolutionize your data privacy initiatives and drive sustainable growth.

- How big is the Secure Multiparty Computation Market?
- What is the Secure Multiparty Computation Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




