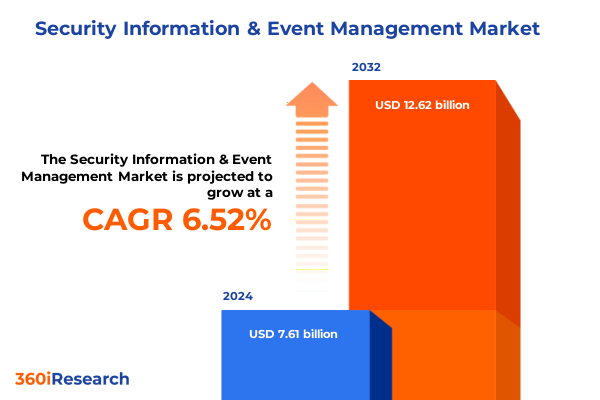
The Security Information & Event Management Market size was estimated at USD 8.09 billion in 2025 and expected to reach USD 8.60 billion in 2026, at a CAGR of 6.55% to reach USD 12.62 billion by 2032.
An overview of how Security Information and Event Management underpins organizational resilience through proactive monitoring and rapid incident response
Security Information and Event Management has become foundational for organizations striving to maintain operational continuity and safeguard critical assets. Through the integration of real-time monitoring, threat detection, and rapid response workflows, SIEM empowers teams to identify anomalous behavior before incidents escalate. This section introduces the core principles that define SIEM, highlighting its role in aggregating log data from disparate systems, normalizing events, and correlating insights across complex infrastructures.
As cyber threats evolve in sophistication, the ability to unify security telemetry under a single pane of glass delivers unparalleled visibility. SIEM platforms now extend beyond simple log collection; they incorporate orchestration and automation to streamline incident response, reducing mean time to detect and resolve breaches. Furthermore, the convergence of SIEM with broader security operations strategies fosters a proactive stance, where historical analysis and predictive modeling anticipate adversary tactics before exploitation.
Transitioning from traditional perimeter defenses to an intelligence-driven paradigm, SIEM has emerged as a strategic asset rather than a compliance checkbox. Organizations leverage its contextual analytics to inform governance, risk management, and compliance programs, weaving security considerations into everyday operations. Ultimately, this introduction sets the stage for a deeper analysis of transformative trends, economic headwinds, and actionable insights that drive SIEM adoption across industries.
A deep exploration of the transformative technological and operational developments reshaping the Security Information and Event Management landscape in 2025
The Security Information and Event Management landscape in 2025 has been reshaped by rapid technological innovation and shifting operational priorities. Artificial intelligence and machine learning have matured to automate routine correlation tasks, enabling security teams to focus on high-impact investigations. This infusion of automation accelerates threat detection and triage, reduces alert fatigue, and enhances the precision of predictive analytics, ultimately transforming SIEM from a reactive tool into an anticipatory defense mechanism.
Simultaneously, the surge in hybrid and multi-cloud architectures has challenged traditional data collection models. Organizations now require SIEM solutions capable of ingesting telemetry from cloud workloads, containers, and serverless environments without compromising performance or scalability. In response, vendors have developed lightweight collectors and native integrations to streamline ingestion pipelines, ensuring comprehensive coverage across dynamic infrastructures.
Moreover, the rise of extended detection and response capabilities has sparked demand for SIEM platforms that integrate seamlessly with endpoint, network, and identity solutions. This convergence fosters unified incident management, enabling analysts to pivot across telemetry sources and orchestrate cross-domain remediation. These transformative shifts reflect a broader industry imperative: to evolve SIEM from a siloed log repository into a centralized command center that drives real-time, intelligence-led security operations.
An in-depth examination of how the 2025 United States tariffs have compounded challenges and driven strategic adjustments within Security Information and Event Management deployments
The imposition of new United States tariffs in early 2025 has introduced additional complexities for organizations deploying Security Information and Event Management systems. As hardware costs for high-performance log collectors and dedicated analytics appliances have risen, procurement teams have been forced to reassess budget allocations. These elevated expenses have prompted a shift toward software-centric and subscription-based deployment models, mitigating capital outlays associated with on-premise infrastructure.
Tariffs on imported security appliances have also disrupted vendor supply chains, extending lead times for critical components. In response, several SIEM providers have diversified their manufacturing footprints, leveraging regional partners and localized assembly to cushion the impact of trade barriers. This structural adjustment underscores a growing emphasis on supply-chain resilience, with organizations prioritizing vendors that maintain flexible sourcing and transparent logistics practices.
Beyond hardware implications, the broader economic reverberations of trade policies have fueled tighter operational budgets, driving heightened scrutiny of license utilization and platform consolidation. Security leaders now demand demonstrable ROI, emphasizing integration with existing toolsets and cross-platform analytics to justify incremental investments. Consequently, the tariff-induced cost pressures have spurred innovation in licensing flexibility, cloud migration incentives, and managed service offerings, collectively reshaping the commercial dynamics of the SIEM ecosystem.
A comprehensive analysis of critical market segmentation dimensions revealing differentiated demands across service offerings, log types, deployment preferences, organization sizes, and verticals
A nuanced understanding of the SIEM landscape emerges when evaluating the market across multiple segmentation dimensions. When examining offerings, organizations often navigate between services and solutions, with service engagements spanning implementation and deployment through managed security services to ongoing support and maintenance, while solution portfolios include core capabilities such as log management and reporting alongside security analytics and threat intelligence modules. This duality enables enterprises to tailor their investments to both project-based requirements and continuous security operations.
Log type segmentation further differentiates needs, as endpoint logs demand high-velocity collection and contextualization, IoT logs introduce a diversity of format and volume considerations, perimeter device logs require real-time alerting, and Windows event logs necessitate deep integration with identity and access management processes. Each log category carries unique ingestion, normalization, and retention challenges, compelling organizations to adopt flexible SIEM architectures that accommodate heterogeneous data streams.
Deployment type distinctions influence architectural choices, with cloud-based implementations offering elasticity and rapid provisioning while on-premise installations provide greater control over sensitive data. Organization size also shapes priorities: large enterprises often pursue full-spectrum managed offerings to centralize operations, whereas small and medium enterprises prioritize cost-effective, scalable solutions requiring minimal in-house administrative overhead. Finally, industry verticals-from BFSI to healthcare, manufacturing to retail trade-impose specific compliance mandates and threat landscapes, driving customized SIEM configurations that align with regulatory frameworks and sector-specific attack vectors.
This comprehensive research report categorizes the Security Information & Event Management market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Offering
- Log Type
- Deployment Type
- Organization Size
- Industry Verticals
An insightful regional breakdown highlighting distinct adoption trends, regulatory considerations, and innovation drivers across the Americas, Europe, Middle East & Africa, and Asia-Pacific markets
Regional dynamics underscore diverse SIEM adoption patterns shaped by regulatory environments, threat landscapes, and economic drivers. In the Americas, mature compliance frameworks and thriving cybersecurity ecosystems have accelerated investments in advanced analytics and orchestration, with many organizations leveraging managed detection and response partnerships to augment in-house capabilities. The regional focus on privacy legislation has also amplified the importance of robust log retention and audit trails.
Across Europe, the Middle East, and Africa, a patchwork of data protection regulations has driven demand for customizable SIEM configurations that address cross-border governance requirements. regional innovation hubs, particularly within emerging markets, are capitalizing on advances in threat intelligence sharing and localized threat feed integrations. Additionally, geopolitical tensions have heightened interest in secure supply chains and vendor diversification strategies throughout the EMEA corridor.
The Asia-Pacific region presents a dual narrative of rapid digital transformation and evolving regulatory oversight. High-growth markets have embraced cloud-based SIEM offerings to facilitate agile deployments, while established economies emphasize integration with national cybersecurity initiatives. Moreover, increasing collaboration between public-sector agencies and private enterprises has fostered intelligence exchange frameworks that enhance SIEM enrichment, driving continuous improvements in detection accuracy and incident coordination across the region.
This comprehensive research report examines key regions that drive the evolution of the Security Information & Event Management market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
A detailed review of leading vendors and emerging players in the Security Information and Event Management sector, focusing on strategic strengths, partnerships, and innovation efforts
Leading SIEM providers continue to differentiate through product innovation, strategic partnerships, and service excellence. Established vendors are enhancing their analytics engines with built-in machine learning algorithms that detect subtle indicators of compromise, while forging integrations with extended detection and response platforms to deliver holistic security operations capabilities. These alliances expand coverage across endpoints, networks, cloud workloads, and identity systems, enabling seamless investigation and remediation workflows.
Emerging players are carving niche positions by specializing in containerized environments, IoT telemetry, or privacy-centric deployments that align with stringent data sovereignty mandates. Their agile development cycles facilitate rapid feature releases, often outpacing legacy platform upgrade cadences. Partnerships with managed service providers and value-added resellers further broaden their market reach, particularly among organizations seeking turnkey security event management solutions with minimal in-house overhead.
Strategic acquisitions have also reshaped vendor landscapes, consolidating capabilities across analytics, orchestration, and threat intelligence. These transactions have enabled comprehensive packaged offerings, combining core SIEM functionality with adjacent security services. Buyers are increasingly evaluating vendor roadmaps for post-acquisition integration efficiency, seeking assurance that innovation pipelines remain robust and customer support channels uninterrupted.
This comprehensive research report delivers an in-depth overview of the principal market players in the Security Information & Event Management market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Adlumin Inc.
- AT&T Inc.
- Blacklight by Cyberphage Limited
- Broadcom Inc.
- Core To Cloud Limited
- Datadog, Inc.
- Dell Technologies Inc.
- Devo Technology Inc.
- Elastic N.V.
- Exabeam, Inc.
- Fortinet, Inc.
- Fortra, LLC
- Google LLC by Alphabet Inc.
- International Business Machines Corporation
- Logpoint A/S
- Logsign
- Lumifi Cyber, Inc.
- McAfee Corp.
- Microsoft Corporation
- NetWitness LLC
- NTT DATA INTELLILINK Corporation
- OpenText Corporation
- Oracle Corporation
- Palo Alto Networks, Inc.
- Rapid7, Inc.
- SAP SE
- Seceon Inc.
- Securonix, Inc.
- SilverSky Inc. by BAE Systems PLC
- Snowflake Inc.
- Solutions Granted, Inc.
- Splunk Inc. by Cisco Systems, Inc.
- Sumo Logic, Inc.
- Trellix by Symphony Technology Group
- Trend Micro Inc.
- Trustwave Holdings
- Verizon Communications Inc.
- Wazuh, Inc.
- Zoho Corporation Pvt. Ltd.
Strategic guidance for industry leaders to drive optimized Security Information and Event Management practices through proactive governance, advanced analytics, and ecosystem collaboration
To capitalize on the evolving SIEM landscape, industry leaders should prioritize a governance framework that aligns security monitoring objectives with overarching business goals. This entails establishing clear metrics for detection efficacy and response timeliness, then integrating those benchmarks into executive dashboards to secure sustained investment. Deploying continuous improvement cycles will ensure that SIEM configurations adapt to emerging threats and shifting compliance requirements.
Leaders must also embrace advanced analytics by investing in artificial intelligence and machine learning models that reduce manual triage. By automating routine correlation tasks and alert prioritization, security teams can allocate resources to complex investigations, threat hunting, and strategic initiatives. Collaborative integrations with endpoint detection, network security, and identity management systems will further amplify the ROI of SIEM platforms through unified incident workflows.
Finally, fostering an ecosystem of trusted partners can mitigate resource constraints and accelerate time to value. Engaging managed detection and response providers, threat intelligence vendors, and systems integrators enables organizations to leverage specialized expertise and scale their security operations efficiently. By orchestrating cross-domain capabilities and cultivating external alliances, industry leaders can transform SIEM from a point solution into a strategic enabler of organizational resilience.
An explanation of the rigorous research approach combining primary interviews, secondary data analysis, and validation processes to ensure authoritative Security Information and Event Management insights
This research synthesized insights from structured interviews with chief information security officers, security operations center managers, and compliance officers across multiple industries. In parallel, secondary data sources-including regulatory filings, industry whitepapers, and open-source threat intelligence reports-were analyzed to validate emerging trends and identify cross-sector commonalities. The methodology emphasized data triangulation to ensure that conflicting signals were reconciled through iterative review cycles.
To augment qualitative insights, vendor briefings provided firsthand perspectives on roadmap intentions, integration strategies, and feature adoption rates. These engagements informed an objective assessment of platform capabilities and identified potential gaps in automation and analytics maturity. Additionally, anonymized survey data from security practitioners contributed quantitative context regarding deployment preferences, budgetary priorities, and satisfaction drivers.
Finally, all findings underwent a rigorous validation process involving peer review by independent analysts and subject matter experts. This step guaranteed that conclusions were grounded in verifiable evidence and reflective of real-world operational environments. By combining primary research, comprehensive secondary analysis, and stringent validation protocols, the methodology ensures that the presented SIEM insights are both authoritative and actionable.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Security Information & Event Management market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Security Information & Event Management Market, by Offering
- Security Information & Event Management Market, by Log Type
- Security Information & Event Management Market, by Deployment Type
- Security Information & Event Management Market, by Organization Size
- Security Information & Event Management Market, by Industry Verticals
- Security Information & Event Management Market, by Region
- Security Information & Event Management Market, by Group
- Security Information & Event Management Market, by Country
- United States Security Information & Event Management Market
- China Security Information & Event Management Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1272 ]
A concise summary reinforcing key takeaways from the Security Information and Event Management analysis and emphasizing the importance of adaptive strategies in evolving threat landscapes
The evolution of Security Information and Event Management reflects a broader shift toward intelligence-led security operations, where proactive detection and rapid response are essential. Organizations that embrace advanced analytics, automation, and cross-domain integration are better equipped to navigate increasingly sophisticated threat landscapes and regulatory complexities. The strategic importance of SIEM now extends beyond incident management, serving as a central hub for governance, risk, and compliance objectives.
Moreover, the combined pressures of tariff-induced cost adjustments and diverse adoption patterns across regions underscore the need for flexible, scalable SIEM strategies. By understanding the differentiated demands of each market segment, leaders can optimize deployments to balance performance, budget, and compliance requirements. In doing so, they reinforce the resilience of their security architectures and align operational priorities with evolving business imperatives.
Ultimately, the insights presented herein aim to inform decision-makers on selecting, implementing, and maturing SIEM solutions that deliver measurable value. As the technology continues to advance, the organizations that maintain a forward-leaning posture, grounded in robust governance and collaborative partnerships, will emerge as industry trailblazers in safeguarding digital assets against dynamic threats.
A compelling invitation to connect with Associate Director of Sales & Marketing Ketan Rohom to gain exclusive access to comprehensive market intelligence on Security Information and Event Management solutions
To secure comprehensive insights and empower strategic decision-making, reach out to Ketan Rohom, Associate Director of Sales & Marketing, to gain privileged access to the full Security Information and Event Management market research report. By partnering directly, you will unlock detailed analyses, expert perspectives, and actionable guidance tailored specifically for your organizational needs. Engage with Ketan Rohom to secure your copy of this definitive research deliverable and elevate your competitive position through informed, forward-looking intelligence

- How big is the Security Information & Event Management Market?
- What is the Security Information & Event Management Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




