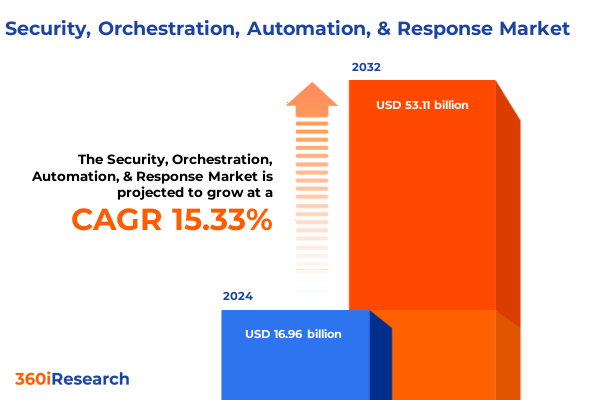
The Security, Orchestration, Automation, & Response Market size was estimated at USD 19.59 billion in 2025 and expected to reach USD 22.38 billion in 2026, at a CAGR of 15.30% to reach USD 53.11 billion by 2032.
Setting the Stage for the Next Generation of Automated Security Orchestration and Response in an Evolving Threat Landscape
The evolving threat environment has elevated the imperative for seamless integration of security operations and automation. As cyberattacks become more sophisticated and pervasive, organizations are compelled to adopt orchestration platforms that unify disparate tools, streamline workflows, and empower security teams to respond with speed and precision. Against this backdrop, this executive summary delves into the critical role of Security Orchestration, Automation, and Response (SOAR) solutions in reinforcing organizational resilience and driving measurable improvements in threat management.
Over the past several years, security leaders have grappled with siloed processes, overwhelming alert volumes, and talent shortages. By converging case management, collaboration, incident response, and threat intelligence under a unified framework, SOAR technologies address these challenges head-on. This introduction outlines the strategic context in which orchestration solutions are poised to redefine security operations, offering insights into the drivers behind accelerated adoption and the shifting expectations of cybersecurity stakeholders.
As organizations pivot toward digital transformation initiatives, the demand for robust automation has surged. This section sets the stage by highlighting the operational efficiencies, risk reduction benefits, and enhanced visibility that enterprise SOAR deployments deliver. By framing the core themes of vendor innovation, market dynamics, and organizational best practices, readers will gain a holistic understanding of why orchestration and automation are no longer optional but fundamental to modern security strategies.
Navigating Critical Technological Advances and Operational Paradigm Shifts Redefining Security Automation and Orchestration Practices
Technological advances such as artificial intelligence and machine learning are reshaping how security operations centers detect and remediate threats. AI-driven analytics now underpin threat triage and playbook recommendations, allowing teams to prioritize high-risk incidents with unprecedented accuracy. Concurrently, the maturation of cloud-native architectures has enabled orchestration platforms to scale dynamically, offering event-driven automation that adjusts resources in real time. These shifts mark a departure from traditional, on-premise workflows toward more agile, data-driven processes.
In parallel, regulatory landscapes across major markets have tightened, mandating faster breach disclosures and more rigorous evidence preservation. Compliance requirements are driving organizations to embed automated documentation and audit trails within their incident response workflows, ensuring consistency and defensibility. Moreover, the convergence of IT service management and security operations is fostering cross-functional collaboration, as incident response teams leverage shared ticketing systems and unified dashboards to streamline communication and accelerate resolution times.
Workforce dynamics are evolving alongside technology. Security teams are now expected to assume strategic roles, focusing on proactive threat hunting and continuous improvement of playbooks rather than manual ticket handling. To support this paradigm, orchestration platforms are incorporating low-code and no-code interfaces, democratizing automation so that non-developers can build and refine response workflows. Taken together, these transformational shifts are redefining the SOAR landscape, positioning automation and orchestration as catalysts for operational excellence.
Assessing the Far-reaching Consequences of 2025 United States Tariff Adjustments on Security Orchestration and Automation Solutions
In early 2025, a new wave of United States tariff adjustments targeted technology hardware and imported security appliances. These measures have created ripple effects across global supply chains, leading to increased costs for foundational components used in on-premise orchestration appliances. As vendors seek to mitigate margin erosion, many have passed incremental pricing onto end customers or restructured support contracts to offset tariff-driven expenses.
Beyond direct hardware pricing, tariffs have influenced vendor sourcing strategies. Some SOAR providers have diversified manufacturing footprints, expanding production to regions outside traditional hubs to bypass levies. Such strategic realignments have lengthened lead times for specialized network connectors and security modules, prompting organizations to reassess deployment timelines and consider temporary cloud-based alternatives. This recalibration has underscored the importance of hybrid architectures that can flex between on-premise and cloud consumption, insulating operations from supply chain volatility.
At the customer level, procurement teams are renegotiating service-level agreements and exploring managed orchestration services to alleviate capital expenditures tied to hardware refresh cycles. By shifting to consumption-based pricing models, organizations can maintain operational continuity without absorbing the full brunt of tariff-related cost spikes. These adaptive responses illustrate how 2025’s tariff landscape is a catalyst for architecture modernization, driving a reimagining of how security automation infrastructures are sourced, financed, and delivered.
Uncovering Strategic Insights across Diverse Solution Types Components Deployment Modes Organization Sizes and End User Verticals
Examining the market through the lens of solution types reveals that orchestration and automation have matured far beyond standalone incident response tools. Originally, case management systems dominated investments, but organizations now prioritize platforms that integrate collaboration channels, threat intelligence enrichment, and advanced playbook orchestration. This evolution underscores a shift from reactive ticketing to proactive, automated response across the entire threat lifecycle.
From a component perspective, platforms remain the strategic anchors of SOAR deployments, offering centralized control planes and data repositories. However, demand for services has surged as enterprises seek expert guidance. Professional services engagements deliver customized playbook development and process mapping, while managed services options appeal to organizations lacking in-house expertise. This trend highlights the growing importance of services-led delivery in achieving rapid time-to-value and sustaining continuous optimization.
Deployment mode segmentation further illustrates market diversification. Pure-cloud solutions continue to gain momentum for their rapid provision and elastic scalability, yet regulated industries often favor hybrid or on-premise configurations to maintain data sovereignty and compliance rigor. Large enterprises tend to adopt multi-modal strategies, leveraging cloud capabilities for emergent use cases and retaining on-premise deployments for mission-critical systems, whereas smaller organizations are gravitating toward cloud-native offerings to minimize operational overhead.
Organizational size also influences buying behavior. Large enterprises leverage internal security operations teams and invest in extensive customization, while small and medium enterprises prioritize out-of-the-box playbooks and simplified interfaces to maximize efficiency with limited resources. Finally, end-user verticals display distinct priorities: financial services emphasize fraud detection and compliance, energy and utilities focus on industrial control system security, government agencies require stringent audit trails, and healthcare entities seek data protection frameworks. Information technology and telecom providers integrate orchestration to handle large volumes of network alerts, while manufacturing firms utilize automated response for operational resilience.
This comprehensive research report categorizes the Security, Orchestration, Automation, & Response market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Solution Type
- Component
- End users
- Deployment Mode
- Organization Size
Illuminating Regional Dynamics Shaping Security Orchestration Adoption across the Americas Europe Middle East and Africa and Asia Pacific Markets
In the Americas, rapid cloud adoption and the presence of mature vendor ecosystems are accelerating SOAR integration. North American organizations are at the forefront of embedding automation into incident response processes, driven by high-profile breach events and stringent data protection regulations at the federal and state levels. Latin American markets, while at a nascent stage, are witnessing growing interest as regional consortiums emphasize cybersecurity modernization and cross-border information sharing.
Europe, the Middle East, and Africa present a tapestry of regulatory frameworks and adoption rates. The European Union’s comprehensive data privacy standards have propelled investments in orchestration solutions that deliver auditability and reporting capabilities. In the Middle East, sovereign wealth funds and national cyber strategies are underwriting ambitious digital transformation programs that include automated security operations. Across Africa, public-private partnerships are laying the groundwork for managed services models, enabling smaller enterprises and government entities to access advanced orchestration technologies without significant capital outlays.
The Asia-Pacific region embodies diverse maturity levels. Countries such as Japan and Australia demonstrate high penetration of cloud-based SOAR platforms, with leading industrial conglomerates seeking to fortify operational technology environments. Meanwhile, emerging markets in Southeast Asia and South Asia are beginning to experiment with hybrid models, often via managed services, to balance compliance requirements with cost efficiencies. Collectively, the regional mosaic highlights how geographic nuances shape deployment strategies and technology roadmaps.
This comprehensive research report examines key regions that drive the evolution of the Security, Orchestration, Automation, & Response market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Leading Organizations Driving Innovation and Competitive Strategies in Security Orchestration Automation and Response
Key market participants are differentiating through strategic partnerships and expanded platform ecosystems. Leading technology providers are embedding orchestration capabilities directly into broader security suites, enabling seamless integration with endpoint protection, network security, and identity management solutions. Vendors specializing in playbook automation are forging alliances with threat intelligence firms to enrich incident context and drive more effective response actions.
Innovation is also driven by organic investment and acquisitions. Market leaders have accelerated R&D cycles to incorporate low-code development environments and artificial intelligence-driven decision support, empowering security analysts to customize processes without extensive coding expertise. Some companies have pursued targeted acquisitions to bolster their service portfolios, particularly in areas such as managed detection and response, to offer end-to-end operational models.
Competitive dynamics are further defined by pricing flexibility. Vendors are increasingly offering consumption-based licensing alongside perpetual models, catering to organizations that require budgetary agility. In parallel, service providers have launched outcome-based engagements, where fees align with measurable improvements in mean time to detect and mean time to respond. These strategic maneuvers underscore how vendors are evolving business models to address customer demands for scalability, cost containment, and demonstrable ROI.
This comprehensive research report delivers an in-depth overview of the principal market players in the Security, Orchestration, Automation, & Response market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Cyware Labs, Inc.
- D3 Security, Inc.
- DFLabs S.p.A.
- Fortinet, Inc.
- Google LLC
- International Business Machines Corporation
- KnowBe4, Inc.
- LogRhythm, Inc.
- Microsoft Corporation
- Open Text Corporation
- Palo Alto Networks, Inc.
- Rapid7, Inc.
- ServiceNow, Inc.
- Splunk Inc.
- Sumo Logic, Inc.
- Swimlane, Inc.
- ThreatConnect, Inc.
- Tines Security Ltd.
- Torq Automation, Inc.
- Trellix Corporation
Empowering Industry Leaders with Actionable Recommendations to Elevate Security Orchestration Operational Efficiency and Resilience
Industry leaders should establish a unified automation roadmap that aligns security orchestration initiatives with broader digital transformation goals. By defining clear objectives-such as reducing manual ticket volume or improving playbook execution times-organizations can measure progress and prioritize investments in the highest-impact use cases. Aligning leadership expectations and security operations roadmaps fosters executive buy-in and secures the budget required for comprehensive deployments.
Robust partner ecosystems are critical to extend capabilities and accelerate value realization. Organizations are advised to engage managed service providers and technology integrators with deep domain expertise in orchestration. Collaborations that blend platform capabilities with threat intelligence feeds, compliance frameworks, and 24/7 support ensure that orchestration initiatives are resilient, adaptive, and continuously optimized.
To sustain momentum, security teams must invest in workforce enablement. Training programs that equip analysts with automation design skills and playbook development techniques will drive broader adoption and innovation. Additionally, integrating orchestration metrics-such as playbook success rates, automated response coverage, and analyst productivity gains-into executive dashboards ensures that performance improvements remain transparent and aligned with organizational risk management objectives.
Detailing Comprehensive Research Methodologies and Analytical Frameworks Underpinning the Security Orchestration Automation and Response Market Analysis
This analysis is grounded in a blend of primary and secondary research methodologies. Primary data was gathered through in-depth interviews with security operations center directors, chief information security officers, and technology decision-makers across multiple industries. These conversations provided nuanced insights into orchestration use cases, deployment challenges, and success metrics.
Secondary research encompassed a comprehensive review of industry publications, regulatory documents, vendor collateral, and financial reports. Publicly available case studies and thought leadership articles were analyzed to identify emerging trends and benchmark best practices. Additionally, vendor product roadmaps and partner program announcements were examined to map the competitive landscape and innovation trajectories.
Data triangulation techniques were applied to validate findings, ensuring consistency between qualitative feedback and quantitative evidence. Analytical frameworks such as technology adoption life cycle and vendor positioning matrices were leveraged to synthesize insights. Expert validation sessions with neutral cybersecurity consultants further refined conclusions and recommendations, guaranteeing that the research outcomes reflect real-world market dynamics and operational imperatives.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Security, Orchestration, Automation, & Response market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Security, Orchestration, Automation, & Response Market, by Solution Type
- Security, Orchestration, Automation, & Response Market, by Component
- Security, Orchestration, Automation, & Response Market, by End users
- Security, Orchestration, Automation, & Response Market, by Deployment Mode
- Security, Orchestration, Automation, & Response Market, by Organization Size
- Security, Orchestration, Automation, & Response Market, by Region
- Security, Orchestration, Automation, & Response Market, by Group
- Security, Orchestration, Automation, & Response Market, by Country
- United States Security, Orchestration, Automation, & Response Market
- China Security, Orchestration, Automation, & Response Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1113 ]
Synthesizing Key Insights and Strategic Imperatives to Strengthen Security Orchestration and Automation Initiatives Moving Forward
The convergence of advanced automation, integrated threat intelligence, and flexible deployment architectures underscores a pivotal moment in security operations. Organizations that harness orchestration platforms to automate repetitive tasks, enforce consistent playbooks, and enhance cross-team collaboration will achieve superior threat detection and response outcomes. The insights detailed throughout this executive summary point to a clear imperative: orchestration and automation are foundational elements of resilient security strategies.
As the market evolves, success will hinge on the ability to adapt architectures to changing regulatory requirements, incorporate emerging AI-driven capabilities, and cultivate a culture of continuous improvement. Leaders must remain vigilant to supply chain disruptions and cost pressures while maintaining agility through hybrid and cloud-native deployment models.
Looking ahead, the organizations that invest strategically-balancing innovative technology adoption with workforce enablement and partner ecosystem development-will secure a decisive advantage. By synthesizing the key trends, segmentation insights, regional dynamics, and competitive strategies presented in this summary, decision-makers can chart a course toward operational excellence and fortified cyber resilience.
Connect with Associate Director Ketan Rohom to Gain Exclusive Access and Purchase the Definitive Security Orchestration Market Research Report
To explore the full scope of insights, methodologies, and strategic recommendations outlined in this report, reach out directly to Associate Director Ketan Rohom to secure your copy today. By partnering with Ketan, you will gain tailored guidance to navigate complex procurement cycles, address stakeholder priorities, and accelerate decision-making processes. Whether you require deeper custom analysis, executive briefings, or volume licensing options, Ketan is prepared to align the report’s offerings with your organizational needs to maximize return on investment.

- How big is the Security, Orchestration, Automation, & Response Market?
- What is the Security, Orchestration, Automation, & Response Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




