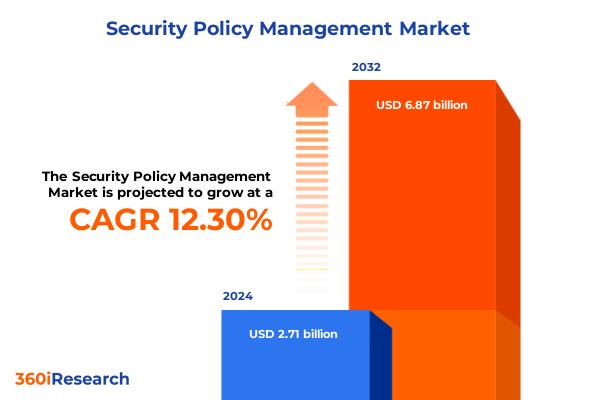
The Security Policy Management Market size was estimated at USD 3.04 billion in 2025 and expected to reach USD 3.40 billion in 2026, at a CAGR of 12.33% to reach USD 6.87 billion by 2032.
Understanding the Crucial Role of Security Policy Management in Safeguarding Digital Infrastructures Amid Evolving Threat Landscapes
Security policy management has emerged as a foundational element in today’s digital ecosystems as organizations contend with an ever-growing array of cyber threats and regulatory expectations. In response to accelerating transformation initiatives, enterprises are recognizing that well-defined, consistently enforced policies form the bedrock of reliable security postures. By bridging the gap between high-level governance and technical enforcement, policy management frameworks ensure that security controls are applied coherently across distributed networks, cloud environments, and hybrid infrastructures.
Moreover, the pervasive adoption of cloud services, remote work models, and Internet of Things (IoT) deployments has amplified the complexity of policy landscapes. In this context, organizations must navigate a labyrinth of vendor capabilities, integration challenges, and data sovereignty mandates. As a result, there is a growing imperative to adopt centralized policy management platforms that enable visibility, agility, and audit readiness. Transitioning away from siloed manual processes to integrated digital workflows not only streamlines policy authoring and enforcement but also accelerates incident response and continuous compliance.
Ultimately, this executive summary seeks to illuminate the critical drivers, market dynamics, and strategic imperatives shaping the security policy management domain, equipping decision-makers with the insights necessary to safeguard their infrastructures and maintain regulatory alignment.
Unveiling the Transformative Shifts Redefining Security Policy Management Through Technological Advancements and Regulatory Dynamics
The security policy management landscape is undergoing a profound transformation driven by rapid technological advancements, shifting regulatory frameworks, and evolving threat vectors. Cloud native architectures and microservices patterns have disrupted traditional perimeter-centric approaches, prompting organizations to adopt policy automation and dynamic enforcement techniques that align with elastic environments. Concurrently, artificial intelligence and machine learning capabilities are being integrated to accelerate policy audits and predictive compliance checks, fostering a proactive posture rather than reactive remediation.
In parallel, regulatory bodies are enhancing requirements to address data privacy, cross-border data flows, and supply chain risk. Legislations such as the updated NIS2 directive in Europe and the progressive tightening of cybersecurity criteria by U.S. federal agencies are compelling organizations to adopt rigorous policy governance mechanisms. These shifts necessitate the harmonization of global policy templates with localized controls to ensure consistency while honoring regional mandates.
Furthermore, the adoption of zero-trust principles has underscored the need for granular, context-aware policies that adapt to user behavior, device posture, and network conditions in real time. This paradigm shift is catalyzing the convergence of identity and access management, endpoint security, and policy orchestration platforms. As these transformative dynamics converge, enterprises that embrace integrated, intelligence-driven policy management will be better positioned to mitigate risks, streamline compliance, and derive strategic value from their security investments.
Assessing the Cumulative Impact of 2025 United States Tariffs on Security Policy Management Ecosystems and Supply Chain Resilience
U.S. tariff adjustments enacted in 2025 have injected new considerations into the security policy management ecosystem by influencing the cost structures and supply chain strategies of technology providers. With elevated duties on imported network appliances, semiconductor components, and certain cloud service offerings, vendors have recalibrated pricing models, leading to higher total cost of ownership for policy management solutions. These economic headwinds have prompted organizations to reassess long-term licensing commitments, prioritize modular deployment options, and evaluate the viability of on-premises versus cloud-based policy orchestration.
In addition, supply chain constraints arising from tariff-related procurement delays have affected hardware availability and implementation timelines. As a result, service integrators and managed security providers have adapted by shifting to more agile, software-centric delivery models. This shift enables faster policy roll-outs and reduces dependency on physical inventory, thereby mitigating the impact of cross-border duties and logistical bottlenecks. Simultaneously, there has been a notable uptick in domestic sourcing and the adoption of open standards to foster interoperability and vendor neutrality.
Ultimately, the cumulative impact of these tariffs has underscored the importance of flexible policy management architectures that decouple enforcement engines from specific hardware stacks. By embracing containerized policy modules, API-first integrations, and vendor-agnostic frameworks, organizations can navigate the complexities introduced by evolving trade policies while maintaining robust security postures and ensuring compliance across diverse operating environments.
Segmentation Insights into How Diverse Software Offerings Service Models Enterprise Scale Industry Verticals and Applications Influence Policy Management Dynamics
Market participants are focusing on differentiated software capabilities that span policy audit and compliance, policy authoring, and policy deployment and enforcement to address diverse governance requirements. The evolution of these modules reflects a broader industry trajectory toward holistic policy governance platforms, driven by the need for end-to-end automation and centralized visibility.
Service models are also adapting to deliver value across managed services engagements and professional services offerings. With an emphasis on outcome-driven partnerships, providers are blending advisory support, custom policy development, and fully outsourced policy management functions to align with client maturity and resource constraints.
Moreover, organizational scale plays a pivotal role in adoption patterns, with large enterprises investing in comprehensive, enterprise-grade platforms that integrate with existing security operations tools, while small and medium enterprises are gravitating toward streamlined solutions that emphasize ease of deployment and cost efficiency. This dichotomy has influenced product roadmaps, pricing tiers, and the emergence of modular consumption models.
Industry verticals such as banking, financial services, and insurance; energy and utilities; government and public sectors; healthcare; IT and telecommunications; manufacturing; and retail are each demanding tailored policy frameworks to address unique regulatory, operational, and threat-profile considerations. Application-level trends further underscore the importance of change management, compliance and auditing, network policy management, and vulnerability assessment as critical use cases that drive platform innovation and prioritize specialized tooling.
This comprehensive research report categorizes the Security Policy Management market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Software
- Services
- Organization size
- Vertical
- Application
Gaining Insight into Regional Evolution of Security Policy Management Trends and Opportunities Across the Americas Europe Middle East Africa and Asia-Pacific
Regional market dynamics reveal distinct trajectories across the Americas, Europe, Middle East and Africa, and Asia-Pacific regions, each influenced by varying levels of regulatory rigor, technological maturity, and threat landscapes. In the Americas, organizations are leveraging mature frameworks and extensive integrations with cloud service providers to advance policy automation, supported by a robust ecosystem of managed security service providers and regional centers of excellence.
Conversely, Europe, the Middle East and Africa are experiencing a surge in regulatory harmonization efforts, compelling organizations to align multi-jurisdictional policy controls with directives such as GDPR and NIS2. This convergence has accelerated demand for centralized policy management solutions that can dynamically adjust controls based on regional criteria while maintaining global consistency.
Meanwhile, Asia-Pacific is emerging as a high-growth market where digital transformation initiatives and rapid cloud adoption are driving investments in next-generation policy management platforms. Local data residency requirements and an increase in state sponsored cyber activities have heightened the focus on context-aware, scalable policy frameworks that can adapt to both legacy and modern network architectures. These regional insights underscore the need for adaptable strategies that accommodate regulatory diversity, market maturity, and shifting threat vectors.
This comprehensive research report examines key regions that drive the evolution of the Security Policy Management market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Examining Leading Companies Driving Innovation and Strategic Initiatives in Security Policy Management to Stay Ahead in an Evolving Cybersecurity Landscape
Leading technology vendors and service providers are strategically investing in product innovation, partnerships, and market expansion to capture emerging opportunities in the security policy management domain. Established network and cybersecurity firms are augmenting policy orchestration platforms with AI-driven analytics, threat intelligence integrations, and zero-trust enforcement modules to differentiate their offerings and accelerate time to value for customers.
At the same time, pure-play policy management specialists are pursuing strategic alliances with cloud hyperscalers and systems integrators to enhance deployment flexibility and broaden their market reach. This collaborative approach enables rapid integration with DevOps pipelines, container orchestration platforms, and micro-segmented network topologies, thus addressing the evolving needs of modern infrastructures.
Additionally, strategic mergers and acquisitions are shaping the competitive landscape, as vendors seek to consolidate capabilities across compliance, risk management, and policy automation. By bringing together complementary technology stacks, these consolidated entities can deliver unified governance and enforcement solutions, reducing operational complexity for enterprise customers.
These company-level initiatives are driving continuous enhancement of policy authoring interfaces, centralized dashboards, and automated remediation workflows, ensuring that organizations can maintain robust controls, streamline audit readiness, and proactively address emerging threats.
This comprehensive research report delivers an in-depth overview of the principal market players in the Security Policy Management market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- AlgoSec, Inc.
- Amazon Web Services, Inc.
- Archer Technologies, Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Diligent Corporation
- FireMon, LLC
- Fortinet, Inc.
- International Business Machines Corporation (IBM)
- Microsoft Corporation
- Mitratech Holdings, Inc.
- NAVEX Global, Inc.
- OneTrust, LLC
- Palo Alto Networks, Inc.
- ProcessUnity, Inc.
- RSA Security LLC
- Tenable, Inc.
- Trend Micro Incorporated
- Tufin Software Technologies Ltd.
- Zscaler, Inc.
Recommendations to Optimize Security Policy Management and Strengthen Organizational Resilience Against Emerging Cyber Threats for Industry Leaders
Industry leaders should embark on an integrated policy management strategy that unifies governance, automation, and analytics to streamline enforcement across hybrid infrastructures. By establishing cross-functional policy committees, organizations can ensure that security, operations, and compliance teams collaborate effectively in defining, reviewing, and updating policy rules. This structured approach promotes accountability and reduces the risk of configuration drift.
Furthermore, leveraging AI-enhanced policy audit capabilities can accelerate risk assessments and identify potential compliance gaps before they evolve into incidents. Organizations should prioritize platforms that embed machine learning models capable of contextualizing policy violations, mapping them to threat intelligence feeds, and recommending remediation steps.
In response to evolving trade policies and supply chain risks, enterprises should decouple policy enforcement modules from specific hardware dependencies. Embracing containerized deployments and API-centric integrations enhances resilience and provides the flexibility to shift workloads between on-premises and cloud-native environments seamlessly.
Finally, industry leaders must foster a culture of continuous improvement by investing in ongoing training, tabletop exercises, and simulated breach scenarios. By validating policy efficacy under realistic threat conditions, organizations can refine controls, optimize incident response, and build the organizational muscle memory required to withstand sophisticated cyber assaults.
Detailing the Rigorous Research Methodology Employed to Ensure Robust Insights Through Primary and Secondary Data Triangulation in Policy Management Analysis
The research methodology underpinning this analysis combined comprehensive secondary research with targeted primary engagements to ensure accuracy and depth. Initial secondary research involved the review of publicly available white papers, technical briefings, regulatory publications, and credible industry reports. This phase established the foundational understanding of market drivers, technology trends, and regulatory developments.
To validate these insights, structured interviews were conducted with senior security architects, compliance officers, and IT leaders across diverse industries and geographies. These primary discussions provided real-world perspectives on deployment challenges, tool preferences, and future roadmap priorities. Additionally, select workshops with system integrators and managed service providers offered granular visibility into delivery models and emerging service frameworks.
Quantitative data was triangulated with vendor-provided usage statistics, independent threat intelligence feeds, and regulatory compliance records to quantify adoption patterns and validate qualitative inputs. Throughout the research process, rigorous data hygiene procedures were applied, including cross-referencing multiple data sources and employing statistical analysis techniques to detect anomalies and ensure robustness.
This blended research approach enabled the development of nuanced segmentation, regional, and company-level insights, equipping decision-makers with a reliable and comprehensive view of the security policy management market.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Security Policy Management market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Security Policy Management Market, by Software
- Security Policy Management Market, by Services
- Security Policy Management Market, by Organization size
- Security Policy Management Market, by Vertical
- Security Policy Management Market, by Application
- Security Policy Management Market, by Region
- Security Policy Management Market, by Group
- Security Policy Management Market, by Country
- United States Security Policy Management Market
- China Security Policy Management Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 954 ]
Summarizing Strategic Conclusions on the Imperative of Security Policy Management for Navigating Emerging Challenges and Sustaining Organizational Resilience
This executive summary highlights the essential drivers shaping the security policy management landscape, including technological innovations, regulatory evolutions, and global trade considerations. By understanding these converging forces, organizations can design policy frameworks that align with hybrid architectures and dynamic threat profiles.
Furthermore, segmentation insights clarify how diverse software modules, service models, organization sizes, industry verticals, and application use cases influence adoption strategies. Regional perspectives underscore the need for adaptable platforms that honor local compliance requirements while providing centralized governance. Company-level analyses illustrate how strategic investments, partnerships, and M&A activities are redefining the competitive arena.
Actionable recommendations emphasize the importance of integrated governance structures, AI-enhanced audit capabilities, decoupled deployment architectures, and continuous validation exercises. These strategic imperatives will enable enterprises to mitigate risks, streamline operations, and sustain resilience in an increasingly complex security environment.
By synthesizing rigorous research and expert insights, this summary equips stakeholders with a clear roadmap to navigate the evolving policy management domain and to harness emerging opportunities effectively.
Unlock In-Depth Security Policy Management Insights by Connecting with Ketan Rohom Associate Director Sales and Marketing to Secure Your Market Research Report
Unlock a deeper understanding of the evolving security policy management landscape by engaging with Ketan Rohom, Associate Director of Sales and Marketing. Ketan brings a wealth of experience in translating complex research findings into actionable insights that directly inform strategic decision-making. By connecting with him, decision-makers and security leaders can access the comprehensive market research report that explores the latest technologies, regulatory shifts, and market dynamics shaping this critical domain.
This tailored market research report offers detailed analysis across software modules, service offerings, enterprise adoption patterns, industry verticals, and application use cases. It distills key trends, competitive strategies, and regional variations, providing organizations with the clarity needed to refine policy frameworks, optimize technology investments, and strengthen compliance postures. Whether you are focusing on advanced policy deployment automation or seeking to enhance audit and compliance processes, this report delivers the insights required to align initiatives with business imperatives.
Schedule a consultation today to explore how this research can support your security policy management objectives, mitigate emerging threats, and drive operational excellence. Ketan welcomes the opportunity to discuss your organization’s specific challenges and objectives and to demonstrate how the report’s findings can catalyze growth. Reach out to secure your copy and position your organization at the forefront of policy management innovation.

- How big is the Security Policy Management Market?
- What is the Security Policy Management Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




