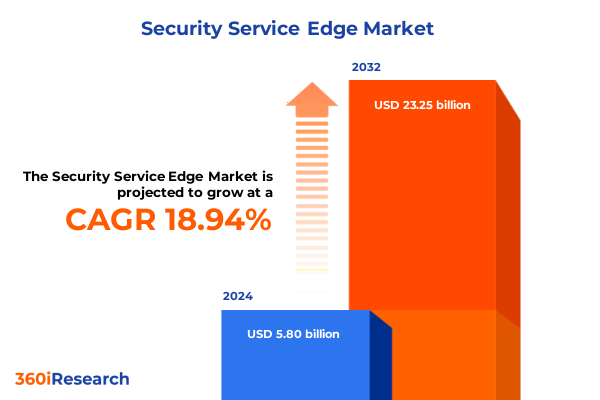
The Security Service Edge Market size was estimated at USD 6.85 billion in 2025 and expected to reach USD 8.09 billion in 2026, at a CAGR of 19.06% to reach USD 23.25 billion by 2032.
Pioneering Security Service Edge Strategies to Bolster Digital Defenses and Enable Resilient, Compliant Networks in an Era of Accelerating Cyber Challenges
The convergence of networking and security has catalyzed a paradigm shift in how enterprises protect, monitor, and optimize access to applications across hybrid and multi-cloud environments. As digital transformation initiatives accelerate, organizations face unprecedented complexity driven by the proliferation of remote workforces, containerized applications, and SaaS adoption. In response, the emergence of Security Service Edge has become a strategic imperative to replace fragmented security stacks with an integrated, cloud-native framework that seamlessly enforces policy at the edge.
Amid an escalating threat landscape, Security Service Edge delivers unified capabilities-ranging from secure web gateway to zero trust network access-through a globally distributed fabric. This approach not only mitigates risks associated with lateral movement and data exfiltration but also enhances user experience by routing traffic along optimized paths. Coupled with managed and professional services offerings, enterprises can accelerate deployment and ensure operational maturity.
Drawing on extensive field research, stakeholder interviews, and real-time threat intelligence, this executive summary offers a concise yet comprehensive overview of the forces shaping the Security Service Edge domain. It establishes the context for understanding transformative trends, tariff headwinds in the United States, segmentation nuances, regional dynamics, and strategic imperatives for technology leaders ready to modernize cybersecurity operations.
Embracing Zero Trust and Cloud Native Convergence to Redesign Perimeter Security for the Modern Hybrid Enterprise
The landscape of network security has undergone transformative shifts as organizations migrate workloads to cloud platforms and adopt remote-first operating models. Traditional perimeter-centric defenses are giving way to zero trust principles, whereby continuous verification and least-privilege access are non-negotiable. This shift is driven by the realization that threats can originate from within trusted networks, necessitating an identity-centric approach that validates every session, device, and application request before granting access.
Simultaneously, the rapid ascent of SASE architectures reflects a convergence of point solutions into a unified service delivery model. Enterprises are decommissioning legacy VPNs and disparate web gateways in favor of cloud-native security stacks that scale elastically. This evolution is underpinned by a broad ecosystem of partners and acquisitions, fostering deeper integration between network optimization services and advanced threat protection.
Furthermore, regulatory pressures around data sovereignty and compliance have prompted security professionals to demand granular policy controls and audit capabilities. As data protection regulations proliferate across jurisdictions, service providers are embedding built-in compliance frameworks into their offerings. Together, these shifts signal a new era in which security is decentralized, automated, and intrinsically aligned with the dynamic demands of digital business.
Navigating Elevated Tariff Pressures on Security Hardware Procurement to Accelerate Cloud-Native Adoption and OPEX-Centric Strategies
In 2025, reinforced tariff measures in the United States have exerted cumulative impacts on the procurement of network security appliances and cloud gateway hardware. Increased duties on imported routers, switches, and specialized edge appliances have elevated capital expenditure for technology teams, prompting many to reassess procurement cycles and total cost of ownership. As a direct consequence, organizations are accelerating transitions to virtualized security functions delivered from the cloud, reducing dependency on on-premises hardware and mitigating exposure to import levies.
Moreover, service providers have absorbed portions of these increased costs through subscription models and managed services to preserve client retention and maintain pricing competitiveness. This dynamic has shifted the balance in favor of software-as-a-service and platform-as-a-service offerings, enabling faster time to value and predictable operating expenditure. Customers benefiting from consolidated managed services are achieving greater cost visibility, even as tariff headwinds linger.
At the intersection of geopolitical tensions and supply chain volatility, security teams are prioritizing diversification of hardware partners and exploring onshore manufacturing options. These strategic adjustments not only hedge against future tariff escalations but also align with broader corporate imperatives around supply chain resilience and sustainable procurement.
Unpacking Multi-Dimensional Security Service Edge Market Segments to Align Technology and Support Models with Organizational Priorities
An in-depth analysis reveals that security service edge offerings bifurcate into platform and service categories, each addressing distinct operational imperatives. Platform solutions encompass cloud access security broker, firewall as a service, secure web gateway, and zero trust network access, delivering granular policy controls and threat inspection across user traffic. Conversely, the service dimension includes managed services for ongoing operation, threat monitoring, and incident response, alongside professional services for architecture design, customization, and integration. This dual lens underscores the importance of selecting vendors that offer both a robust technology stack and expert support.
Deployment mode further differentiates the market into cloud-based and on-premises delivery models. While cloud-based implementations dominate due to scalability and reduced infrastructure overhead, certain regulated industries continue to favor on-premises deployments for sensitive workloads or specific compliance requirements. Consequently, vendors that facilitate hybrid deployments with consistent policy orchestration across both environments are witnessing heightened demand.
Organizational size also influences decision criteria. Large enterprises, with complex global footprints and mature security operations centers, often require integrated analytics, automation, and threat intelligence feeds. In contrast, small and medium enterprises prioritize ease of deployment, cost efficiency, and turnkey management. This dichotomy drives solution providers to offer tiered feature sets and consumption-based pricing.
Finally, end-use applications span vertical markets such as banking, financial services and insurance, energy and utilities, government, healthcare, information technology and telecommunications, manufacturing, and retail and e-commerce. Each vertical exhibits unique risk profiles and regulatory obligations, necessitating tailored policy libraries, industry-specific threat intelligence, and compliance reporting capabilities.
This comprehensive research report categorizes the Security Service Edge market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Type
- Deployment Mode
- Organization Size
- End Use Applications
Analyzing Regional Dynamics to Illuminate the Diverse Drivers of Security Service Edge Adoption Across Americas, EMEA, and Asia-Pacific
Regionally, the Americas lead adoption of security service edge solutions, propelled by advanced cloud adoption, stringent data privacy regulations, and an expansive network of managed service providers. North American enterprises, in particular, are driving demand for advanced analytics and AI-powered threat detection, while Latin American organizations prioritize rapid deployment and cost-effective managed services to bridge resource gaps.
In the Europe, Middle East & Africa corridor, regulatory frameworks such as the GDPR and emerging data sovereignty mandates have elevated the importance of localized policy controls and sovereign cloud options. Enterprises in this region often engage security partners capable of delivering on-premises hardware alongside cloud-based services to satisfy cross-border data transfer requirements and stringent audit trails.
The Asia-Pacific landscape exhibits rapid growth fueled by digital infrastructure investments and widespread enthusiasm for cloud transformation. Governments and large enterprises in China, Japan, Australia, and Southeast Asian markets are integrating secure web gateways and zero trust architectures to support expanding mobile and IoT ecosystems. Local vendors and global hyperscalers alike are tailoring offerings to meet diverse language, compliance, and performance needs across this heterogeneous market.
This comprehensive research report examines key regions that drive the evolution of the Security Service Edge market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Assessing Competitive Forces Shaping Security Service Edge Innovation and Partner-Powered Ecosystems to Sustain Market Leadership
Leading technology vendors and emerging disruptors are vigorously competing to establish dominance in the security service edge arena. Incumbent network equipment manufacturers are expanding software portfolios and forging strategic alliances with cloud hyperscalers. Meanwhile, cloud-native startups are differentiating through micro-services architectures, API-first integration, and AI-driven threat analytics.
A surge of mergers and acquisitions has reshaped the competitive landscape, enabling established security vendors to integrate zero trust capabilities and expand managed services footprints. Simultaneously, specialized professional services firms are carving out niche positions by offering deep vertical expertise and bespoke integration services for complex hybrid environments. These diverse go-to-market strategies underscore the critical balance between innovation velocity and customer trust.
In addition, partnerships between service providers and technology alliances are accelerating ecosystem interoperability. Cross-vendor integrations for single-pane-of-glass management and unified policy orchestration are rapidly becoming standard expectations. Providers that deliver both comprehensive platform capabilities and a robust network of managed services partners are emerging as preferred suppliers for enterprise security teams seeking end-to-end simplicity and operational resiliency.
This comprehensive research report delivers an in-depth overview of the principal market players in the Security Service Edge market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Akamai Technologies, Inc.
- Barracuda Networks, Inc.
- Broadcom Inc.
- Cato Networks Ltd.
- Check Point Software Technologies Ltd.
- Cloudflare, Inc.
- ExtraHop Networks, Inc.
- F5 Networks, Inc.
- Forcepoint, LLC
- Fortinet, Inc.
- Imperva, Inc.
- Juniper Networks, Inc.
- McAfee Corp.
- Microsoft Corporation
- Netskope, Inc.
- Palo Alto Networks, Inc.
- Proofpoint, Inc.
- Radware Ltd.
- SonicWall Inc.
- Sophos Group plc
- Tata Communications Limited
- Trend Micro Incorporated
- WatchGuard Technologies, Inc.
- Zscaler, Inc.
Driving Resilient Security Posture Through Zero Trust Adoption, Supply Chain Diversification, and Data-Driven Governance Practices
Industry leaders should prioritize a holistic, cloud-native security strategy that unifies policy enforcement across distributed environments. By adopting zero trust network access as the foundation, organizations can systematically eliminate implicit trust and reduce attack surfaces. Concurrently, integrating advanced threat analytics and automation into security service edge platforms will accelerate detection and response times while alleviating operational burdens on security operations centers.
Leaders are also advised to engage in proactive supply chain diversification to buffer against tariff volatility and hardware shortages. Embracing a balanced mix of cloud-based and on-premises architectures ensures flexibility, compliance alignment, and cost predictability. Furthermore, investing in workforce upskilling and aligning with managed service partners will empower security teams to focus on strategic initiatives rather than routine maintenance.
Finally, establishing a governance framework that incorporates continuous feedback loops, performance metrics, and compliance monitoring will drive sustained optimization. By leveraging data insights from policy usage, threat intelligence feeds, and user behavior analytics, executives can refine security posture iteratively, ensuring alignment with evolving business objectives and regulatory mandates.
Detailing a Robust Multi-Phased Methodology Combining Executive Interviews, Market Intelligence, and Validation Workshops to Ensure Analytical Integrity
The research approach entailed a rigorous blend of primary and secondary investigations. Primary insights were harvested from in-depth interviews with C-level executives, security architects, and managed service operators, delivering firsthand perspectives on deployment challenges, procurement drivers, and success metrics. Concurrently, expert roundtables and workshops provided qualitative validation of key use cases and technology adoption roadmap scenarios.
Secondary research encompassed a comprehensive review of industry white papers, regulatory filings, vendor press releases, and publicly available threat intelligence feeds. This multi-source dataset was triangulated to ensure consistency, relevance, and timeliness of findings. Additionally, vendor solution demonstrations and proof-of-concept evaluations were conducted to assess functional capabilities and integration maturity across leading platforms.
To uphold analytical rigor, quantitative data points-such as adoption rates, deployment timelines, and incident response benchmarks-were cross-referenced with third-party surveys and anonymized telemetry provided by security operations centers. The combined methodology ensures that the insights presented herein rest on a robust evidentiary foundation, offering executives a reliable framework for strategic decision-making.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Security Service Edge market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Security Service Edge Market, by Type
- Security Service Edge Market, by Deployment Mode
- Security Service Edge Market, by Organization Size
- Security Service Edge Market, by End Use Applications
- Security Service Edge Market, by Region
- Security Service Edge Market, by Group
- Security Service Edge Market, by Country
- United States Security Service Edge Market
- China Security Service Edge Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1113 ]
Consolidating Strategic Imperatives Around Zero Trust, Cloud Native Scalability, and Service-Oriented Partnerships to Secure Tomorrow’s Networks
In an era where cyber threats evolve at the speed of cloud, the imperative for unified, adaptive security architectures has never been clearer. Security Service Edge stands at the forefront of this evolution, offering a consolidated framework that addresses performance, compliance, and resilience across distributed networks. Leaders who harness zero trust principles, cloud-native scalability, and data-driven governance are poised to outmaneuver adversaries and secure digital transformations.
As enterprises grapple with geopolitical headwinds, tariff uncertainties, and shifting regulatory landscapes, the integration of managed and professional services emerges as a critical lever for operational success. By aligning vendor partnerships to organizational priorities-whether around agility, cost efficiency, or compliance-end users can realize sustained value from their security investments.
Ultimately, the journey toward a mature Security Service Edge posture is iterative, requiring continuous feedback, threat intelligence integration, and capability refinement. The insights presented in this summary equip decision makers with the strategic context and actionable direction needed to navigate this complex terrain and achieve robust, future-proof security outcomes.
Unlock Exclusive Security Service Edge Intelligence with a Personalized Consultation to Acquire the Definitive Market Research Report
To explore comprehensive insights, in-depth analysis, and strategic implications tailored for decision makers, please reach out to Ketan Rohom (Associate Director, Sales & Marketing at 360iResearch). Securing this authoritative security service edge market research report will empower your organization with the clarity and foresight needed to navigate the evolving cybersecurity terrain. Connect directly with Ketan to arrange a personalized briefing and gain immediate access to the latest findings, critical case studies, and actionable data that will inform your next strategic initiative.

- How big is the Security Service Edge Market?
- What is the Security Service Edge Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




