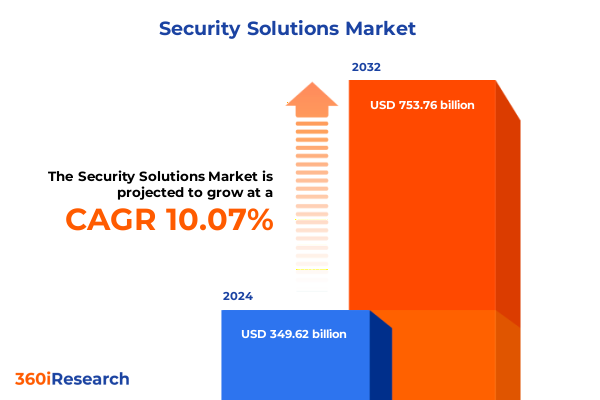
The Security Solutions Market size was estimated at USD 384.60 billion in 2025 and expected to reach USD 423.09 billion in 2026, at a CAGR of 10.08% to reach USD 753.76 billion by 2032.
A Comprehensive Overview of Modern Security Dynamics Providing Context for Holistic Risk Mitigation and Strategic Investment Decisions
In today’s interconnected digital and physical environment, organizations face an unprecedented convergence of risks that challenge traditional security paradigms. Rapid advances in digital transformation have extended enterprise perimeters well beyond corporate firewalls into cloud architectures, mobile devices, and smart infrastructure. Concurrently, physical security frameworks have become increasingly integrated with cybersecurity controls, creating a single threat surface that spans application vulnerabilities, network intrusions, and physical breaches. As a result, decision-makers must adopt a holistic understanding of evolving threat vectors and risk mitigation approaches to safeguard assets, data, and reputations in this complex ecosystem.
This report opens by contextualizing the modern security landscape against a backdrop of accelerating regulatory pressures, sophisticated adversaries, and shifting technology investments. It examines how the industry’s evolution has driven a strategic shift from reactive defense mechanisms toward proactive risk management and resilience planning. By establishing a common baseline of the prevailing security environment, this introduction sets the stage for deeper analysis of transformative trends, tariff implications, segmentation drivers, regional dynamics, and actionable strategies that will equip leaders to navigate uncertainty and capitalize on emerging opportunities.
Identification of Key Transformative Shifts Reshaping the Security Solutions Ecosystem Amidst Rapid Technological Convergence and Regulatory Evolution
The security solutions ecosystem has undergone profound transformations driven by rapid technological convergence and escalating threat sophistication. Artificial intelligence and machine learning have transitioned from experimental tools into core components of threat detection, enabling behavioral analytics that can identify anomalous activity across cloud workloads and on-premises infrastructure. Edge computing and 5G networks have introduced low-latency connectivity for smart sensors and IoT devices, blending physical and digital security to facilitate predictive maintenance, crowd analytics, and real-time access control. These developments have reshaped vendor portfolios and accelerated the adoption of unified platforms that span application security, network defense, and physical monitoring.
Regulatory frameworks and compliance mandates have evolved in parallel, influencing both technology adoption and investment priorities. Data privacy regulations such as the California Privacy Rights Act and evolving federal cybersecurity standards have compelled organizations to adopt granular data governance and encryption strategies across cloud and on-premises deployments. Similarly, critical infrastructure operators in energy, utilities, and transportation have faced stringent requirements under emerging directives, driving investments in security analytics, intrusion detection, and perimeter controls. Together, technological advances and regulatory imperatives have catalyzed a strategic pivot toward zero trust architectures and integrated risk management solutions.
Comprehensive Analysis of the Cumulative Impact of 2025 United States Tariff Measures on Security Supply Chains Component Costs and Solution Accessibility
In 2025, the United States government implemented targeted tariff measures designed to protect domestic industries and address trade imbalances with major manufacturing partners. These tariffs have notably impacted the security hardware sector, increasing the cost of imported components such as camera modules, biometric sensors, and network switches. Providers of physical security solutions have encountered higher input costs, prompting supply chain realignment efforts including diversification to alternative sourcing regions and accelerated nearshoring initiatives. At the same time, cybersecurity vendors reliant on imported specialized hardware for secure boot processes and hardware-based encryption modules have felt the downstream effects of component price inflation.
Meanwhile, end users and integrators have adapted by renegotiating long-term agreements, exploring modular procurement options, and prioritizing software-centric solutions to mitigate capital expenditure spikes. As price pressures mount, competitive differentiation has shifted toward value-added services such as managed security offerings, performance-based contracts, and hybrid deployment models that reduce reliance on high-cost proprietary hardware. The cumulative effect of these tariffs underscores the importance of supply chain agility and vendor transparency in maintaining cost-effective security architectures and ensuring business continuity.
In-Depth Insights into Critical Security Market Segmentation Highlighting Security Type Component Deployment Model End User Industry and Organizational Scale Drivers
A nuanced understanding of security market segmentation underpins strategic decision-making across industries. Security type segmentation differentiates between the cybersecurity domain-encompassing application security, cloud security, endpoint protection, identity and access management, network security, and security analytics and SIEM-and the physical security domain, which includes access control, fire safety and protection, intrusion detection, perimeter security, and video surveillance technologies. Within physical access control, choices span biometric, card-based, and mobile credential systems, while fire safety breaks down into detection systems and suppression mechanisms. Perimeter protection further bifurcates into barriers, bollards, and fences, and video surveillance ranges from analog to IP-based solutions. This layered approach allows stakeholders to fine-tune investments based on distinct threat profiles and operational priorities.
Component segmentation divides the market into services-covering managed services and professional services with subcategories of consulting, integration, support, and maintenance-and solutions, which split into hardware and software offerings. Deployment mode segmentation highlights the growing importance of cloud-native architectures, hybrid environments that balance centralized and distributed workloads, and traditional on-premises installations for sensitive operations. End user segmentation reveals diverse requirements across banking, financial services, and insurance; energy and utilities; government and defense; healthcare; information technology and telecommunications; manufacturing; retail; and transportation and logistics. Finally, organization size segmentation distinguishes between large enterprises with complex, multi-site deployments and small to medium enterprises that often favor turnkey, cost-effective solutions. Together, these segmentation insights illuminate buyer behaviors, purchasing cycles, and integration challenges that shape vendor strategies.
This comprehensive research report categorizes the Security Solutions market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Security Type
- Component
- Deployment Mode
- End User Industry
Strategic Regional Perspectives Examining Distinct Security Market Dynamics and Growth Enablers across Americas Europe Middle East Africa and Asia Pacific
Regional dynamics exert a profound influence on security solution demand and adoption patterns. In the Americas, mature markets such as the United States and Canada demonstrate robust demand for advanced cybersecurity capabilities, particularly in cloud security and identity management, driven by evolving federal regulations and high-profile breach disclosure requirements. Latin American markets are gradually scaling investments in perimeter security and video surveillance to address urban crime rates and bolster public safety infrastructure, though budget constraints often lead to a focus on hybrid deployments that optimize capital and operational expenditures.
The Europe, Middle East, and Africa region presents a complex tapestry of security priorities and regulatory environments. Western European nations emphasize data privacy compliance alongside network security, motivated by evolving GDPR interpretations and sector-specific guidelines for critical infrastructure. In the Middle East, sovereign wealth fund–backed projects in smart cities, oil and gas, and transportation have accelerated demand for integrated cybersecurity and physical security frameworks. African markets, while nascent, show potential for leapfrogging traditional architectures by leveraging cloud-based access control and managed services to circumvent legacy infrastructure limitations.
Asia-Pacific remains the fastest-growing security market worldwide, fueled by digital transformation initiatives in China, Japan, South Korea, and emerging Southeast Asian economies. Governments across the region invest heavily in public safety systems, including facial recognition and IP surveillance, integrated with cybersecurity platforms to protect sensitive data flows. Hybrid cloud deployments dominate in APAC, as organizations balance rapid scalability with data sovereignty concerns, creating opportunities for vendors to offer tailored managed solutions that address local compliance requirements and language preferences.
This comprehensive research report examines key regions that drive the evolution of the Security Solutions market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Detailed Examination of Leading Security Solutions Providers Their Strategic Differentiators and Competitive Positioning in a Rapidly Evolving Market
Leading security solution providers are differentiating through strategic acquisitions, ecosystem partnerships, and continuous innovation in both hardware and software. Global networking giants have expanded their security portfolios by integrating next-generation firewalls, secure access service edge capabilities, and zero trust frameworks into broad enterprise offerings. Pure-play cybersecurity vendors focus on deep specialization, advancing machine learning–driven threat intelligence and user behavior analytics. Concurrently, established physical security firms are forging alliances with cloud providers to deliver converged platforms that unify video surveillance, access management, and analytics under a single pane of glass.
Emerging challengers leverage open architectures and developer-friendly APIs to create modular solutions that address specific industry pain points, such as medical device security in healthcare or SCADA protection in utilities. In parallel, managed security service providers have gained traction by offering flexible consumption models, 24/7 monitoring, and rapid incident response, appealing to both large enterprises seeking to offload operational complexity and small to medium enterprises lacking in-house expertise. This competitive landscape underscores the need for collaboration across technology stacks and supply chains to deliver differentiated value while maintaining scalability and interoperability.
This comprehensive research report delivers an in-depth overview of the principal market players in the Security Solutions market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- ADT Inc.
- Airbus SE
- Assa Abloy AB
- Axis Communications AB
- BAE Systems plc
- Bosch Sicherheitssysteme GmbH
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Holdings, Inc.
- Fortinet, Inc.
- Hangzhou Hikvision Digital Technology Co., Ltd.
- Hanwha Vision Co., Ltd.
- Honeywell International Inc.
- International Business Machines Corporation
- Johnson Controls International plc
- Microsoft Corporation
- NEC Corporation
- Palo Alto Networks, Inc.
- Raytheon Company
- Secom Co., Ltd.
- Teledyne FLIR LLC
- Thales S.A.
- Trend Micro Incorporated
- VMware, Inc.
- Zhejiang Dahua Technology Co., Ltd.
Strategic Actionable Recommendations Guiding Industry Leaders to Leverage Innovation Strengthen Partnerships and Optimize Security Investment Portfolios
Industry leaders should prioritize the consolidation of security operations across physical and cyber domains to reduce blind spots and streamline incident response. By adopting integrated risk management platforms that encompass cloud security posture management, network threat detection, and video analytics, organizations can achieve a unified security stance and improve operational efficiency. Executives are encouraged to develop strategic partnerships with managed service providers to augment internal capabilities and ensure 24/7 monitoring, leveraging these alliances to fast-track deployment and reduce total cost of ownership.
Organizations must also realign supply chain strategies in light of evolving tariff landscapes, diversifying supplier portfolios and exploring local assembly options to mitigate cost fluctuations. Investing in scalable, cloud-native solutions with modular architectures can further insulate operations from hardware price volatility. Leadership teams should accelerate workforce upskilling in emerging technologies such as AI-driven analytics and zero trust frameworks, fostering a security-first culture that empowers employees to act as frontline defenders. Finally, aligning security investments with business outcomes and regulatory mandates will enable decision-makers to quantify risk reduction, demonstrate compliance, and secure sustained executive sponsorship.
Rigorous Research Methodology Outlining Comprehensive Primary Secondary Data Collection and Analytical Frameworks to Ensure Robust Market Insights
This analysis employs a multi-stage research methodology combining comprehensive secondary research with in-depth primary engagements. Secondary research involved systematic review of publicly available data sources, industry publications, trade association reports, and regulatory filings to establish baseline market trends and technology trajectories. To validate findings, primary research was conducted through structured interviews with security technology executives, channel partners, system integrators, and end user decision-makers across multiple regions and industry verticals.
Data triangulation techniques ensured consistency across qualitative insights and quantitative indicators, while expert panels provided validation of evolving use cases and maturity models. The research framework incorporated a robust segmentation approach, delineating security types, components, deployment modes, end user industries, and organization sizes. Regional analyses were reinforced by localized data collection efforts to capture regulatory nuances and investment drivers. Throughout the process, key metrics and thematic drivers were continuously cross-referenced to industry benchmarks, ensuring the report’s conclusions reflect both current realities and emerging trends.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Security Solutions market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Security Solutions Market, by Security Type
- Security Solutions Market, by Component
- Security Solutions Market, by Deployment Mode
- Security Solutions Market, by End User Industry
- Security Solutions Market, by Region
- Security Solutions Market, by Group
- Security Solutions Market, by Country
- United States Security Solutions Market
- China Security Solutions Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 2226 ]
Conclusive Synthesis of Security Market Findings Emphasizing Strategic Imperatives and Opportunities for Enhanced Risk Management and Operational Resilience
The convergence of cybersecurity and physical security continues to redefine enterprise risk management, driven by converging technology stacks, heightened regulatory demands, and evolving threat landscapes. Organizations that embrace integrated security frameworks, underpinned by zero trust principles and AI-driven analytics, will be positioned to detect, respond to, and remediate incidents more effectively. The interplay of tariff-induced cost pressures and regional market dynamics underscores the necessity for agile supply chain strategies and flexible deployment models that align with both business objectives and compliance requirements.
As the security landscape evolves, collaboration across technology vendors, service providers, and end users becomes paramount. Firms that invest in talent development, robust governance structures, and ecosystem partnerships will drive sustained resilience and competitive advantage. In sum, the strategic imperatives outlined throughout this report offer a roadmap for decision-makers seeking to navigate complexity, optimize resource allocation, and fortify organizational defenses against the full spectrum of emerging risks.
Engaging Call To Action Encouraging Collaboration with Associate Director of Sales and Marketing for Access to the Comprehensive Security Solutions Market Research Report
Ready to gain unparalleled insights into the evolving security solutions market and transform your organization’s risk management strategies? Engage directly with Ketan Rohom, Associate Director, Sales & Marketing, to access the full depth and breadth of our comprehensive report. Discover how tailored data, actionable analysis, and expert guidance can empower your decision-making and drive growth in a complex security landscape. Take the next step toward informed investments and strategic advantage by securing your copy of the definitive security solutions market research report today

- How big is the Security Solutions Market?
- What is the Security Solutions Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




