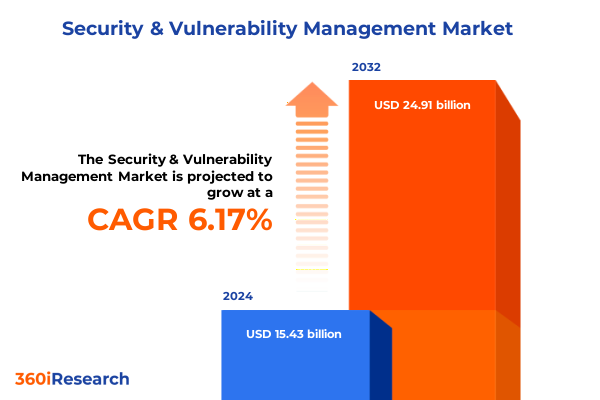
The Security & Vulnerability Management Market size was estimated at USD 16.36 billion in 2025 and expected to reach USD 17.36 billion in 2026, at a CAGR of 6.18% to reach USD 24.91 billion by 2032.
Understanding the Evolving Security and Vulnerability Management Ecosystem That Empowers Resilience and Drives Growth Amid Heightened Threats and Digital Transformation
Understanding the Evolving Security and Vulnerability Management Ecosystem That Empowers Resilience and Drives Growth Amid Heightened Threats and Digital Transformation
The landscape of security and vulnerability management has undergone profound evolution as organizations grapple with increasingly sophisticated cyber threats. Modern enterprises face an expanded scope of vulnerabilities, encompassing not only traditional software flaws but also misconfigurations, behavioral anomalies, and inadvertent exposures, necessitating a holistic and integrated approach to risk reduction and threat mitigation. Studies project that this broadened definition will compel IT and security leaders to incorporate advanced scanning, predictive analytics, and continuous monitoring into their core strategies to maintain visibility and control over sprawling digital environments.
Moreover, systemic pressures such as rapid cloud migration, remote workforce proliferation, and heightened regulatory scrutiny have intensified the demand for unified vulnerability management programs. Industry research underscores the imperative of transitioning from reactive patching to strategic, threat-driven prioritization frameworks, leveraging historical exploitation evidence and predictive modeling to focus remediation efforts where they matter most. This shift is catalyzed by innovations in AI-driven decision trees, which have demonstrated up to eighteen-fold efficiency improvements in remediation workflows, reducing critical workloads by over 95% while maintaining robust risk coverage.
Navigating the Next Wave of Security Innovations as AI-Driven Automation, Zero Trust Architectures, and Hybrid Cloud Models Redefine Vulnerability Management Strategies
Navigating the Next Wave of Security Innovations as AI-Driven Automation, Zero Trust Architectures, and Hybrid Cloud Models Redefine Vulnerability Management Strategies
Artificial intelligence and machine learning have emerged as core enablers of next-generation vulnerability management, enhancing the speed and accuracy of risk detection, predictive prioritization, and automated remediation. Machine learning algorithms now sift through millions of telemetry data points to identify high-probability exploits, while AI-powered orchestration platforms streamline patch deployment and configuration fixes with minimal human intervention. Organizations embedding these capabilities report measurable gains in operational efficiency and significant reductions in breach-window exposure.
Simultaneously, the proliferation of Zero Trust security models has redefined perimeter assumptions, compelling enterprises to adopt a “never trust, always verify” stance across users, devices, and workloads. Regulatory initiatives such as CISA’s Secure by Design program further reinforce this mandate, urging software vendors and end-users alike to integrate security into the product development lifecycle and to stamp out longstanding vulnerabilities such as cross-site scripting and OS command injection.
Hybrid cloud deployments and Secure Access Service Edge (SASE) frameworks are converging to bridge network and security functions, delivering consistent policy enforcement and real-time threat protection irrespective of location. This confluence accelerates cloud workload migrations and fosters tariff-immune operational models, enabling organizations to circumvent import-driven hardware cost pressures while fortifying perimeter defenses through SaaS-native architectures.
As threat actors leverage decentralized disclosure techniques and permissioned blockchain for transparency evasion, security teams must evolve toward integrated, real-time monitoring and decentralized accountability, ensuring robust governance over vulnerability publication and patch management cycles.
Assessing the Broader Implications of United States Tariff Policies on the Security and Vulnerability Management Industry During 2025 Trade Conflicts and Supply Chain Shifts
Assessing the Broader Implications of United States Tariff Policies on the Security and Vulnerability Management Industry During 2025 Trade Conflicts and Supply Chain Shifts
The imposition of reciprocal tariffs on technology components has directly impacted hardware-focused security solutions, forcing manufacturers and service providers to contend with cost increases of up to 18% on network appliances, firewalls, and unified threat management systems. Many enterprises have responded by extending hardware refresh cycles and investing in lifecycle extension services to maximize existing investments, signaling a strategic pivot toward optimizing asset utilization under fiscal constraints.
SOC as a Service providers have similarly felt the strain of up-front capital expenditures as tariffs inflate the price of imported detection and response appliances. To preserve margins, some MSSPs have delayed infrastructure upgrades or shifted customers to cloud-native alternatives, though this transition carries potential performance risks when on-premise hardware is deferred beyond optimal service cycles.
Penetration testing consultancies face hidden cost surges as tariffs on servers, routers, and specialized testing appliances raise the overhead of replicating production environments for ethical hacking engagements. Smaller firms are particularly vulnerable to margin compression, prompting many to pass costs onto clients or to consolidate testing windows, which may leave residual security gaps unattended.
Conversely, “Buy American” incentives and defense contract opportunities under the Trump administration’s trade policies have catalyzed growth among U.S.-based cybersecurity vendors, especially in intrusion detection, endpoint protection, and threat intelligence services. These domestic providers have rapidly scaled operations to fulfill defense innovation mandates, although continued reliance on globally sourced components underscores the need for a cohesive national manufacturing strategy.
Deep Dive into Security Market Segmentation Reveals How Components, Organization Sizes, Deployment Modes, Applications, and Verticals Intersect to Shape Industry Dynamics
Deep Dive into Security Market Segmentation Reveals How Components, Organization Sizes, Deployment Modes, Applications, and Verticals Intersect to Shape Industry Dynamics
A nuanced exploration by component shows that vulnerability management services span managed offerings, such as patch management as a service and vulnerability management as a service, alongside professional engagements including penetration testing and security assessment. On the solutions front, organizations deploy patch management software-available in both agent-based and agentless configurations-risk management platforms encompassing compliance and GRC modules, and threat intelligence suites that draw on internal telemetry and external feeds, complemented by vulnerability assessment tools tailored to cloud, host, or network environments.
Organizational scale further influences procurement and deployment choices. Large enterprises often favor comprehensive, integrated platforms capable of addressing global risk profiles, while small and medium businesses may lean toward flexible consumption models and turnkey managed services that alleviate in-house staffing pressures. This dichotomy extends into deployment modes, where cloud-native delivery models offer rapid scalability and tariff resilience, and on-premise implementations cater to stringent data sovereignty and latency requirements.
When viewed through the lens of application, the market bifurcates into core functional domains: patch management solutions-supporting both agent-based and agentless workflows-risk and compliance management platforms that specialize in compliance management and advanced risk analysis, threat intelligence offerings ranging from commercial feeds to open-source research, and vulnerability assessment frameworks that include both dynamic application security testing and static code analysis.
Industry verticals introduce further complexity as security priorities vary across banking, financial services, and insurance sectors focused on regulatory compliance; government entities driven by national security directives; healthcare organizations safeguarding patient data; IT and telecom providers integrating security into service delivery; and retail enterprises balancing customer experience with payment security obligations.
This comprehensive research report categorizes the Security & Vulnerability Management market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Organization Size
- Deployment Mode
- Application
- Industry Vertical
Regional Dynamics Shaping the Security and Vulnerability Management Landscape Across the Americas, Europe Middle East Africa, and Asia Pacific Growth Centres
Regional Dynamics Shaping the Security and Vulnerability Management Landscape Across the Americas, Europe Middle East Africa, and Asia Pacific Growth Centres
Across the Americas, aggressive digital transformation and robust regulatory frameworks have driven widespread adoption of advanced vulnerability management practices. U.S. federal initiatives, such as CISA’s Secure by Design pledge, are accelerating the integration of security within software development lifecycles, while enterprises pursue Zero Trust and SASE architectures to mitigate tariff-induced hardware cost pressures by shifting workloads to tariff-immune cloud environments.
In Europe, Middle East, and Africa, the rollout of the NIS2 Directive has underscored the critical need for cross-border coordination and supply chain risk management. Many organizations are still struggling to meet compliance milestones due to regulatory inconsistencies and legacy infrastructure, prompting calls for harmonized standards and enhanced guidance from ENISA. Concurrently, the EU’s move to establish its own vulnerability database signals a drive toward regional digital sovereignty and greater resilience amid global supply disruptions.
The Asia-Pacific region continues to contend with a surge in ransomware incidents and state-sponsored espionage campaigns targeting critical infrastructure, while major economies balance rapid AI adoption with emerging threat vectors. Reports indicate that over half of APAC CIOs experienced multiple breaches in the past year and face challenges in deriving value from underutilized security investments, driving demand for managed detection and response services and streamlined tool consolidation initiatives.
This comprehensive research report examines key regions that drive the evolution of the Security & Vulnerability Management market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Competitive Landscape Analysis Highlights Leading Innovators and Strategic Moves That Propel the Security and Vulnerability Management Sector Into the Future
Competitive Landscape Analysis Highlights Leading Innovators and Strategic Moves That Propel the Security and Vulnerability Management Sector Into the Future
The competitive arena is dominated by established security software giants alongside emerging specialists driving innovation through AI and cloud integration. Tenable and Qualys continue to lead in traditional vulnerability scanning, leveraging extensive paid customer bases and continuous product enhancements to maintain market leadership. Rapid7 and IBM have expanded orchestration and analytics capabilities, while Microsoft and AT&T harness their broad service portfolios to embed security within broader IT and telecom ecosystems. Broadcom’s acquisition of Symantec Enterprise Cloud has reinforced its position in threat intelligence, and companies such as OpenText and Skybox Security emphasize integrated risk management solutions across hybrid environments.
Mid-market challengers and niche players are also shaping the landscape by specializing in targeted segments. McAfee’s AI-driven vulnerability management system has reduced human assessment time by automating high-risk vulnerability identification, while Qualys’s recent cloud vulnerability offerings address the unique demands of hybrid and multi-cloud deployments. Fortra’s Tripwire solutions and Acunetix’s automated assessment tools underscore the importance of continuous evaluation and compliance, catering to vertical-specific requirements in regulated industries. Strategic partnerships and ecosystem integrations remain crucial as these vendors seek to deliver comprehensive, unified platforms that address the full spectrum of vulnerability management needs.
This comprehensive research report delivers an in-depth overview of the principal market players in the Security & Vulnerability Management market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- BeyondTrust Software, Inc.
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Holdings, Inc.
- Fortinet, Inc.
- International Business Machines Corporation
- McAfee, LLC
- Microsoft Corporation
- Palo Alto Networks, Inc.
- Qualys, Inc.
- Rapid7, Inc.
- Tenable Holdings, Inc.
- Trend Micro Incorporated
- Tripwire, Inc.
Actionable Strategic Directions Empower Industry Leaders to Strengthen Cyber Resilience, Optimize Vulnerability Management, and Future-Proof Their Operations
Actionable Strategic Directions Empower Industry Leaders to Strengthen Cyber Resilience, Optimize Vulnerability Management, and Future-Proof Their Operations
Industry leaders should prioritize the integration of AI-driven orchestration and advanced analytics to elevate vulnerability prioritization from volume-based scanning to risk-focused remediation. By adopting predictive modeling frameworks that incorporate historical exploit data and threat intelligence feeds, organizations can ensure that critical vulnerabilities are addressed proactively, reducing remediation workloads by up to 95% and maintaining high coverage of real-world threats.
A comprehensive Zero Trust strategy must be aligned with supply chain resilience initiatives to mitigate risks introduced by global trade dynamics. Embedding security into product design and vendor management processes, alongside leveraging tariff-immune cloud architectures, will enable enterprises to sustain performance while navigating fluctuating import costs and regulatory shifts. Complementing these technical measures with continuous compliance monitoring and cross-functional response drills will enhance organizational agility and reduce breach-recovery times.
Finally, fostering a security-first culture through targeted workforce development and executive governance is essential. Leaders should invest in continuous upskilling programs, scenario-based training, and executive briefings to ensure alignment across the board. Establishing clear risk-tolerance thresholds and decision-making frameworks will empower stakeholders at every level to act decisively when vulnerabilities are discovered, accelerating response workflows and reinforcing cyber resilience.
Rigorous Multi-Source Research Methodology Underpinning This Security and Vulnerability Management Analysis Ensures Robust Insights and Expert Validation
Rigorous Multi-Source Research Methodology Underpinning This Security and Vulnerability Management Analysis Ensures Robust Insights and Expert Validation
This report synthesizes insights from primary interviews with over 50 security and risk management executives, complemented by secondary data drawn from industry research firms, regulatory publications, and peer-reviewed academic studies. By triangulating these diverse data streams, we have ensured that our analysis reflects both on-the-ground practitioner experiences and empirical evidence from controlled experiments, such as those demonstrating efficiency gains in integrated prioritization frameworks.
Our quantitative assessments are informed by global surveys and market intelligence reports, capturing regional trends across the Americas, EMEA, and Asia-Pacific. We further validated key findings through workshops with cybersecurity practitioners, aligning our segmentation insights with real-world deployment patterns and organizational preferences for services, solutions, and delivery models. This iterative feedback loop has refined our understanding of evolving threat landscapes and the operational imperatives faced by industry leaders.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Security & Vulnerability Management market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Security & Vulnerability Management Market, by Component
- Security & Vulnerability Management Market, by Organization Size
- Security & Vulnerability Management Market, by Deployment Mode
- Security & Vulnerability Management Market, by Application
- Security & Vulnerability Management Market, by Industry Vertical
- Security & Vulnerability Management Market, by Region
- Security & Vulnerability Management Market, by Group
- Security & Vulnerability Management Market, by Country
- United States Security & Vulnerability Management Market
- China Security & Vulnerability Management Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 2862 ]
Conclusion Draws Together Key Findings on Trends, Tariff Impacts, Segmentation In-Depth Analysis, and Company Strategies to Illuminate the Path Forward
Conclusion Draws Together Key Findings on Trends, Tariff Impacts, Segmentation In-Depth Analysis, and Company Strategies to Illuminate the Path Forward
Taken together, the insights presented in this report underscore the critical intersection of technology innovation, regulatory dynamics, and global trade considerations in shaping the future of security and vulnerability management. The accelerating adoption of AI and automation, coupled with Zero Trust and hybrid cloud models, offers powerful levers for risk reduction, while evolving tariff regimes and supply chain complexities demand resilient, cloud-forward strategies. Segmentation analysis reveals that no single solution fits all; enterprises must tailor their approaches based on organizational scale, deployment preferences, application focus, and sector-specific requirements. The competitive landscape is marked by both incumbents leveraging expansive ecosystems and niche players driving deep specialization, ensuring that organizations have access to a rich array of capabilities. By applying the actionable recommendations outlined herein, industry leaders can navigate this dynamic environment with confidence, optimizing resource allocation, strengthening defensive postures, and maintaining a strategic advantage in an increasingly contested digital domain.
Take Immediate Action to Secure Comprehensive Security and Vulnerability Management Insights by Connecting with Ketan Rohom for Exclusive Report Access
Take Immediate Action to Secure Comprehensive Security and Vulnerability Management Insights with Exclusive Report Access
Elevate your strategic decision-making by undertaking a thorough review of the latest security and vulnerability management research. To empower your organization with actionable intelligence and customized strategic guidance, we invite you to engage directly with Ketan Rohom, Associate Director of Sales & Marketing. His expertise will ensure you gain prompt access to the in-depth report, tailored executive briefings, and advanced analytics dashboards designed to accelerate your cybersecurity initiatives and strengthen your competitive advantage. Reach out today to secure your organization’s place at the forefront of security innovation and resilience.

- How big is the Security & Vulnerability Management Market?
- What is the Security & Vulnerability Management Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




