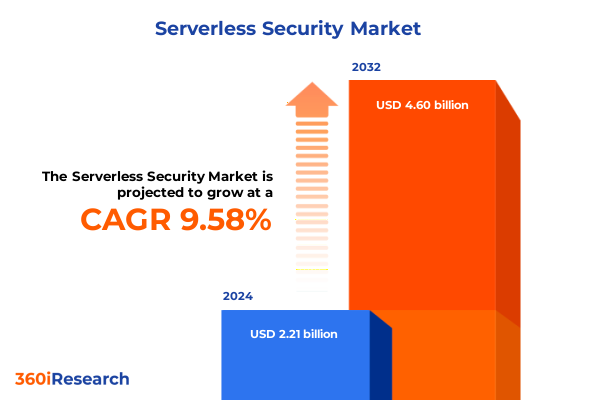
The Serverless Security Market size was estimated at USD 2.39 billion in 2025 and expected to reach USD 2.59 billion in 2026, at a CAGR of 9.80% to reach USD 4.60 billion by 2032.
Pioneering Robust Defense Strategies for Next Generation Serverless Applications Amid Escalating Cyber Threats and Operational Complexity
The rapid adoption of serverless computing has shifted the paradigm of cloud-native application development, introducing both unparalleled flexibility and novel security challenges. As organizations increasingly delegate infrastructure management to cloud providers, the traditional perimeter-based defenses become insufficient, necessitating security strategies that are inherently entwined with ephemeral execution environments.
In this evolving context, the protection of function-level assets demands visibility into transient workloads, granular enforcement of identity and access controls, and continuous monitoring of API interactions. Concurrently, the acceleration of development cycles through continuous integration and continuous delivery (CI/CD) pipelines has heightened the need for security solutions to integrate seamlessly into automated workflows, ensuring that risk is addressed at the earliest stages of code deployment. With these dynamics in play, stakeholders must craft defense approaches that not only safeguard against known vulnerabilities but also anticipate emerging threats unique to serverless architectures.
This executive summary introduces a comprehensive exploration of the serverless security landscape, illuminating transformative market shifts, the implications of recent policy adjustments, and key segmentation insights. The goal is to equip decision-makers with a clear understanding of how to fortify their serverless deployments, optimize strategic investments, and embrace innovative safeguards that align with organizational objectives and compliance requirements.
Unveiling Critical Technological and Operational Shifts Redefining Serverless Security Posture Across Global Cloud Ecosystems
Serverless security is undergoing a profound transformation as enterprises confront the limitations of legacy monitoring tools and embrace more sophisticated approaches. One significant shift is the transition from static vulnerability assessments to dynamic threat detection powered by real-time telemetry and machine learning. This evolution allows teams to identify anomalous behavior in function invocations, trace lateral movement within microservice chains, and enforce contextual safeguards that adapt to variable workloads.
In parallel, the maturation of identity-aware proxies and zero trust frameworks has reframed how trust is established and maintained in serverless environments. Rather than relying on network location or traditional firewalls, modern architectures enforce granular permissions at the function and API level, ensuring that each invocation is authenticated, authorized, and recorded. Additionally, the rise of infrastructure as code incorporates security policies directly into deployment templates, enabling consistent configuration management across hybrid and multi-cloud landscapes.
Moreover, the increasing integration of serverless workloads into edge computing and container orchestration platforms underscores the need for cohesive runtime protection mechanisms. Techniques such as sandboxing and runtime application self-protection (RASP) have gained prominence, offering defense-in-depth that spans both vendor-managed function runtimes and customer-controlled environments. These transformative shifts are redefining how organizations anticipate threats, allocate resources, and architect security controls for serverless adoption.
Assessing the Far-Reaching Consequences of 2025 United States Tariff Measures on Serverless Security Supply Chains and Operational Costs
In 2025, the United States government implemented a series of tariff measures targeting imports of critical hardware components, cryptographic accelerators, and specialized serverless tooling. Although these policies aim to stimulate domestic manufacturing and protect intellectual property, they have also introduced cost pressures and supply chain complexities for security solution providers and end-users.
Organizations dependent on imported silicon-based security modules have encountered extended lead times and higher component prices, prompting teams to reevaluate vendor relationships and diversify their supply sources. As a result, many enterprises are exploring alternative architectures that favor software-based encryption and zero trust overlays over hardware-bound key management systems. This shift necessitates careful assessment of performance trade-offs, regulatory compliance, and interoperability with existing legacy systems.
Furthermore, the increased duties on software licenses and managed security services have impacted subscription pricing models, driving interest in open-source and community-driven security projects. While these alternatives can mitigate immediate financial burdens, they require rigorous validation and ongoing maintenance to match the controls offered by commercial offerings. Ultimately, the cumulative effect of these tariff policies underscores the importance of resilient procurement strategies, collaborative partnerships, and adaptable security roadmaps that can absorb market fluctuations without compromising the integrity of serverless deployments.
Illuminating Core Segmentation Dimensions Driving Tailored Security Solutions Across Service Models Deployment Regions and Industry Verticals
A nuanced understanding of market segmentation reveals that security requirements diverge significantly depending on the underlying service model. In environments where Backend-as-a-Service offerings predominate, organizations must prioritize data encryption at rest and in transit, ensuring that object stores and database bindings remain protected even as service endpoints scale automatically. Conversely, Function-as-a-Service deployments demand robust runtime protection controls, such as container security and sandbox security, to address the transient nature of workloads and to prevent privilege escalation across distributed invocations.
When examining specific solution types, API security emerges as a foundational control, encompassing access control mechanisms, advanced threat detection, and real-time usage monitoring to thwart unauthorized or anomalous requests. Simultaneously, compliance management solutions must integrate audit and reporting capabilities alongside policy management workflows, enabling governance teams to substantiate regulatory adherence across multi-cloud infrastructures. The diversity of encryption strategies-from key management systems to transport layer encryption-further underscores the need to tailor approaches based on performance, regulatory, and risk tolerance criteria.
The identity and access management domain demands multi-factor authentication for sensitive function invocations, privilege management to enforce least-privilege access, and single sign-on integration to streamline developer workflows. By contrast, runtime security layers, including runtime application self-protection, provide introspective defenses that adapt to runtime contexts and application logic. Across hybrid cloud, private cloud, and public cloud deployments, these controls require continuous synchronization to maintain policy consistency and to support seamless failover and load balancing.
Industry-specific considerations also shape segmentation strategies. Financial services and insurance firms, along with public sector agencies, often mandate stringent audit trails and cryptographic attestations, whereas healthcare and retail providers place a premium on data privacy and cardholder data security. Information technology and telecom companies, which frequently act as both service providers and consumers, demand highly extensible platforms capable of accommodating rapid feature evolution. Meanwhile, organizational scale influences procurement and governance practices: large enterprises typically engage managed security service providers in complex multi-vendor ecosystems, whereas small and medium enterprises prioritize turnkey solutions with rapid deployment cycles.
This comprehensive research report categorizes the Serverless Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Service Type
- Security Solution Type
- Deployment Model
- End Use Industry
- Organization Size
Delving into Regional Nuances Shaping Serverless Security Adoption Trends Innovations and Compliance Imperatives Across Global Markets
Regional dynamics exert a profound influence on serverless security priorities and adoption trajectories. In the Americas, organizations leverage well-established cloud infrastructures and robust security ecosystems, enabling accelerated deployment of advanced controls such as runtime protection and zero trust microsegmentation. Regulatory frameworks such as the California Consumer Privacy Act and sector-specific guidelines drive demand for integrated compliance management and standardized audit reporting, fostering a mature market characterized by strategic vendor partnerships.
Across Europe, the Middle East, and Africa, the interplay between stringent data protection regulations like GDPR and regional sovereignty requirements shapes bespoke security designs. Enterprises in this region often adopt hybrid deployments, balancing public cloud scalability with private cloud isolation to satisfy cross-border data flow restrictions. This approach amplifies the need for unified policy orchestration, ensuring consistent encryption key management and identity governance across dispersed infrastructures.
In the Asia-Pacific region, rapid digital transformation and the proliferation of mobile-first applications have accelerated the uptake of serverless frameworks. Cost sensitivities and diverse compliance landscapes, spanning data localization in India to cybersecurity mandates in Australia, compel organizations to evaluate lightweight, API-centric security solutions. Consequently, local managed service providers and niche security players have introduced context-aware threat detection and lightweight access control capabilities optimized for high-volume, low-latency use cases. These regional insights underscore the criticality of adapting security strategies to evolving regulatory, economic, and technological environments.
This comprehensive research report examines key regions that drive the evolution of the Serverless Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Leading Security Innovators in Serverless Ecosystems Driving Boundary-Pushing Solutions and Shaping Industry Standards
Leading technology providers and security specialists are accelerating innovation to address the unique requirements of serverless environments. Major cloud platform vendors have expanded their native offerings to include enhanced encryption key management, identity federation services, and integrated API protection features, allowing customers to embed security directly into development pipelines without incurring performance penalties.
At the same time, specialized security vendors are differentiating through advanced threat intelligence integrations, offering developers context-rich analytics that correlate anomalous function behavior with emerging attack campaigns. These companies leverage container security innovations to create seamless visibility across serverless workloads, across both managed function runtimes and self-hosted environments. By embedding runtime application self-protection agents and sandboxing capabilities, they deliver defense layers that adapt in real time to shifting workloads and code changes.
Partnerships between cloud providers and independent security firms have given rise to managed detection and response offerings tailored for serverless architectures. These collaborative models enable organizations to outsource continuous monitoring and incident response, while retaining granular control over policy configurations and cryptographic assets. Collectively, these key companies are setting industry benchmarks for interoperability, automation, and developer-centric security tooling, shaping the trajectory of serverless protection standards.
This comprehensive research report delivers an in-depth overview of the principal market players in the Serverless Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike, Inc.
- Fortinet, Inc.
- Google LLC
- International Business Machines Corporation
- McAfee Corp.
- Microsoft Corporation
- Orca Security
- Palo Alto Networks, Inc.
- Trend Micro Incorporated
Empowering Industry Leaders with Strategic Roadmaps to Fortify Serverless Deployments Through Proactive Risk Mitigation and Continuous Innovation
To navigate the intricate serverless security landscape, industry leaders should adopt a proactive risk management mindset, integrating security at every stage of the application lifecycle. By embedding automated API security tests within CI/CD pipelines, development teams can catch misconfigurations and injection vulnerabilities early, significantly reducing the likelihood of runtime exploits. Furthermore, leveraging policy-as-code frameworks ensures that infrastructure as code templates adhere to organizational and regulatory standards from inception through deployment.
Beyond development practices, organizations must implement zero trust principles for function-to-function communication, enforcing strict identity and access management controls that validate each invocation. Continuous monitoring with context-aware threat detection enables rapid identification of anomalous patterns, while runtime application self-protection fortifies functions against in-memory attacks and sophisticated exploitation techniques. Adopting container security measures, such as vulnerability scanning of base images and sandboxing of execution environments, further strengthens the defense-in-depth posture.
Strategic vendor selection plays a pivotal role in operational resilience. Industry leaders should evaluate providers based on their ability to deliver flexible deployment models-including hybrid, private, and public cloud integrations-alongside comprehensive compliance management and encryption services. By fostering collaborative relationships and negotiating transparent service-level agreements, organizations can ensure consistent policy enforcement, predictable performance, and effective incident response support.
Ultimately, a holistic approach that combines early-stage security automation, continuous runtime protection, and adaptive vendor partnerships will empower enterprises to stay ahead of emerging threats, optimize resource allocation, and achieve sustainable competitive advantages in serverless adoption.
Unraveling Rigorous Research Frameworks and Analytical Approaches Underpinning In-Depth Insights into Serverless Security Market Dynamics
This research leverages a multi-faceted methodology, beginning with an extensive review of publicly available documentation, technical whitepapers, and regulatory guidelines to establish a foundational understanding of serverless security principles. Complementing this secondary research, primary interviews were conducted with cloud security architects, DevSecOps practitioners, and compliance officers to capture real-world challenges, tool preferences, and best practices.
To quantify market dynamics, a structured survey of IT and security decision-makers across diverse industries was administered, focusing on deployment models, security solution adoption, and perceived gaps in existing controls. The survey findings were triangulated with vendor product briefings and independent technology evaluations to validate feature sets and performance benchmarks. Additionally, expert workshops involving cross-functional stakeholders provided qualitative insights into emerging use cases, trust models, and integration strategies.
Analytical frameworks such as SWOT and PESTEL were applied to assess internal strengths, external opportunities, and macro-environmental factors affecting the serverless security ecosystem. Scenario planning exercises illustrated the potential impact of regulatory changes, tariff policies, and technological innovations on future adoption trends. The synthesis of quantitative data and qualitative feedback ensures that the report’s conclusions are grounded in robust evidence, offering decision-makers a clear, actionable perspective on evolving market conditions.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Serverless Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Serverless Security Market, by Service Type
- Serverless Security Market, by Security Solution Type
- Serverless Security Market, by Deployment Model
- Serverless Security Market, by End Use Industry
- Serverless Security Market, by Organization Size
- Serverless Security Market, by Region
- Serverless Security Market, by Group
- Serverless Security Market, by Country
- United States Serverless Security Market
- China Serverless Security Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1749 ]
Converging Insights and Strategic Imperatives to Elevate Serverless Security Resilience and Drive Sustainable Competitive Advantages
In an environment defined by relentless innovation and escalating threat vectors, serverless architectures demand a security mindset that is both adaptive and anticipatory. The convergence of dynamic execution models, granular identity controls, and distributed policy frameworks underscores the imperative for comprehensive, end-to-end protection strategies. By synthesizing insights across technological shifts, tariff-induced market pressures, segmentation nuances, and regional considerations, organizations can craft resilient security architectures that withstand uncertainty.
As key vendors refine their offerings and standards evolve, the onus lies with enterprise leaders to integrate automated security practices into their development lifecycles, to align with regulatory mandates, and to continuously calibrate defenses through data-driven feedback loops. The collective insights presented in this report provide a strategic blueprint for navigating the complex interplay between innovation, compliance, and operational resilience.
Looking ahead, the maturation of AI-driven threat detection, the proliferation of edge-native serverless patterns, and potential adjustments in trade policies will further influence security postures. It is essential for decision-makers to remain engaged with the latest developments, to cultivate agile procurement strategies, and to invest in collaborative partnerships that deliver both technical excellence and strategic foresight. Ultimately, a holistic, forward-looking approach will unlock the full promise of serverless computing while safeguarding critical digital assets.
Initiate a Comprehensive Engagement with Ketan Rohom to Harness Tailored Insights and Secure Your Serverless Future Today
To explore the full depth of these insights and to secure comprehensive guidance tailored to your organization’s unique serverless security challenges, reach out to Ketan Rohom, Associate Director of Sales & Marketing. By engaging directly with Ketan, you can request a customized briefing, discuss integration scenarios, and obtain exclusive access to detailed chapters of the report. Empower your team with the strategic foresight and specialized expertise required to navigate the complexities of modern serverless environments and to proactively defend against emerging threats.

- How big is the Serverless Security Market?
- What is the Serverless Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




