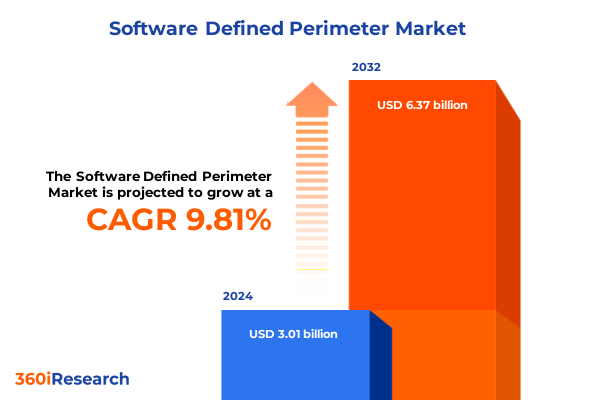
The Software Defined Perimeter Market size was estimated at USD 3.22 billion in 2025 and expected to reach USD 3.45 billion in 2026, at a CAGR of 10.21% to reach USD 6.37 billion by 2032.
Unlocking Adaptive Security: How Software Defined Perimeter Frameworks Are Redefining Access Control for Modern Enterprise Networks
The exponential growth of remote workforces, cloud migrations, and digital ecosystems has fundamentally challenged traditional network perimeters. Modern enterprises can no longer rely on legacy firewalls and VPNs to protect sensitive assets and maintain seamless connectivity across distributed environments. Software Defined Perimeter (SDP) technology emerges as a strategic response, enabling dynamic, identity-centric access controls that adapt to user context, device posture, and network conditions. By leveraging policy orchestration and microsegmentation, organizations can effectively conceal critical resources and only reveal them when strict authentication and authorization criteria are met. Transitioning from static network boundaries to agile, software-driven perimeters empowers security teams to proactively mitigate threats, reduce attack surfaces, and deliver consistent user experiences regardless of location or infrastructure topology.
Amid accelerated adoption of cloud-native applications and hybrid architectures, Software Defined Perimeter has become a cornerstone of next-generation security frameworks. Its underlying principles align closely with zero trust models, which assume no inherent trust between users, devices, or network segments. By integrating SDP into broader security ecosystems, organizations realize benefits such as granular access policies, reduced lateral movement, and real-time threat resilience. As digital transformation initiatives reshape business operations, understanding SDP fundamentals and its transformational potential becomes essential for enterprise leaders seeking to safeguard critical data, comply with stringent regulations, and gain a competitive edge in an increasingly threat-intense environment.
Navigating the Security Revolution Driven by Zero Trust Principles and Cloud-Native Perimeter Architectures Adapting to Hybrid Workforces
The landscape of network security is undergoing transformative shifts driven by the rapid convergence of zero trust principles, cloud-native architectures, and evolving threat vectors. Zero trust has transcended a theoretical concept to become an operational imperative, compelling organizations to rethink how identities, applications, and data communicate. Software Defined Perimeter implementations now serve as a foundational element for this paradigm, enforcing “never trust, always verify” policies across diverse endpoints and networks. This shift is further amplified by the proliferation of edge computing and IoT devices, which demand a more distributed and adaptive security posture.
Concurrently, the adoption of cloud services and containerized applications has introduced new complexities, as data and workloads span public, private, and hybrid environments. Traditional security controls struggle to maintain visibility and consistency across these heterogeneous landscapes. In contrast, Software Defined Perimeter solutions offer API-driven policy management and automated enforcement that seamlessly extends to dynamic workloads in the cloud or at the network edge. Moreover, the global transition toward hybrid work models has heightened demand for secure, low-latency remote access, making SDP a key enabler of productivity and resilience. As threat actors exploit configuration gaps and misaligned access controls, the ability to apply unified, software-centric security controls across all communication channels represents a vital evolution in protecting modern digital ecosystems.
Assessing the Cascading Effects of 2025 United States Tariffs on Software Defined Perimeter Adoption and Technology Supply Chains
The imposition of new United States tariffs in 2025, targeting a broad spectrum of hardware, software, and component imports, has introduced notable complexities for organizations deploying Software Defined Perimeter solutions. Increased duties on networking appliances, specialized cryptographic modules, and endpoint hardware have driven up capital expenditures for on-premises SDP controller units and gateways. This tariff-driven escalation in acquisition costs has compelled many enterprises to reevaluate deployment strategies, accelerating migration toward subscription-based, cloud-hosted SDP services that minimize dependencies on imported equipment.
In response to cost pressures, security architects are placing greater emphasis on software-centric, vendor-agnostic SDP implementations leveraging local infrastructure and open standards. By adopting lightweight agents and leveraging existing compute resources, organizations mitigate the impact of elevated hardware tariffs while preserving robust access control mechanisms. At the same time, the tariffs have stimulated a shift in supply chain dynamics: domestic providers of semiconductors and specialized network components are scaling operations to meet new demand, and partnerships between service providers and regional manufacturers have proliferated. These developments have fostered a more diversified, resilient ecosystem for SDP deployments, where procurement risks are distributed across multiple geographies and vendors.
Furthermore, the cumulative impact of 2025 tariffs has underscored the value proposition of integrated, policy-driven security platforms. Organizations are increasingly bundling SDP capabilities with broader cloud security suites to achieve operational efficiencies and cost savings through unified licensing and management frameworks. In doing so, they not only sidestep the volatility introduced by hardware tariffs but also enhance their overall security posture by consolidating vendor relationships and standardizing policy enforcement across multi-cloud environments. This tariff-induced realignment is poised to have lasting implications for how enterprises architect and procure their perimeter security solutions.
Unlocking Market Nuances Through Component, Authentication, Deployment, Industry Vertical, and Organizational Size Segmentation Dynamics
Diving into market segmentation reveals nuanced behaviors and adoption patterns across multiple dimensions of the Software Defined Perimeter ecosystem. When examining component type, services and solutions each reveal distinct demand drivers: managed services emphasize continuous monitoring, threat detection, and policy optimization delivered by specialized security teams, whereas professional services focus on accelerated deployment, bespoke integration, and architectural consultation. On the solutions side, SDP controllers orchestrate dynamic policy distribution and centralized administration, while gateways enforce access rules and segment network traffic at the edge of protected resources.
Authentication type serves as a critical axis of differentiation, with organizations tailoring their approaches based on risk tolerance and user experience requirements. Biometric authentication unlocks frictionless access for employees under strict regulatory regimes, while certificate-based mechanisms ensure cryptographic integrity across machine-to-machine communications. Multi-factor authentication combines two or more validation factors to strike a balance between security and usability, and token-based methods facilitate ephemeral session credentials for contractors and third-party partners.
The choice of deployment model reflects organizational priorities and existing infrastructure portfolios. Cloud-based implementations leverage public and private cloud environments to scale elastically, hybrid approaches blend on-premises assets with cloud-hosted components for agility, and on-premises installations maintain full control over data residency and regulatory compliance. Within hybrid and cloud paradigms, distinctions between private and public clouds influence network performance, integration effort, and operational governance.
Industry verticals such as banking, financial services, and insurance demand granular segmentation to comply with stringent privacy regulations and safeguard customer transactions, while government and defense sectors prioritize sovereign data controls and hardened access protocols. Healthcare providers address patient confidentiality and medical device security needs, and IT and telecommunications firms integrate SDP to support high-volume network traffic and carrier-grade service level agreements. Organization size further shapes adoption strategies: large enterprises often lead with pilot programs and phased rollouts, whereas small and medium businesses prioritize turnkey solutions that minimize internal resource commitments.
This comprehensive research report categorizes the Software Defined Perimeter market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component Type
- Authentication Type
- Deployment Model
- Industry Vertical
- Organization Size
Strategic Growth Patterns Emerging Across the Americas, Europe Middle East Africa, and Asia Pacific in Software Defined Perimeter Deployments
Geographic analysis of the Software Defined Perimeter market uncovers a tapestry of regional variations influenced by regulatory environments, technological maturity, and investment priorities. In the Americas, forward-looking enterprises across North and South America are capitalizing on digital transformation mandates and cybersecurity regulations to modernize access controls. Leading financial institutions, technology firms, and public sector bodies are deploying SDP architectures to secure complex, multi-site operations and accelerate cloud adoption.
Meanwhile, Europe, the Middle East, and Africa present a spectrum of adoption drivers, ranging from the European Union’s stringent data protection directives to the Middle East’s national security imperatives. Organizations in Western Europe are integrating SDP within broader network function virtualization strategies, whereas in the Middle East and Africa, rapid infrastructure buildouts and smart city initiatives have sparked targeted investments in next-generation perimeter security to guard critical utilities and government networks.
In the Asia-Pacific region, dynamic economic growth and technological innovation have catalyzed widespread interest in SDP solutions. Countries in East Asia and Oceania are advancing cloud-first policies, encouraging local data center expansions and strategic collaborations between multinational vendors and domestic solution providers. Southeast Asian markets, fueled by a burgeoning digital services sector, are balancing cost optimization with rapid scaling, leveraging SDP to secure remote access for growing workforces and distributed supply chains.
Across all three regions, public-private partnerships and cross-border initiatives are emerging to standardize best practices, streamline procurement processes, and cultivate local expertise. Such collaborative frameworks help to mitigate regional disparities in technical skills and integration capabilities, ensuring that enterprises of all sizes can harness the benefits of software defined perimeter technologies to safeguard critical assets and foster global interoperability.
This comprehensive research report examines key regions that drive the evolution of the Software Defined Perimeter market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Leading Innovators and Strategic Collaborators Shaping Software Defined Perimeter Ecosystem Through Cutting-Edge Offerings
The software defined perimeter landscape is shaped by an ecosystem of established security vendors, emerging specialists, and open-source initiatives, each bringing unique capabilities to the table. Industry leaders with mature SDP portfolios have expanded their offerings to integrate advanced analytics, user behavior modeling, and threat intelligence feeds. These vendors emphasize seamless integration with existing security information and event management systems, positioning SDP as a critical component in their broader secure access service edge roadmaps.
Emerging players differentiate themselves through hyper-focused innovation in areas like distributed gateway orchestration, lightweight client provisioning, and real-time policy auto-tuning. By prioritizing ease of deployment and developer-centric toolkits, these specialists appeal to organizations seeking rapid time to value and minimal operational overhead. Partnerships between technology vendors and managed service providers have also intensified, enabling turnkey solutions that combine technical expertise, around-the-clock support, and compliance reporting services.
Open-source projects and standards bodies have contributed to the maturing of the SDP ecosystem by fostering interoperability and vendor neutrality. Specifications for secure service identity, certificate issuance, and mutual TLS handshakes drive consistency across disparate implementations. Community-driven repositories of templates, code samples, and best practice guides accelerate proof-of-concept efforts for enterprises exploring SDP architectures for the first time.
Collectively, these dynamics are catalyzing a competitive environment that rewards continuous innovation, ecosystem collaboration, and strong customer support models. As the perimeter security ecosystem evolves, both established and emergent players are refining their strategies to address integration challenges, reduce total cost of ownership, and deliver seamless, policy-driven access experiences.
This comprehensive research report delivers an in-depth overview of the principal market players in the Software Defined Perimeter market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Cloudflare, Inc.
- Fortinet, Inc.
- Juniper Networks, Inc.
- Microsoft Corporation
- Palo Alto Networks, Inc.
- Palo Alto Networks, Inc.
- VMware, Inc.
- Zscaler, Inc.
Implementing Proactive Security Frameworks and Collaborative Governance Models to Advance Software Defined Perimeter Adoption and Resilience
Organizations aiming to capitalize on software defined perimeter benefits should begin by aligning security and network teams under a unified governance framework. Early engagement of stakeholders across IT operations, compliance, and application development ensures that access policies reflect both technical requirements and business objectives. Conducting pilot programs in controlled environments allows for iterative tuning of policy engines, user authentication workflows, and logging configurations before enterprise-wide rollouts.
It is advisable to adopt a phased deployment strategy that starts with low-risk, high-impact use cases-such as securing remote administration interfaces and third-party vendor connections-and progressively extends perimeter controls to internal applications and critical data repositories. Integrating SDP with existing identity providers, security orchestration platforms, and endpoint management tools not only streamlines user provisioning but also delivers unified visibility into authentication events and policy violations.
To mitigate skills gaps, organizations should invest in targeted training and certification programs, ensuring that security engineers and network architects become proficient with SDP orchestration consoles, API integrations, and agent deployments. Collaboration with managed security service partners can provide immediate operational support and knowledge transfer, reducing time to value and enhancing incident response capabilities.
Finally, enterprises must establish continuous monitoring and improvement processes. Regular policy audits, red team exercises, and threat hunting activities reveal misconfigurations and emergent vulnerabilities. By embedding SDP metrics into broader security performance dashboards, leaders can track key indicators-such as time to authenticate, unauthorized access attempts, and compliance adherence-and refine strategies accordingly. This holistic approach equips organizations with the agility and resiliency required to defend against evolving threats while maintaining seamless user experiences.
Employing a Rigorous Multi-Phase Research Approach Integrating Qualitative Interviews and Quantitative Data Analysis for Comprehensive Market Insights
This research leverages a multi-phase approach combining both primary and secondary data collection methods to deliver comprehensive insights into software defined perimeter trends. Initial desk research synthesized industry reports, regulatory documents, and technical white papers to identify market drivers, technology architectures, and emerging threat vectors. These findings informed the development of structured interview guides and survey instruments.
In the primary research phase, in-depth interviews were conducted with senior security executives, network architects, and solution integrators across diverse industries. These qualitative interactions uncovered real-world deployment challenges, evolving security policies, and strategic priorities guiding SDP adoption. Concurrently, a quantitative survey captured adoption rates, preferred feature sets, and budgetary considerations, enabling validation of qualitative themes and identification of segmentation-based differences.
Data triangulation and cross-validation were achieved through consolidation workshops with subject matter experts, ensuring accuracy and minimizing bias. Analytical techniques, including correlation analysis and thematic coding, were applied to distill key insights and identify patterns across organizational sizes, verticals, and regions. The resulting framework delivers both depth and granularity, equipping decision-makers with actionable intelligence backed by methodological rigor.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Software Defined Perimeter market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Software Defined Perimeter Market, by Component Type
- Software Defined Perimeter Market, by Authentication Type
- Software Defined Perimeter Market, by Deployment Model
- Software Defined Perimeter Market, by Industry Vertical
- Software Defined Perimeter Market, by Organization Size
- Software Defined Perimeter Market, by Region
- Software Defined Perimeter Market, by Group
- Software Defined Perimeter Market, by Country
- United States Software Defined Perimeter Market
- China Software Defined Perimeter Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1431 ]
Synthesis of Industry Transformations and Strategic Pathways Highlighting Software Defined Perimeter’s Role in Fortifying Future Network Security Landscapes
The evolution of network security is at an inflection point, where traditional perimeters dissolve into dynamic, software-driven boundaries. Software defined perimeter solutions offer a proven mechanism for enforcing zero trust principles, enabling organizations to adapt to fluid architectures, mitigate sophisticated threats, and maintain regulatory compliance. Through segmentation by component, authentication, deployment model, vertical, and organization size, it becomes clear that SDP’s flexibility addresses the unique challenges of each enterprise environment.
Regional insights further underscore the importance of contextual strategies-from regulatory-driven deployments in Europe to cloud-first initiatives in Asia-Pacific and integrated transformation programs in the Americas. Additionally, the cumulative effects of the 2025 US tariffs have accelerated shifts toward cloud-centric models and software-only implementations, reshaping procurement and supply chain approaches.
Innovative vendors and collaborative ecosystems continue to drive technology enhancements, while leading organizations demonstrate that successful SDP adoption hinges on strong governance, phased rollouts, and continuous policy refinement. By embracing these principles, enterprises can elevate their security posture, reduce attack surfaces, and deliver seamless, context-aware access to users worldwide. This convergence of strategy, technology, and operational excellence heralds a new era of resilient network security for the digital age.
Secure Your Competitive Edge Now by Engaging with Our Associate Director to Unlock Exclusive Software Defined Perimeter Market Intelligence and Guidance
To gain comprehensive visibility into evolving perimeter security strategies and to stay ahead of both emerging threats and market dynamics, reach out to Ketan Rohom, our Associate Director of Sales & Marketing. Ketan brings a deep understanding of your challenges and will guide you through our latest market research findings with tailored insights and recommendations. Don’t miss the opportunity to empower your organization with advanced strategies and actionable intelligence that will define your competitive advantage in the software defined perimeter space

- How big is the Software Defined Perimeter Market?
- What is the Software Defined Perimeter Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




