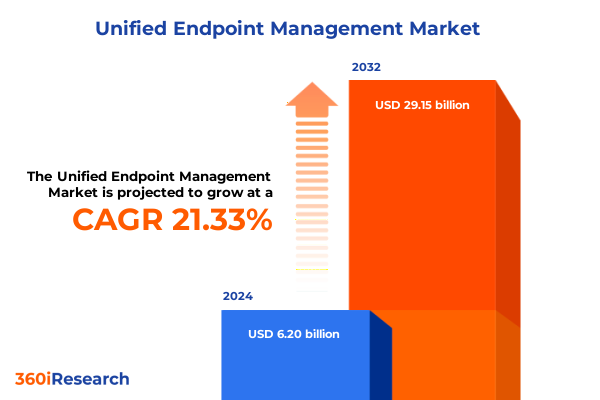
The Unified Endpoint Management Market size was estimated at USD 7.50 billion in 2025 and expected to reach USD 8.99 billion in 2026, at a CAGR of 21.39% to reach USD 29.15 billion by 2032.
Pioneering a Holistic Approach to Unified Endpoint Management to Secure, Simplify, and Reinforce Complex Device and Application Ecosystems
The rapid proliferation of devices across enterprise environments has ushered in a pivotal moment for technology leaders: the imperative to adopt Unified Endpoint Management as the linchpin of device governance. No longer can organizations rely on disparate tools to manage laptops, smartphones, tablets, and specialized IoT endpoints. Instead, the convergence of security, compliance, and user experience under a single management umbrella has become essential to mitigate risk and maintain agility. This shift reflects a fundamental transformation in how businesses envision control, moving beyond isolated device policies toward a cohesive framework that streamlines administration, accelerates response times, and reduces operational friction.
Moreover, the growing sophistication of cyberthreats demands a proactive stance in endpoint defense. Today’s security teams must collaborate seamlessly with IT operations, integrating threat intelligence and automated remediation to neutralize vulnerabilities before they can be exploited. As organizations embrace remote and hybrid work models, the boundaries between corporate networks and external environments blur, intensifying the need for a unified approach that spans on-premises and cloud infrastructures alike. In this environment, Unified Endpoint Management emerges as the strategic foundation upon which secure, scalable, and future-ready device ecosystems are built
Navigating Transformative Shifts in the Unified Endpoint Management Landscape Driven by Zero Trust, AI Integration, and Hybrid Work Models
Recent advancements in artificial intelligence and machine learning have catalyzed transformative shifts in the Unified Endpoint Management landscape, redefining both threat detection and user experience. By embedding predictive analytics directly into endpoint controls, leading solutions can preemptively identify anomalous behavior, triggering automated policy enforcement or remediation workflows without manual intervention. This evolution reflects a broader trend toward intelligent orchestration, where the synergy of real-time telemetry and dynamic policy engines ensures continuous compliance and adaptive defense.
Simultaneously, the embrace of zero trust principles has reshaped organizational security architectures. Rather than assuming inherent trust based on network location or device ownership, zero trust enforces rigorous verification for every access request, driving tighter integration between identity and access management capabilities and endpoint governance. Furthermore, the ubiquity of hybrid work-where employees switch seamlessly between corporate networks, home offices, and public hotspots-has elevated the importance of consistent policy application. Consequently, enterprises are prioritizing cloud-native UEM platforms that offer unified consoles and cross-platform consistency, enabling IT teams to manage device lifecycles from deployment through decommissioning with unprecedented agility
Unpacking the Cumulative Effects of 2025 United States Tariff Changes on Endpoint Management Supply Chains and Strategic Cost Structures
The introduction of new tariff measures in the United States during early 2025 has created a complex backdrop for device procurement and lifecycle management. Hardware manufacturers and resellers have adjusted pricing models to absorb additional import duties, leading many organizations to renegotiate vendor contracts and explore alternate supply channels. These cost pressures have, in turn, influenced refresh cycles, as enterprises balance budget constraints against the imperative to maintain robust endpoint security postures.
Beyond immediate cost implications, the tariffs have accelerated strategic decision-making around onshoring and nearshoring device assembly. Technology leaders are increasingly evaluating partnerships with domestic original equipment manufacturers to mitigate exposure to shifting trade policies, while also considering refurbished and certified pre-owned hardware as viable alternatives. Consequently, IT procurement teams must close the gap between financial planning and security requirements, ensuring that tariff-driven cost optimization does not compromise the integrity of managed endpoints or obscure critical compliance obligations
Deriving Critical Segmentation Insights from Component to Device and Operating System Dimensions to Inform Targeted UEM Strategies
A comprehensive understanding of Unified Endpoint Management requires dissecting the market through multiple lenses, beginning with the distinction between services and solutions. Managed services deliver ongoing oversight and remote remediation across device portfolios, whereas professional services guide strategic implementation and architecture design. On the solutions front, security modules protect against malware and unauthorized access, identity and access management components enforce robust authentication, mobile application management streamlines software distribution, and mobile device management governs hardware configurations and patch updates.
Deployment preferences further diversify the market: cloud-based platforms offer rapid scalability and simplified upgrades, while on-premises installations grant enterprises granular control over sensitive data and custom integrations. Organizational scale introduces another dimension of complexity, as large enterprises demand enterprise-grade performance, extensive customization, and global support networks whereas small and medium-sized enterprises often favor turnkey UEM suites that reduce overhead and accelerate time to value. Industry verticals from banking, financial services, and insurance to education, government and defense, healthcare, IT and telecom, manufacturing, retail, and transportation and logistics each impose distinct regulatory, compliance, and operational requirements that shape UEM feature prioritization. Device diversity remains a constant driver: laptops and desktops continue to account for the core worker base, while smartphones and tablets power frontline work and customer engagement. Finally, operating systems spanning Android, iOS, Linux, MacOS, and Windows introduce unique security models and management APIs, compelling UEM vendors to deliver deep integrations that span the full spectrum of enterprise endpoints
This comprehensive research report categorizes the Unified Endpoint Management market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Deployment Mode
- Organization Size
- Industry Vertical
- Device Type
Unveiling Regional Dynamics Shaping Unified Endpoint Management Adoption across the Americas, EMEA, and Asia-Pacific Markets
Regional dynamics play a pivotal role in shaping Unified Endpoint Management adoption, beginning with the Americas. This region exhibits pronounced interest in cloud-first deployments and advanced security integrations, fueled by stringent data privacy regulations and a mature technology ecosystem. North American enterprises often serve as early adopters of AI-driven threat analytics and zero trust frameworks, setting benchmarks that reverberate across Latin America as organizations there pursue digital transformation and regulatory alignment.
Across Europe, the Middle East, and Africa, UEM strategies are heavily influenced by local compliance regimes and geopolitical considerations. The General Data Protection Regulation has elevated data residency concerns, prompting some enterprises to opt for on-premises or sovereign cloud implementations. In parallel, the Middle East and Africa region is witnessing rapid growth in managed service adoption as regional service providers expand their portfolios to meet demand. Meanwhile, Asia-Pacific presents a dynamic landscape of both established and emerging markets. Advanced economies like Japan and Australia are focused on integrated security suites and automation, while nations such as India and Southeast Asian countries are driving adoption through cloud-based, cost-effective UEM solutions tailored to large-scale deployments
This comprehensive research report examines key regions that drive the evolution of the Unified Endpoint Management market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Strategic Moves and Differentiators of Key Players Steering Innovation and Competition in the UEM Space
In the competitive arena of Unified Endpoint Management, leading technology firms are differentiating through strategic acquisitions, deepened security integrations, and AI-driven feature enhancements. One segment of the market is elevating endpoint security by integrating advanced threat intelligence platforms that enable proactive detection and response. Another set of vendors is reinforcing identity and access management capabilities to offer seamless single sign-on and multifactor authentication experiences, reducing friction for end users while boosting security.
Innovation is also manifest in the consolidation of management consoles, where some providers are unifying disparate modules into cohesive platforms that span desktop, mobile, and IoT. Key players are forging partnerships with cloud providers to optimize performance and scalability, while others are investing heavily in user experience design, acknowledging that administration simplicity can be a compelling differentiator. Collectively, these strategic moves underscore a market in flux, where comprehensive feature sets and service excellence determine competitive positioning
This comprehensive research report delivers an in-depth overview of the principal market players in the Unified Endpoint Management market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- 42Gears Mobility Systems Pvt Ltd
- BlackBerry Limited
- Broadcom Inc
- Cisco Systems Inc
- Citrix Systems Inc
- CrowdStrike, Inc.
- Dell Technologies
- ESET
- HCL Technologies
- Hexnode
- IBM Corporation
- Ivanti Inc
- Jamf Software LLC
- Kaspersky Lab
- Matrix42 AG
- Microsoft Corporation
- Miradore
- NinjaOne LLC
- Palo Alto Networks
- Quest Software Inc
- Scalefusion
- Snow Software
- Sophos Ltd
- SOTI Inc
- Zoho Corporation Pvt Ltd
Translating UEM Trends into Actionable Recommendations to Elevate Security Posture and Operational Agility for Enterprise Leaders
To translate emerging Unified Endpoint Management trends into actionable strategies, enterprise leaders should first adopt a zero trust mindset by integrating continuous authentication and least-privilege access controls. This foundational step will tighten security at every point of interaction, reducing the risk of lateral movement and data exfiltration. Next, organizations must invest in AI-enabled analytics that surface behavioral anomalies and automate routine remediation tasks, freeing security teams to focus on strategic initiatives rather than manual workflows.
Furthermore, aligning UEM deployments with cloud-native architectures will unlock greater scalability and reduce maintenance overhead, particularly for distributed workforces. Leaders should also prioritize cross-functional collaboration between IT, security, and business units to ensure that endpoint policies align with broader operational goals and compliance mandates. Finally, regular reviews of device procurement strategies-factoring in tariff impacts, total cost of ownership, and sustainability considerations-will help organizations maintain control over their hardware estates and anticipate supply chain disruptions
Detailing a Robust Research Methodology Embracing Qualitative Analysis, Expert Interviews, and Industry Data to Ensure Comprehensive UEM Insights
This research report is underpinned by a rigorous methodology that combines qualitative and quantitative techniques to ensure comprehensive coverage of the Unified Endpoint Management domain. Primary data was collected through in-depth interviews with senior IT and security executives across diverse industries, supplemented by expert panels that validated emerging trends and vendor capabilities. Secondary research involved a detailed review of regulatory frameworks, technology white papers, and industry analyst commentary to contextualize market drivers and barriers.
To enhance the robustness of our findings, data triangulation was employed, integrating vendor documentation, independent case studies, and real-world deployment scenarios. This multi-dimensional approach enabled the distillation of critical success factors and pain points, providing readers with a holistic view of the UEM landscape. Throughout the process, rigorous quality checks and peer reviews ensured that insights are both accurate and actionable, setting a new benchmark for market intelligence in endpoint management
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Unified Endpoint Management market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Unified Endpoint Management Market, by Component
- Unified Endpoint Management Market, by Deployment Mode
- Unified Endpoint Management Market, by Organization Size
- Unified Endpoint Management Market, by Industry Vertical
- Unified Endpoint Management Market, by Device Type
- Unified Endpoint Management Market, by Region
- Unified Endpoint Management Market, by Group
- Unified Endpoint Management Market, by Country
- United States Unified Endpoint Management Market
- China Unified Endpoint Management Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1272 ]
Concluding Critical Perspectives on the Future Trajectory of Unified Endpoint Management Amid Evolving Security and Operational Demands
As organizations grapple with an increasingly complex device landscape and evolving threat environment, Unified Endpoint Management stands out as a strategic enabler of security, efficiency, and user satisfaction. The convergence of services and solutions into unified platforms, coupled with advancements in AI and zero trust, has reshaped the competitive landscape and raised the bar for performance. Regional nuances further underscore the importance of tailored approaches, while industry-specific requirements highlight the need for flexibility and integration expertise.
Ultimately, the journey toward endpoint excellence is ongoing. Decision-makers who embrace the insights contained in this report will be equipped to navigate tariffs, supply chain challenges, and regulatory complexities, ensuring that their UEM strategies deliver sustained value. By adopting the recommendations herein, enterprises can not only safeguard their device ecosystems but also drive innovation, support hybrid work models, and maintain a resilient security posture well into the future
Take the Next Step toward Unified Endpoint Management Excellence by Engaging with Ketan Rohom to Access the Comprehensive Market Research Report
The path to unlocking the strategic value of Unified Endpoint Management begins with a single, decisive step: engaging with Ketan Rohom to acquire the definitive market research report. With a deep understanding of security imperatives, deployment intricacies, and emerging industry dynamics, Ketan Rohom (Associate Director, Sales & Marketing at 360iResearch) stands ready to guide you through the complex landscape. By obtaining this comprehensive analysis, organizations will gain critical insights into segmentation opportunities, regional trends, and vendor strategies, empowering teams to make data-driven decisions and secure their device ecosystems with confidence. Reach out today to secure your edge in endpoint management excellence and propel your enterprise toward a future of heightened security and operational efficiency

- How big is the Unified Endpoint Management Market?
- What is the Unified Endpoint Management Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




