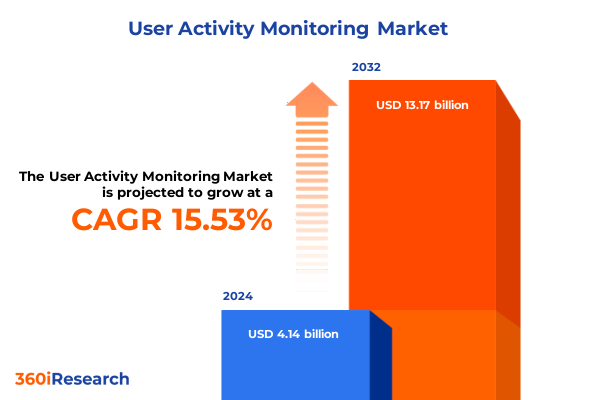
The User Activity Monitoring Market size was estimated at USD 4.78 billion in 2025 and expected to reach USD 5.53 billion in 2026, at a CAGR of 15.55% to reach USD 13.17 billion by 2032.
Introducing the strategic foundations and pivotal drivers shaping the modern cybersecurity market’s evolution and framing enterprise protection priorities
In today’s digital economy, the cybersecurity market stands at a pivotal crossroads where evolving threat vectors and enterprise resilience objectives intersect. Organizations are under pressure to protect sensitive data, maintain continuous operations, and uphold stringent regulatory requirements. High-profile breaches have intensified executive awareness, driving cybersecurity from a commoditized IT function to a boardroom imperative. Against this backdrop, enterprises are reprioritizing investments to close gaps in data loss prevention and endpoint security, while weaving real-time threat detection into overarching IT strategies.
Amid these rising stakes, holistic platforms that unify security information and event management with user behavior analytics are gaining traction as methods to transcend siloed defenses. This shift is fueled by a confluence of factors: the proliferation of remote and hybrid work models, the migration of critical workloads to multi-cloud environments, and the increasing sophistication of nation-state and financially motivated threat actors. Consequently, decision-makers are recalibrating roadmaps to integrate adaptive security architectures, aligning operational imperatives with the need for seamless compliance and rapid incident response. These strategic foundations set the stage for the deeper market dynamics explored in the following sections.
Examining fundamental shifts in threat landscapes technology advancements and regulatory pressures elevating cybersecurity solutions to a new frontier
The cybersecurity landscape is being reshaped by a series of transformative shifts that extend well beyond traditional perimeter defenses. Artificial intelligence and machine learning capabilities are now central to threat hunting and anomaly detection, enabling predictive insights that preempt breaches. Simultaneously, the escalation of cloud-native threats has propelled innovations in cloud workload protection and secure access service edge solutions. These technological advancements are mirrored by an intensified regulatory environment, where frameworks like CMMC in the defense sector and updated data privacy mandates in healthcare are redefining compliance thresholds.
Moreover, the rise of zero trust architectures underscores a paradigm where implicit trust is replaced by continuous verification, paving the way for microsegmentation and identity-centric controls. As organizations embrace DevSecOps, security is being woven into the software development lifecycle, accelerating time to market without sacrificing risk management. The convergence of these factors illustrates a dual trajectory: while threat actors evolve in complexity, security strategies are simultaneously becoming more agile, data-driven, and integrated. This interplay of innovation and adversary advancement is crafting a new frontier in cybersecurity solutions.
Assessing the combined repercussions of newly implemented United States import tariffs in 2025 on supply chains technology partnerships and cost structures
The introduction of elevated United States tariffs on technology imports in 2025 has generated reverberations across global supply chains, compelling cybersecurity vendors to reexamine sourcing and cost structures. Hardware components for network security appliances and secure access gateways have experienced pricing pressures, which in turn have prompted providers to adjust service-level agreements and reevaluate vendor partnerships. These cost escalations are most pronounced in appliance-based endpoint protection and on-premises security information and event management systems, where economies of scale are less adaptable to sudden tariff adjustments.
In response, a growing number of firms are pivoting toward cloud-based models, leveraging subscription services and software-as-a-service offerings to circumvent upfront capital expenditures on hardware subject to tariffs. This shift has accelerated cloud adoption, particularly among organizations seeking to maintain budgetary predictability and reduce operational overhead. Additionally, strategic alliances with domestic component manufacturers and localized data center deployments have emerged as risk mitigation tactics against further geopolitical volatility. As a result, the cybersecurity market is witnessing a rebalancing of cost versus control considerations, where enterprises must weigh tariff-induced cost rises against the benefits of on-site infrastructure and sovereignty over critical security functions.
Unveiling segmentation perspectives across solution type deployment mode organization size industry vertical and end user demands shaping cybersecurity adoption
Segmentation based on solution type reveals that data loss prevention technologies have moved to the forefront as executives grapple with insider threats and intellectual property protection. Endpoint security maintains broad adoption through advanced threat detection capabilities, yet next-generation systems that fuse security information and event management with user behavior analytics are rapidly gaining traction for their contextualized, proactive alerting.
Within deployment modes, cloud-based solutions dominate due to their rapid scalability and minimized need for upfront capital outlay. Hybrid architectures are emerging as a preferred compromise, allowing enterprises to maintain critical workloads on-premises while extending elastic security functions to public clouds. Nonetheless, on-premises systems remain relevant for highly regulated environments that demand granular control over data residency and infrastructure.
When considering organization size, large enterprises favor integrated platforms with centralized management and orchestration capabilities to secure extensive and disparate environments. Medium enterprises gravitate toward managed security services that balance advanced features with cost-effective resource allocation, whereas small enterprises emphasize ease of deployment and the ability to integrate point solutions rapidly.
Vertical segmentation underscores the continued leadership of banking, insurance, and securities within the broader BFSI sector, driven by stringent compliance requirements and mandate-driven investments. Government entities are prioritizing critical infrastructure protection, healthcare is accelerating cybersecurity modernization to secure patient data, while IT and telecom providers are embedding security into network and service offerings. Manufacturing firms focus on safeguarding operational technology environments, and retail organizations are reinforcing point-of-sale and e-commerce protections.
End users across compliance teams demand integrated reporting and audit-ready capabilities to satisfy regulatory bodies. Consultants play a pivotal role in advising on solution architecture and execution roadmaps. IT teams require real-time monitoring tools to maintain uptime and operational resilience. Risk management functions focus on quantifiable analytics to inform board-level strategies, and security analysts seek advanced threat intelligence and automated response mechanisms to accelerate incident resolution.
This comprehensive research report categorizes the User Activity Monitoring market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Solution Type
- Vertical
- End User
- Organization Size
- Deployment Mode
Revealing regional intelligence encompassing the Americas Europe Middle East Africa and Asia Pacific markets guiding tailored cybersecurity strategies
In the Americas, the United States continues to set the pace for cybersecurity investment, with robust budgets directed toward cloud-native detection and extended XDR platforms. Canada and select Latin American markets are demonstrating accelerated growth as enterprises modernize legacy systems and align with North American supply chain standards. The regional focus on public sector modernization is also spurring demand for managed security and compliance-centric offerings.
Across Europe, the Middle East, and Africa, stringent data protection regulations such as the GDPR and newly enacted Middle East data residency laws are the principal drivers of adoption. Western European nations are investing in advanced threat intelligence sharing initiatives, while Middle Eastern smart city projects are integrating security by design into critical infrastructure deployments. African markets are increasingly reliant on cloud-first security strategies to overcome on-premises infrastructure gaps and resource constraints.
In Asia-Pacific, digital transformation agendas in China and India are catalyzing investments in AI-powered threat detection and cloud security posture management. Government-led mandates for data localization are shaping solution architectures, leading to a rise in domestic security service providers. Australia’s stringent privacy legislation is propelling enterprise-grade encryption and identity management solutions, creating a diverse and dynamic regional market.
This comprehensive research report examines key regions that drive the evolution of the User Activity Monitoring market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Diving into leading industry players innovation initiatives partnerships and competitive positioning within the global cybersecurity ecosystem
Leading cybersecurity vendors remain focused on expanding their portfolios through both organic innovation and strategic acquisitions. Market frontrunners are investing heavily in AI and machine learning integrations, embedding autonomous response capabilities into existing platforms to reduce mean time to remediation. Partnerships between network infrastructure providers and cloud-native security specialists are delivering unified offerings that simplify procurement and operational management. Additionally, the competitive landscape is witnessing the emergence of specialized innovators targeting niche use cases such as industrial control system protection and privacy-centric analytics.
Across the board, established players are leveraging their global footprints to deliver localized threat intelligence and managed detection services, addressing region-specific compliance and geopolitical risk factors. Several firms have announced dedicated industry practice groups, aligning product roadmaps with regulatory milestones in sectors from healthcare to critical infrastructure. Collaboration between security vendors and major cloud hyperscalers is also deepening, resulting in co-developed services optimized for platform-native deployment and interoperability.
This comprehensive research report delivers an in-depth overview of the principal market players in the User Activity Monitoring market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- ActivTrak
- CrowdStrike, Inc.
- CyberArk Software Ltd.
- Deep Software Inc.
- E-SPIN Group of Companies
- Ekran System Inc.
- Forcepoint LLC
- HEYCE Technologies FZCO
- Imperva, Inc.
- Kriptone Solutions LLP
- Micro Focus International PLC
- ObserveIT by Proofpoint, Inc.
- Palo Alto Networks, Inc.
- Rapid7 LLC
- Salesforce, Inc.
- Securonix, Inc.
- SolarWinds Worldwide, LLC
- Splunk Inc.
- Sumo Logic, Inc.
- SysKit Ltd.
- Teramind Inc.
- TSFactory LLC
- Veriato Inc.
- VMware, Inc.
Empowering executive decision makers with strategic recommendations to foster resilience drive innovation and enhance operational security efficacy
To navigate the complex cybersecurity environment, organizations should prioritize an AI-driven security operations model that integrates advanced analytics with automated playbooks to curtail incident response cycles. Embracing a zero trust framework will fortify perimeter-less environments by enforcing continuous identity verification and microsegmentation, thereby containing lateral movement of adversaries. It is equally critical to rationalize vendor portfolios by consolidating overlapping tools and selecting platforms that deliver unified event correlation and orchestration capabilities.
Cross-functional alignment between IT, compliance, and risk management teams will accelerate the integration of security requirements into business processes, ensuring that investments directly support organizational objectives. Leaders are advised to invest in cybersecurity skills development programs, equipping personnel with cloud security, threat hunting, and incident response expertise. Finally, adopting a continuous improvement mindset through regular tabletop exercises and red-team assessments will uncover latent vulnerabilities and validate the effectiveness of controls under simulated adversarial conditions.
Detailing the comprehensive research methodology blending primary interviews secondary data sources and rigorous validation processes ensuring reliable findings
This research synthesizes insights from an extensive primary research effort, comprising in-depth interviews with cybersecurity executives, end users, industry consultants, and regulatory specialists. These interviews were complemented by a rigorous secondary research phase, where corporate financial filings, white papers, trade publications, and government regulations were systematically reviewed to validate emerging trends and market dynamics.
Data triangulation ensured that the findings reflect both quantitative metrics and qualitative perspectives, with proprietary databases cross-referenced against public domain sources. All information was subjected to a multi-layered validation process, including data cleaning protocols, logical consistency checks, and expert review panels. This methodology guarantees that the analysis is grounded in the most reliable and up-to-date evidence, furnishing stakeholders with an authoritative foundation for strategic decision making.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our User Activity Monitoring market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- User Activity Monitoring Market, by Solution Type
- User Activity Monitoring Market, by Vertical
- User Activity Monitoring Market, by End User
- User Activity Monitoring Market, by Organization Size
- User Activity Monitoring Market, by Deployment Mode
- User Activity Monitoring Market, by Region
- User Activity Monitoring Market, by Group
- User Activity Monitoring Market, by Country
- United States User Activity Monitoring Market
- China User Activity Monitoring Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1113 ]
Summarizing strategic insights actionable outcomes and future considerations to guide stakeholders through evolving cybersecurity challenges and opportunities
The cybersecurity market is undergoing rapid transformation, driven by shifts in threat sophistication, regulatory complexity, and technological innovation. Organizations that proactively embrace adaptive architectures-integrating AI-driven detection, zero trust principles, and cloud-native services-are poised to outpace adversaries and maintain resilient operations. Segmentation analyses underscore the necessity of tailoring strategies to solution requirements, deployment preferences, organization size, vertical-specific regulations, and end user workflows. Regionally, the balance between global best practices and local compliance imperatives shapes divergent adoption patterns across the Americas, EMEA, and Asia-Pacific.
As leading vendors evolve through synergy-based partnerships and targeted product developments, competition will center on the ability to deliver seamless, interoperable security experiences. The recommended course of action for industry leaders is to streamline toolsets, align security investments with business objectives, and foster a culture of continuous vigilance. By grounding their strategies in robust research insights and engaging in proactive risk management, stakeholders can confidently navigate the complexities ahead and capitalize on emerging opportunities.
Engage directly with Associate Director of Sales and Marketing Ketan Rohom to secure the cybersecurity market research report for informed decision making
To secure full access to detailed market intelligence including in-depth analysis of segment breakdowns and region-specific trends, reach out to Associate Director of Sales and Marketing Ketan Rohom. Ketan can arrange a personalized briefing to highlight how the insights map to your strategic objectives and ensure you gain the actionable guidance needed to navigate evolving cybersecurity challenges. Engage today to elevate your competitive positioning and safeguard your organization’s digital assets with confidence.

- How big is the User Activity Monitoring Market?
- What is the User Activity Monitoring Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




