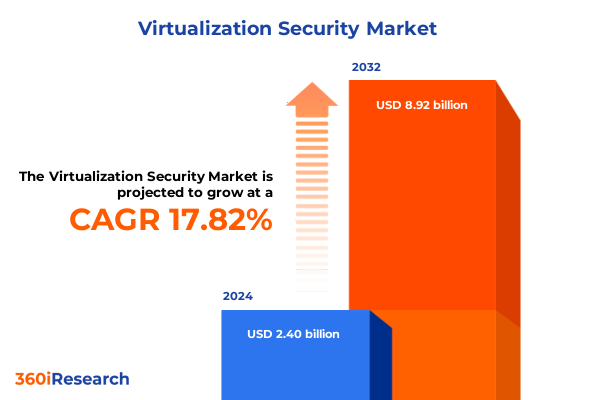
The Virtualization Security Market size was estimated at USD 2.82 billion in 2025 and expected to reach USD 3.32 billion in 2026, at a CAGR of 17.84% to reach USD 8.92 billion by 2032.
Exploring the Critical Role of Virtualization Security in Safeguarding Modern IT Infrastructures Against Evolving Threat Landscapes
The rapid proliferation of virtualization across enterprise IT environments has fundamentally transformed how organizations deploy, scale, and manage critical workloads. As virtual machines, containers, and hyperconverged infrastructures become central to modern data centers and cloud architectures, the security paradigm must evolve to address the unique risks introduced by abstraction layers. Hypervisor exploits, lateral movement within virtual networks, and insecure orchestration tools can expose sensitive assets unless countermeasures are specifically designed for virtual environments.
Moreover, the convergence of virtualization with cloud-native services and edge computing orchestrations has blurred traditional network perimeters, demanding an integrated approach that combines micro-segmentation, workload integrity verification, and real-time monitoring. Security architects now prioritize isolating workloads, applying policy-driven controls, and leveraging behavior analytics to detect anomalies that evade conventional defenses. Efficiency and agility no longer come at the expense of resilience when organizations adopt virtualization-aware security frameworks.
Accordingly, this executive summary introduces the critical aspects of virtualization security, mapping out transformative shifts, tariff influences, segmentation insights, regional dynamics, and competitive landscapes. Each section equips decision-makers with evidence-backed perspectives on how to optimize defenses, navigate supply chain headwinds, and harness innovation to maintain robust protection for virtualized workloads.
Navigating the Transformative Shifts in Virtualization Security Fueled by Innovations in Cloud Computing, Edge Environments and Regulatory Evolution
The virtualization security landscape is undergoing transformative shifts driven by the integration of cloud computing, edge deployments, and regulatory evolution. Cloud service providers continuously enhance native security controls, embedding micro-segmentation, secure boot, and encrypted vSwitch technologies into their platforms. At the edge, constrained environments require lightweight agents and distributed policy enforcement to secure IoT and critical infrastructure workloads beyond centralized data centers.
Regulatory initiatives around data sovereignty and privacy have further propelled the adoption of encryption-first architectures and granular audit capabilities in virtualized settings. Organizations must align security strategies with emerging standards such as zero trust and confidential computing, which mandate continuous verification of workload integrity and strict isolation of privileged operations. This shift necessitates collaboration between security operations and platform engineering teams to embed controls throughout the development lifecycle.
These converging forces are catalyzing a move toward unified visibility across hybrid environments, where virtual and containerized workloads coexist. As a result, virtualization security solutions are evolving into comprehensive platforms that blend policy orchestration, threat intelligence integration, and automated response mechanisms. This section delves into the key drivers reshaping how enterprises secure virtual assets and prepare for next-generation architectures.
Assessing the Cumulative Impact of United States Tariffs in 2025 on Virtualization Security Costs, Supply Chains and Technology Adoption Dynamics
United States tariff policies in 2025 have had a cumulative impact on virtualization security by influencing hardware costs, supply chain resilience, and technology adoption. New levies imposed on imported server components and specialized processors have increased acquisition and refresh expenses, prompting organizations to extend lifecycle management and defer upgrades. This dynamic has underscored the importance of software-based defenses that can be deployed on heterogeneous hardware without compromising performance or security.
Tariffs have also driven technology leaders to diversify manufacturing footprints and source critical components from alternative regions. By shifting production to tariff-exempt zones, vendors can maintain competitive pricing and supply continuity, albeit with transitional complexities in logistics and quality control. These changes highlight the interdependence between fiscal policy and virtualization security preparedness, emphasizing the need for proactive scenario planning and agile procurement strategies.
Consequently, enterprises are recalibrating investment toward virtualization-agnostic security software and managed services that can be quickly scaled across existing infrastructures. Such services offer continuous monitoring, policy updates, and threat intelligence feeds without requiring extensive hardware refreshes. This approach mitigates the direct cost pressures of tariffs while ensuring that security controls remain robust and consistently enforced across virtual environments.
Unveiling Key Segmentation Insights to Illuminate How Component, Security Type, Deployment Mode and Industry Verticals Drive Virtualization Security Strategies
A nuanced understanding of market segments reveals how distinct technology components and service offerings drive virtualization security strategies. The ecosystem spans software solutions-ranging from hypervisor extensions to orchestration-level policy engines-and services that encompass both managed offerings and professional consulting engagements. Managed services provide continuous oversight, threat hunting, and incident response, whereas professional services focus on architecture design, compliance audits, and deployment accelerations tailored to virtualization platforms.
Detailing the security types further illuminates prioritization within organizations. Data protection efforts extend from robust backup and recovery workflows to advanced data masking and encryption schemes, ensuring that virtual workloads maintain integrity and confidentiality. Host security enforces hardening measures at the hypervisor and operating system levels to thwart lateral movement, while identity and access management solutions-encompassing multi-factor authentication, privileged access controls, and single sign-on-regulate administrative and user interactions. Network security applies segmentation and micro-segmentation controls to isolate workloads and contain breaches in distributed virtual topologies.
Deployment models-whether on-premises, in public clouds, or via hybrid architectures-shape how these controls are implemented and managed. Each end-user industry brings its own risk profile and compliance requirements, from the regulated data environments of financial institutions and healthcare providers to the high-velocity networks in telecommunications and retail. By aligning capabilities with sector-specific needs, stakeholders can ensure that virtualization security investments deliver optimal protection and operational efficiency.
This comprehensive research report categorizes the Virtualization Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Security Type
- Deployment Type
- End User Industry
Revealing Key Regional Insights Highlighting How Markets in the Americas, Europe Middle East & Africa and Asia Pacific Shape Virtualization Security Trajectories
Regional dynamics play a pivotal role in shaping how virtualization security capabilities are adopted and implemented. In the Americas, enterprises leverage mature cloud ecosystems and advanced threat intelligence frameworks, often prioritizing rapid scalability and centralized management. This focus stimulates demand for cloud-native security controls and automated orchestration tools that integrate with leading hyperscale platforms, while compliance mandates around data privacy reinforce encryption and micro-segmentation strategies.
Across Europe, the Middle East, and Africa, regulatory complexity and diverse infrastructure maturity levels necessitate flexible security frameworks. Organizations navigate stringent data residency regulations alongside varied risk landscapes, prompting a hybrid approach where on-premises and regional cloud deployments coexist. This mosaic of requirements fosters partnerships between local managed security providers and global technology vendors to deliver tailored virtualization security solutions.
In the Asia-Pacific region, rapid digital transformation and increased modernization efforts have accelerated virtualization adoption in both public and private sectors. To address heterogeneous network environments and emerging threat vectors, security teams emphasize lightweight endpoint agents, container-native defenses, and unified management across geographically dispersed sites. Collaboration between regional data centers and multinational IT service providers ensures that virtualization security architectures remain both resilient and compliant.
Understanding these regional distinctions is essential for technology leaders seeking to align product roadmaps and service models with localized demands, regulatory frameworks, and infrastructure capabilities.
This comprehensive research report examines key regions that drive the evolution of the Virtualization Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Examining the Strategic Movements and Competitive Positioning of Leading Technology Providers Shaping the Virtualization Security Ecosystem Today
Leading technology providers have taken diverse strategic approaches to secure their positions within the virtualization security ecosystem. Major players offer integrated platforms that combine hypervisor-level defenses, behavioral analytics, and centralized policy orchestration, ensuring consistent protection across public, private, and hybrid environments. These vendors have expanded their portfolios through targeted acquisitions, bolstering capabilities in zero-trust network access and confidential computing to address emerging demands.
Some innovators specialize in container and micro-segmentation security, delivering API-driven controls that integrate seamlessly with DevOps pipelines. By embedding security at the application layer, they enable rapid iteration without sacrificing comprehensive threat visibility. Others focus on identity-centric models, unifying privileged access management, multi-factor authentication, and single sign-on to fortify administrative controls over virtual infrastructure. Service-oriented providers complement these solutions with managed detection and response offerings, leveraging global threat intelligence networks to anticipate and counteract advanced adversaries.
Competitive differentiation often hinges on deep partnerships with hyperscale cloud operators and hardware manufacturers. By collaborating on secure boot processes, firmware attestation, and hardware-rooted trust anchors, these alliances yield solutions that mitigate risks at every layer of the stack. Understanding how leading companies align go-to-market strategies with technology roadmaps provides critical insight for stakeholders evaluating vendors in a crowded and rapidly evolving market.
This comprehensive research report delivers an in-depth overview of the principal market players in the Virtualization Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Bitdefender LLC
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Citrix Systems Inc.
- Fortinet, Inc.
- IBM Corporation
- Juniper Networks Inc.
- Kaspersky Lab
- McAfee, LLC
- Nutanix Inc.
- Palo Alto Networks, Inc.
- Red Hat Inc.
- Sangfor Technologies Inc.
- Sophos Group plc
- Tenable Holdings Inc.
- Trend Micro Incorporated
- VMware, Inc.
Crafting Actionable Recommendations for Industry Leaders to Enhance Virtualization Security Posture Through Innovation, Collaboration and Policy Alignment
Industry leaders must adopt a multi-faceted approach to reinforce virtualization security while fostering innovation. First, embedding policy orchestration directly into virtualization platforms ensures that security controls keep pace with dynamic workload provisioning. By automating micro-segmentation and leveraging infrastructure as code, organizations can reduce misconfigurations and accelerate response times during incident investigations.
Second, investing in comprehensive identity governance frameworks is essential to manage privileged access across virtual assets. Integrating multi-factor authentication, single sign-on, and privileged access management within orchestrator consoles creates an end-to-end security fabric that prevents unauthorized lateral movement. Such identity-centric controls also support compliance with stringent data protection regulations by providing granular audit trails.
Third, collaboration between security and operations teams can bridge the gap between policy development and enforcement. Establishing cross-functional councils and shared metrics promotes a culture of shared responsibility, ensuring security is embedded in every stage of the deployment lifecycle. Finally, aligning vendor selection with roadmap priorities-such as confidential computing and zero trust-will future-proof defenses against emerging threats. By following these recommendations, decision-makers can establish resilient virtualization security postures that balance agility and robust protection.
Detailing a Rigorous Research Methodology Incorporating Primary Interviews, Secondary Data Triangulation and Validation for Comprehensive Analysis
This analysis is underpinned by a rigorous research methodology that combines primary insights with comprehensive secondary validation. Primary data was collected through in-depth interviews with C-level executives, security architects, and solution providers actively engaged in virtualization deployments. These conversations elucidated firsthand challenges around hypervisor exploits, orchestration vulnerabilities, and emerging regulatory drivers.
Secondary research encompassed a wide range of credible sources, including publicly available technical whitepapers, government policy announcements, and vendor documentation. Data triangulation was applied to reconcile findings across proprietary reports, academic publications, and industry forums, ensuring a balanced perspective free from vendor bias. Quantitative data points were verified against multiple independent references to confirm accuracy.
The research was further validated through expert panel discussions and peer reviews, where assumptions and emerging themes were challenged and refined. This iterative validation process resulted in a comprehensive framework that captures the current state of virtualization security, future trajectories, and actionable strategies. By adhering to these methodological principles, the report delivers authoritative insights with high confidence in relevance and reliability.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Virtualization Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Virtualization Security Market, by Component
- Virtualization Security Market, by Security Type
- Virtualization Security Market, by Deployment Type
- Virtualization Security Market, by End User Industry
- Virtualization Security Market, by Region
- Virtualization Security Market, by Group
- Virtualization Security Market, by Country
- United States Virtualization Security Market
- China Virtualization Security Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1272 ]
Concluding Reflections on Elevating Virtualization Security Paradigms to Address Emerging Threats and Support Resilient Digital Transformation Objectives
In closing, virtualization security represents a critical pillar for organizations pursuing digital transformation and cloud modernization. As threat actors evolve tactics to exploit abstraction layers and blurred perimeters, robust controls-spanning micro-segmentation, identity governance, and workload integrity verification-are no longer optional. The interplay between policy decisions such as tariffs, regional regulatory landscapes, and market segmentation underscores the complexity of securing virtual infrastructures.
By synthesizing insights on transformative shifts, tariff impacts, segmentation drivers, and competitive dynamics, decision-makers gain a holistic view of how to architect resilient environments. Collaboration between security and operations, coupled with strategic vendor partnerships, will accelerate the adoption of next-generation frameworks such as zero trust and confidential computing. Ultimately, organizations that proactively integrate virtualization-specific defenses into their broader security ecosystems will achieve sustained resilience and competitive advantage in an ever-more dynamic threat landscape.
Engage with Ketan Rohom to Discover How Our Comprehensive Virtualization Security Research Can Empower Your Strategic Decision Making and Drive Business Growth
To secure a decisive advantage in virtualization security and gain unparalleled insight into emerging trends, connect with Ketan Rohom. With deep expertise as an Associate Director of Sales & Marketing, he can guide your organization through tailored strategic discussions, covering everything from advanced threat mitigation to robust compliance strategies. Engaging directly will reveal how comprehensive market intelligence can inform roadmap planning, investment prioritization, and risk management frameworks that align with broader digital transformation goals. Elevate your security posture with a solution set shaped by rigorous research and expert validation. Reach out today to schedule a personalized briefing and explore options for licensing the full report, equipping your team with actionable intelligence that drives sustained growth and resilience in an increasingly complex virtualization landscape.

- How big is the Virtualization Security Market?
- What is the Virtualization Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




