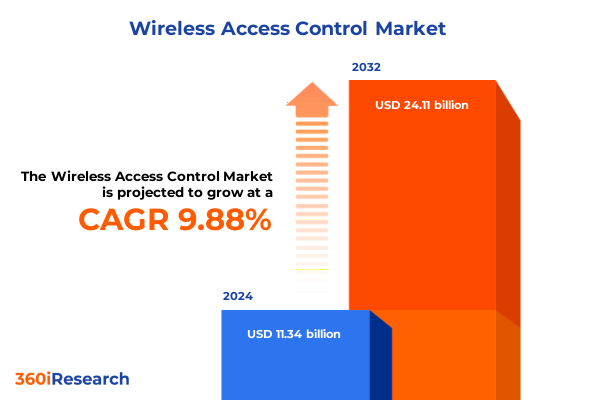
The Wireless Access Control Market size was estimated at USD 12.33 billion in 2025 and expected to reach USD 13.42 billion in 2026, at a CAGR of 10.04% to reach USD 24.11 billion by 2032.
Unlocking the Future of Secure Entry: An Overview of Wireless Access Control Market Dynamics and Strategic Imperatives and Emerging Opportunities
The transition from traditional mechanical locks to advanced wireless access control systems marks a pivotal shift in how organizations safeguard assets and manage entry points. As digital transformation accelerates across industries, the need for flexible, scalable security solutions becomes increasingly paramount. Wireless access control leverages radio frequency, mobile credentials, and cloud connectivity to deliver seamless entry management, reducing dependency on physical keys and localized infrastructure. This evolution not only enhances user convenience but also strengthens overall security posture by centralizing control and enabling real-time monitoring from any location.
Stakeholders across sectors are drawn to wireless access control for its ability to integrate with broader building management and IoT ecosystems. Whether revitalizing legacy systems in corporate campuses or deploying secure entry mechanisms in distributed facilities, decision-makers recognize that wireless solutions minimize installation complexity and lower the total cost of ownership. Enterprise teams can administer user permissions remotely, revoke credentials instantly, and generate audit trails for compliance purposes, all without labor-intensive on-site visits. Consequently, the convergence of convenience and compliance drives unprecedented adoption rates.
Momentum in the wireless access control market is fueled by technological advancements in cloud computing, mobile credentialing, and edge processing. Organizations confronting heightened cybersecurity threats and stringent regulatory mandates seek robust authentication mechanisms to ensure the integrity of secure environments. Additionally, the proliferation of connected devices in smart buildings underscores the importance of interoperable security platforms that communicate seamlessly while preserving data privacy and resilience against cyberattacks.
Nonetheless, deploying wireless access control systems requires careful navigation of interoperability challenges, legacy integration complexities, and evolving data protection standards. Budgetary constraints and concerns over network reliability can slow procurement cycles, prompting providers to offer scalable models that support phased rollouts. As such, stakeholders must align strategic objectives with technological capabilities and risk tolerance to harness the full potential of wireless access control.
Navigating Disruption: How Technological Innovations and Next Generation Connectivity are Redefining Wireless Access Control Solutions at Scale
The landscape of wireless access control has been irreversibly reshaped by the advent of cloud platforms that deliver centralized management, zero-trust architectures, and seamless firmware updates. Security architects are increasingly prioritizing solutions that leverage machine learning algorithms to detect anomalous entry patterns, predict potential breaches, and enforce adaptive authentication protocols in real time. Simultaneously, the convergence of wireless access control with comprehensive facility management tools enables facility operators to unify security, environmental monitoring, and energy optimization within a single operational dashboard.
At the same time, the proliferation of mobile devices has driven widespread acceptance of smartphone-based credentials as a preferred authentication mechanism. With near-field communication and Bluetooth Low Energy technologies embedded in modern devices, organizations can issue digital keys that reduce dependency on physical cards and RFID tags. These credentialing innovations enhance user experience while empowering IT teams to revoke access at the push of a button, thereby mitigating risks associated with lost or stolen badges.
Moreover, the integration of 5G connectivity paves the way for low-latency, high-bandwidth communication between access control endpoints and cloud servers. This development supports use cases such as video-based authentication, where facial recognition cameras at entry points can verify identities in under a second. As the Internet of Things permeates building infrastructure, wireless door locks and readers seamlessly exchange data with environmental sensors, occupancy trackers, and emergency response systems, forging a truly intelligent security environment.
In response to the pandemic-induced demand for contactless solutions, industry players have accelerated the rollout of touchless access methods, including QR code scanning and gesture-based approvals. This trend underscores an overarching shift toward user-centric security models that balance convenience with robust risk mitigation. Altogether, these transformative shifts highlight an industry in flux-where innovation, flexibility, and resilience form the bedrock of modern wireless access control solutions.
Assessing the Ripple Effects: Comprehensive Analysis of United States 2025 Tariffs on Wireless Access Control Supply Chains and Cost Structures
In 2025, the United States implemented a new tranche of tariffs on imported electronic components often utilized in wireless access control hardware, including controllers, readers, and secure identity devices. These tariffs, targeting key manufacturing hubs abroad, have exerted upward pressure on equipment prices, compelling both vendors and end users to reassess procurement strategies. As supply costs climb, the economic calculus shifts, prompting integrators to explore alternative sourcing from tariff-exempt regions or to negotiate longer-term agreements with original equipment manufacturers.
The cumulative impact of these trade measures has revealed vulnerabilities within global supply chains. Lead times for critical hardware components have expanded, and manufacturers face higher costs for logistics and customs compliance. To mitigate disruption, several prominent access control providers are diversifying their supplier base, laying the groundwork for dual sourcing and onshore assembly initiatives. Simultaneously, system integrators are adjusting project timelines, building greater contingency into delivery schedules, and exploring modular installation approaches that allow phased hardware rollouts.
End users have seen a corresponding rise in total project costs, which in some cases has led to deferment of nonessential upgrades or migration to subscription-based models that spread expenses over time. In an effort to preserve budget flexibility, certain organizations are piloting hybrid deployments that combine locally sourced hardware with cloud-managed software licenses. This approach not only diffuses risk but also fosters a more agile upgrade cycle, enabling incremental enhancements without a large upfront capital outlay.
The industry’s collective response underscores a strategic pivot toward resilient, geographically diversified supply chains. Emerging partnerships between hardware vendors and contract manufacturers in the Americas signal a broader trend toward regionalization. Looking ahead, stakeholders must remain vigilant to evolving trade policies and adjust sourcing strategies dynamically. Through proactive risk management, the wireless access control ecosystem can adapt to tariff-induced cost pressures while continuing to innovate and meet growing security demands.
Decoding Market Nuances and Segmentation Across Components, Deployment Models, Authentication Types, Access Technologies, Application Verticals, and End Users
A nuanced understanding of market segmentation is essential for grasping the varied drivers shaping wireless access control today. By component, the ecosystem encompasses hardware offerings-such as controllers that manage door operations, locks that secure entryways, readers that authenticate credentials, and secure identity devices that embed mobile or card-based tokens-alongside services ranging from consulting and training to installation and integration, plus ongoing support and maintenance. Complementing these are software platforms, which can be delivered as cloud-native solutions or on-premise installations, each tailored to different organizational preferences around control and scalability.
Examining deployment models reveals a clear dichotomy: organizations opting for cloud deployments prize rapid scalability, simplified updates, and remote management, whereas entities embracing on-premise setups often cite data sovereignty, network independence, and tighter integration with internal IT policies as paramount. This bifurcation underscores the need for providers to deliver both turnkey cloud services and customizable on-premise frameworks that can interoperate seamlessly.
Authentication modalities themselves are evolving. Biometric methods, including facial recognition cameras at turnstiles, fingerprint scanners embedded in handheld readers, and iris recognition terminals, now coexist with traditional card-based systems such as RFID cards and smart cards. Password-based credentials remain in use for backward compatibility and low-risk environments. The diverse mix of these authentication types necessitates platforms capable of multi-factor authentication workflows and dynamic policy enforcement based on real-time threat assessments.
Access technologies further diversify the landscape, with Bluetooth and NFC enabling mobile credential transactions, RFID powering contactless card swipes, Wi-Fi supporting remote device configuration, and Zigbee facilitating mesh network communication among battery-powered locks. Each technology carries its own trade-offs in terms of range, power consumption, and network complexity, influencing solution design and deployment costs.
Applications for wireless access control span from high-traffic commercial buildings and healthcare facilities-where strict compliance and auditability are critical-to industrial sites that demand ruggedized hardware and residential communities seeking smart home integration. End users range across banking, financial services, and insurance organizations with stringent security mandates to government and defense entities requiring top-tier cryptographic authentication, retailers and e-commerce businesses aiming to streamline supply chain access, and telecom and IT firms focused on securing network operations centers. These multifaceted segmentation insights inform product roadmaps, partnership strategies, and go-to-market approaches for stakeholders across the value chain.
This comprehensive research report categorizes the Wireless Access Control market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Authentication Type
- Access Technology
- Deployment
- Application
- End User
Panoramic Overview of Regional Dynamics in Wireless Access Control with Focus on Americas, Europe Middle East and Africa, and Asia Pacific Opportunities
Regional dynamics play an instrumental role in shaping the adoption and evolution of wireless access control systems. In the Americas, the United States leads with robust investment in enterprise-grade solutions, driven by stringent regulatory environments, a mature channel of system integrators, and a pronounced shift toward cloud-managed security. Canada follows closely, placing emphasis on interoperability standards and integration with national identity programs. Latin America is witnessing gradual uptake, primarily in banking and critical infrastructure projects, though budget constraints and local compliance requirements remain deciding factors.
Across Europe, Middle East, and Africa, diverse economic landscapes fuel distinct security priorities. Western Europe sees widespread demand for GDPR-compliant identity management, with companies deploying cutting-edge mobile credentials to satisfy both security and privacy mandates. The Middle East is characterized by large-scale developments in smart city and infrastructure initiatives, where turnkey wireless access control solutions are embedded into mixed-use complexes. In Africa, nascent urbanization and growing digital transformation efforts are spurring pilot deployments, particularly within government facilities and international organizations seeking rapid, flexible security enhancements.
Asia-Pacific presents a tapestry of market maturity levels. Major economies such as China and Japan prioritize domestically developed hardware platforms, often coupled with advanced facial recognition and QR-based authentication to support high population densities. Australia and New Zealand emphasize integration with existing building management systems and focus on sustainability metrics. Emerging markets in Southeast Asia and India are accelerating investments in cloud-native access control to bridge security gaps in manufacturing hubs and technology parks, harnessing the scalability and cost-effectiveness of subscription-based models.
This geographic mosaic of regional insights highlights the need for solution providers to craft localized value propositions that address regulatory frameworks, technology preferences, and infrastructure readiness. By tailoring offerings to each region’s unique drivers and constraints, vendors can unlock new growth corridors and establish resilient market presence across the Americas, EMEA, and Asia-Pacific.
This comprehensive research report examines key regions that drive the evolution of the Wireless Access Control market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Strategic Portrait of Leading Innovators and Key Competitors Steering Wireless Access Control Solutions Through Technology Partnerships and Service Excellence
Leading providers in wireless access control are differentiating through strategic investments in cloud platforms, AI-driven analytics, and partnership ecosystems. One notable innovator has leveraged a microservices architecture to deliver real-time telemetry and predictive maintenance alerts, while another has expanded its portfolio through a high-profile acquisition of a cloud-based identity management startup. These moves illustrate a broader trend toward converged security platforms that unify physical access data with cybersecurity operations.
Similarly, several incumbents have deepened their relationships with system integrators and technology alliances to offer end-to-end managed services, enabling customers to outsource day-to-day security administration. This shift addresses talent shortages and allows organizations to tap into specialized expertise for deployment, monitoring, and incident response. At the same time, newer market entrants are courting niche segments-such as biopharma manufacturing and co-working spaces-by offering modular, plug-and-play solutions that require minimal on-site configuration.
Innovation cycles are further accelerated by partnerships between access control providers and leading IoT platform vendors, fostering interoperability among building automation, video surveillance, and environmental sensors. In parallel, some companies have launched developer-ready APIs and SDKs, empowering enterprise IT teams to tailor user interfaces and integrate access control events into custom business workflows. This trend toward open architectures underscores a collective move away from monolithic systems toward extensible ecosystems.
Finally, several top-tier players are emphasizing sustainability and lifecycle management by introducing battery-free locks, solar-powered readers, and take-back programs for end-of-life hardware. These initiatives reflect growing environmental stewardship within the security domain and address customer demands for resource efficiency. Together, these strategic maneuvers by leading companies define the competitive contours of the wireless access control market and signal where future innovation will emerge.
This comprehensive research report delivers an in-depth overview of the principal market players in the Wireless Access Control market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Ackerman Security
- ADT Inc.
- Allegion PLC
- AMAG Technology, Inc.
- Assa Abloy AB
- Axis Communications AB
- Brivo, Inc.
- Cansec Systems Ltd
- Cisco Systems, Inc.
- dormakaba Holding AG
- Eins Technologies India Pvt Ltd.
- Genetec Inc.
- Godrej & Boyce Manufacturing Company
- Honeywell International Inc.
- IDEMIA
- Identiv, Inc.
- Johnson Controls International PLC
- Lenel Systems International, Inc.
- NEC Corporation
- Nedap N.V.
- Robert Bosch GmbH
- SALTO Systems, S.L.
- Spintly
- Suprema Inc.
- Thales Group
Blueprint for Future-Proof Success in Wireless Access Control by Embracing Cloud-Native Innovation, AI-Powered Insights, and Collaborative Ecosystem Strategies
Industry leaders aiming to secure leadership in the wireless access control domain should adopt cloud-native architectures that support seamless upgrades and real-time analytics. By shifting from monolithic on-premise installations to microservices–based deployments, organizations can reduce time-to-market for feature enhancements and reinforce resilience against cyber threats. Concurrently, embedding AI-driven insights within access management platforms enables proactive anomaly detection and adaptive authentication that respond dynamically to changing risk profiles.
Collaborating with ecosystem partners is equally imperative. Establishing robust interoperability frameworks with IoT device manufacturers, video surveillance providers, and building management system vendors not only enhances solution value but also simplifies integration efforts for end users. Open APIs and standardized communication protocols ensure that organizations can integrate security data into broader operational intelligence initiatives, unlocking cross-domain efficiencies and richer situational awareness.
Moreover, aligning deployment strategies with user behavior and environment-specific requirements will yield higher adoption rates. Hybrid offerings that blend cloud and on-premise components cater to customers with stringent data privacy mandates, while flexible licensing models-including subscription-based and usage-based pricing-address budgetary constraints and promote scalability. Embedding multi-factor authentication workflows that leverage biometric modalities and mobile credentials enhances security without compromising convenience, a balance that end users increasingly demand.
Finally, forging a culture of continuous learning and compliance will bolster long-term success. Providing comprehensive training, updating policies to reflect evolving regulations, and collaborating with industry consortia on best practices will cultivate stakeholder trust. In sum, a combination of technology innovation, strategic alliances, customer-centric licensing, and robust training initiatives will empower industry leaders to chart a sustainable growth trajectory in wireless access control.
Insight into Rigorous Research Methodology Underpinning Comprehensive Analysis of Wireless Access Control Market Trends and Data Validation Techniques
The research underpinning this analysis integrates both primary and secondary data sources to ensure comprehensive coverage of wireless access control trends. Primary research consisted of one-on-one interviews and workshops with senior executives from end-user organizations, system integrators, and technology vendors. These interactions provided qualitative insights into emerging use cases, procurement barriers, and performance expectations. In parallel, a structured online survey captured quantitative data on deployment preferences, budget allocations, and satisfaction levels across diverse industries.
Complementing primary inputs, secondary research leveraged a range of publicly available materials, including regulatory filings, patent databases, academic journals, and industry white papers. This phase validated market narratives, technology roadmaps, and competitive positioning. Data from import-export records and trade databases were analyzed to quantify the effect of tariffs and supply chain shifts. Additionally, company financial reports and press releases were examined to track M&A activity, strategic partnerships, and product launches.
An iterative triangulation methodology harmonized findings from these multiple sources. Top-down sizing approaches were cross-checked against a bottom-up aggregation of segmented revenue streams to refine trend assessments. Segment definitions were aligned with industry-standard taxonomies, and all data points underwent rigorous cleansing and normalization to ensure comparability. Preliminary results were peer-reviewed by an internal panel of subject matter experts, while draft interpretations were validated through follow-up consultations with select stakeholders.
This robust research framework ensures that the insights presented are both data-driven and reflective of real-world market dynamics. Limitations related to forecast intervals, undisclosed vendor contracts, and rapidly evolving regulatory landscapes are acknowledged, with ongoing tracking mechanisms established to update findings as conditions change.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Wireless Access Control market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Wireless Access Control Market, by Component
- Wireless Access Control Market, by Authentication Type
- Wireless Access Control Market, by Access Technology
- Wireless Access Control Market, by Deployment
- Wireless Access Control Market, by Application
- Wireless Access Control Market, by End User
- Wireless Access Control Market, by Region
- Wireless Access Control Market, by Group
- Wireless Access Control Market, by Country
- United States Wireless Access Control Market
- China Wireless Access Control Market
- Competitive Landscape
- List of Figures [Total: 18]
- List of Tables [Total: 1749 ]
Synthesis of Key Findings and Strategic Perspective on the Evolution of Wireless Access Control Market Imperatives for Decision Makers
The synthesis of our research highlights a market in which technological innovation, regulatory pressures, and shifting user expectations converge to shape the future of wireless access control. Cloud adoption emerges as a pivotal driver, enabling real-time management and seamless scaling, while hybrid on-premise offerings continue to meet the needs of security-conscious organizations. The expanding array of authentication methods-from biometrics to mobile credentials-underscores the sector’s focus on balancing security with user experience.
Tariff-induced supply chain challenges in the United States have encouraged a strategic pivot toward regionalized manufacturing and diversified sourcing. Providers demonstrating adaptability in their procurement strategies stand to maintain competitive pricing and project timelines. Moreover, as partnerships across the IoT ecosystem deepen, the integration of access control with broader facility management and cybersecurity frameworks becomes both possible and operationally advantageous.
Regional insights reveal distinct adoption trajectories, with mature markets in North America and Western Europe emphasizing compliance and interoperability, while Asia-Pacific and emerging economies pursue rapid digital transformation under government-led initiatives. Leading companies are responding with modular, API-driven solutions and sustainability programs that reflect evolving customer priorities.
In conclusion, stakeholders equipped with a clear understanding of segmentation dynamics, regional variations, and tariff impacts are better positioned to navigate an environment defined by continuous innovation. By adopting the strategic recommendations outlined, decision makers can accelerate deployment timelines, optimize security outcomes, and capture sustainable value in the wireless access control market.
Take Immediate Action to Transform Access Security by Securing a Comprehensive Wireless Access Control Report with Associate Director Sales and Marketing
We invite you to engage directly with Ketan Rohom, Associate Director of Sales & Marketing, to secure your comprehensive wireless access control market research report. By partnering with Ketan, you gain exclusive access to in-depth analysis, proprietary insights, and tailored recommendations designed to empower your strategic decision-making. Connect with him to discuss how this report can address your unique challenges and reveal opportunities in an evolving security landscape. Reach out today to elevate your understanding and drive actionable growth in wireless access control technologies.

- How big is the Wireless Access Control Market?
- What is the Wireless Access Control Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




